Pinpointing the hottest PHP code paths with high CPU usage (using OpenResty XRay)
Today I will show you another step-by-step guide for analyzing PHP applications with OpenResty XRay. We’ll quickly pinpoint the hottest code paths in an already-running PHP process. These code paths might take most of the CPU time of your applications. OpenResty XRay is a truly non-intrusive dynamic analysis tool that requires no installation of any special modules or plugins in the target application, no recompilation of the target application, and even no need to restart the running processes.
Problem: high CPU usage
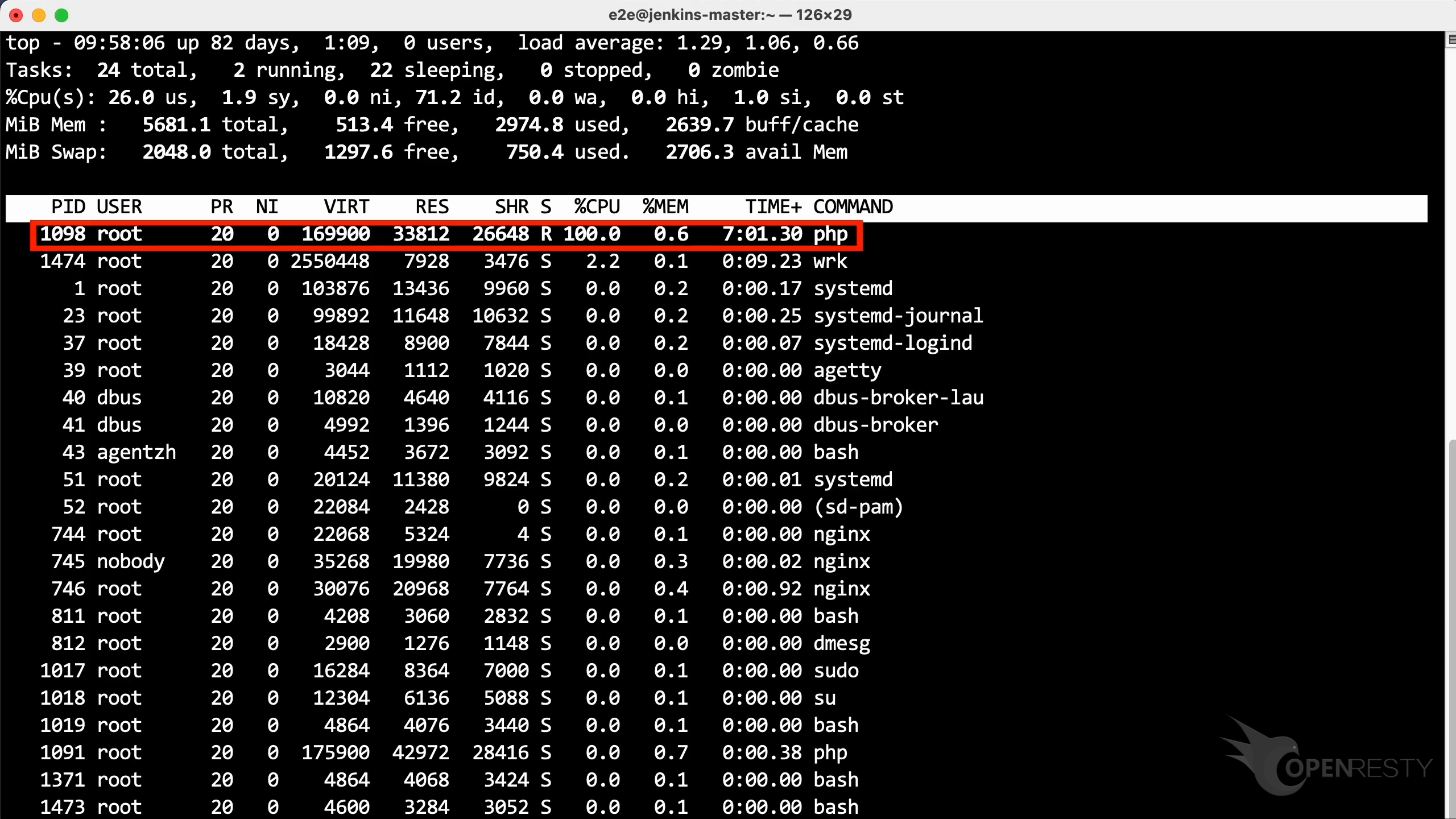
Let’s run the top command to check the CPU usage. As shown, the php process consumes 100% of CPU cores.
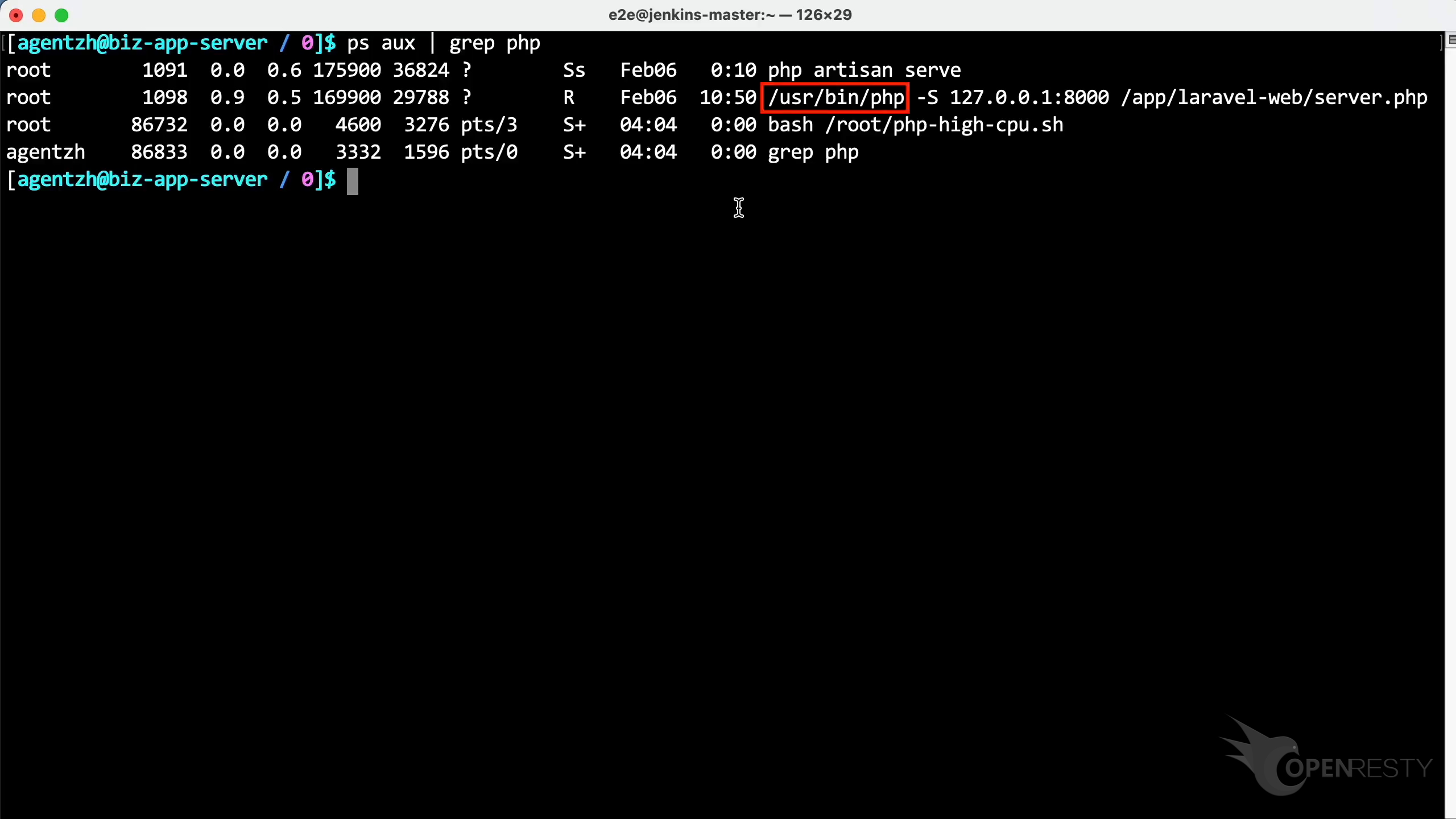
Run the ps command to see the full command line for this process. We can see it is the standard PHP binary executable shipped with the Linux distribution.
Use the guidede analysis feature of OpenResty XRay to spot the CPU-hottest PHP code paths
Let’s use OpenResty XRay to check out this unmodified process. We can analyze it in real time and figure out what’s going on.
Open the OpenResty XRay Web console in the web browser.
Make sure it is the right machine you are watching.
You can choose the right machine from the list below if the current one is incorrect.
Go to the “Guided Analysis” page.
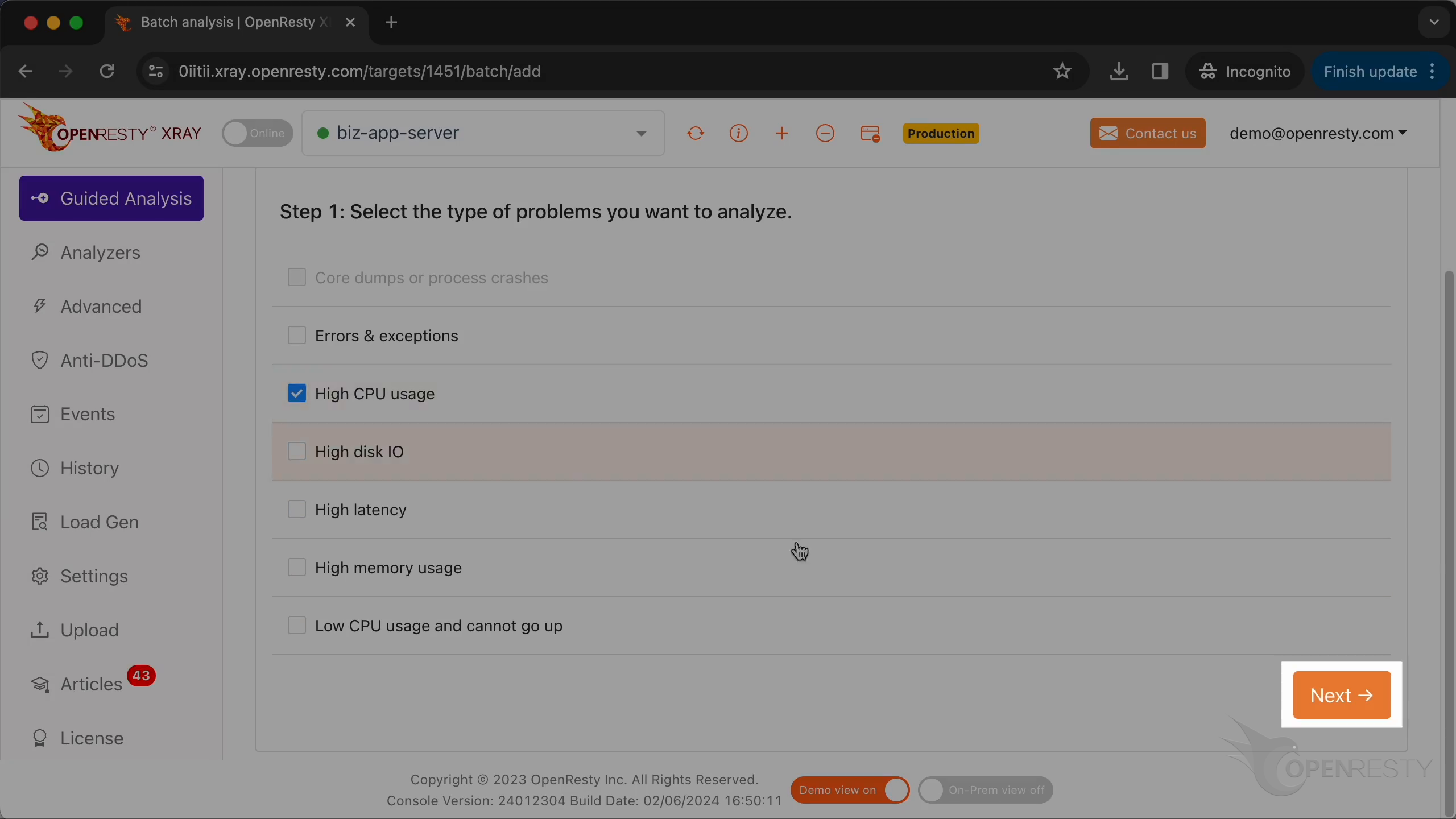
Here, you can see different types of problems that you can diagnose.
Let’s select “High CPU usage”.
Click on “Next”.
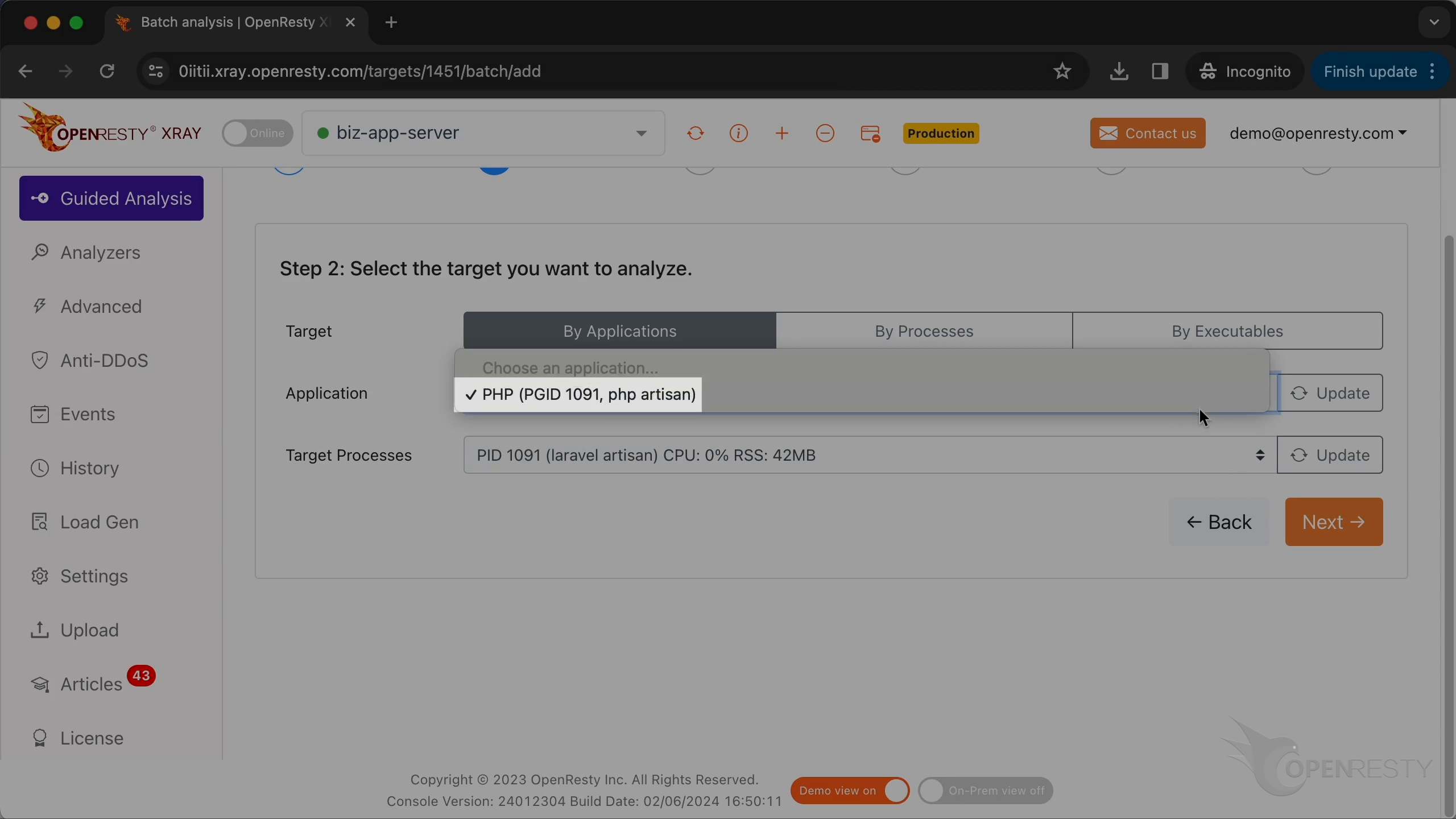
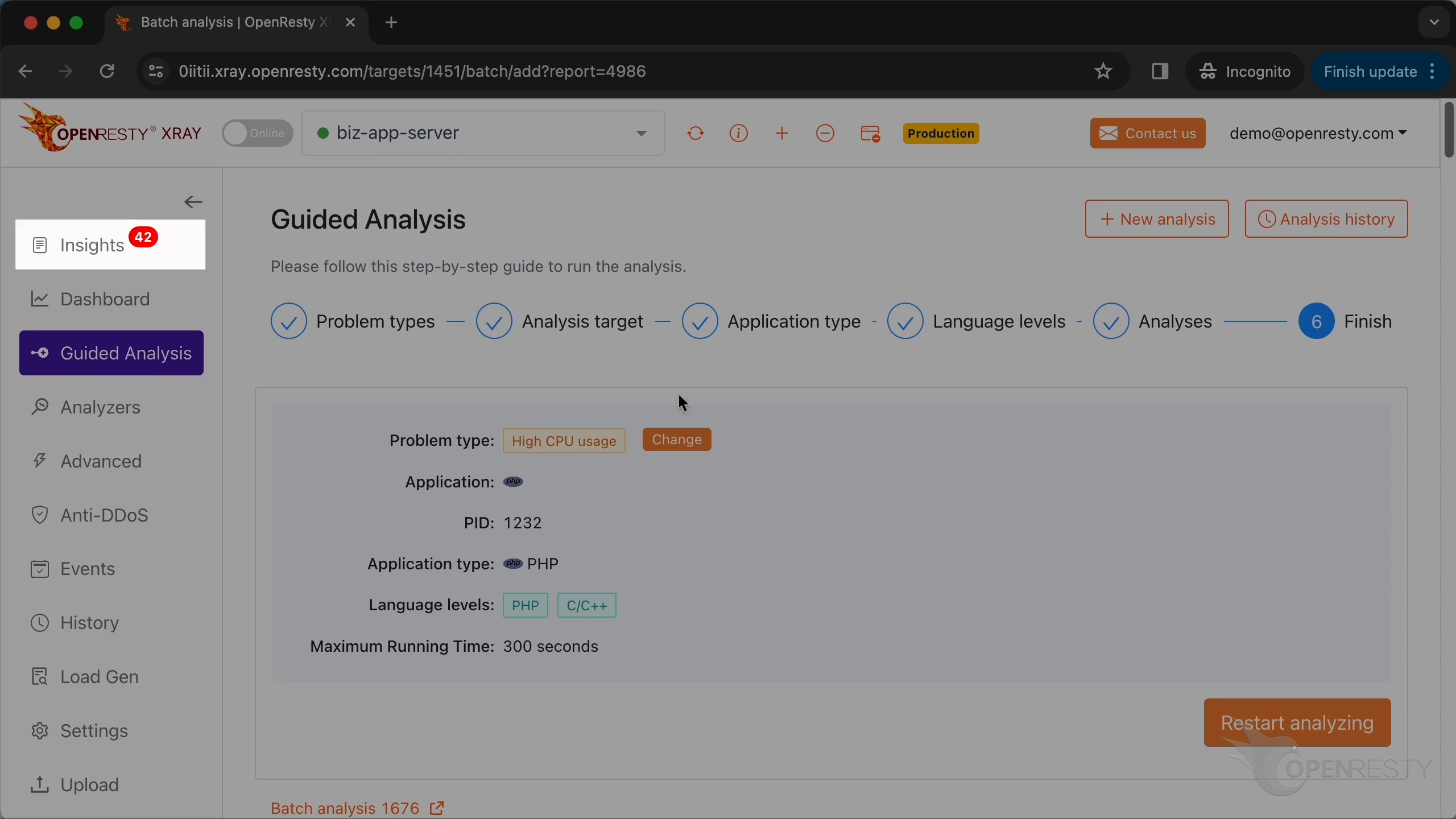
Select the PHP application.
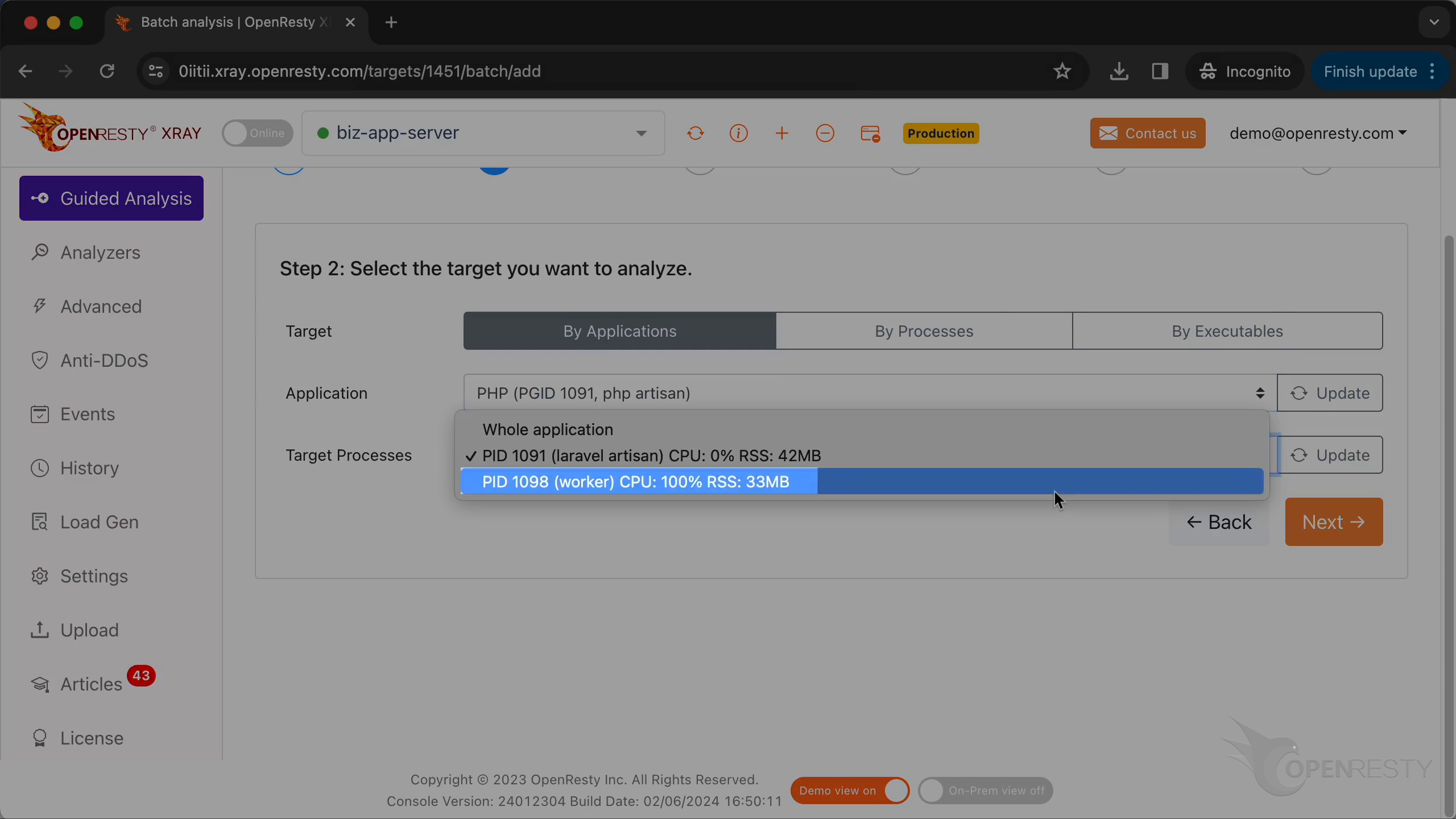
Select the process consuming 100% of the CPU resources. This is what we saw previously in top.
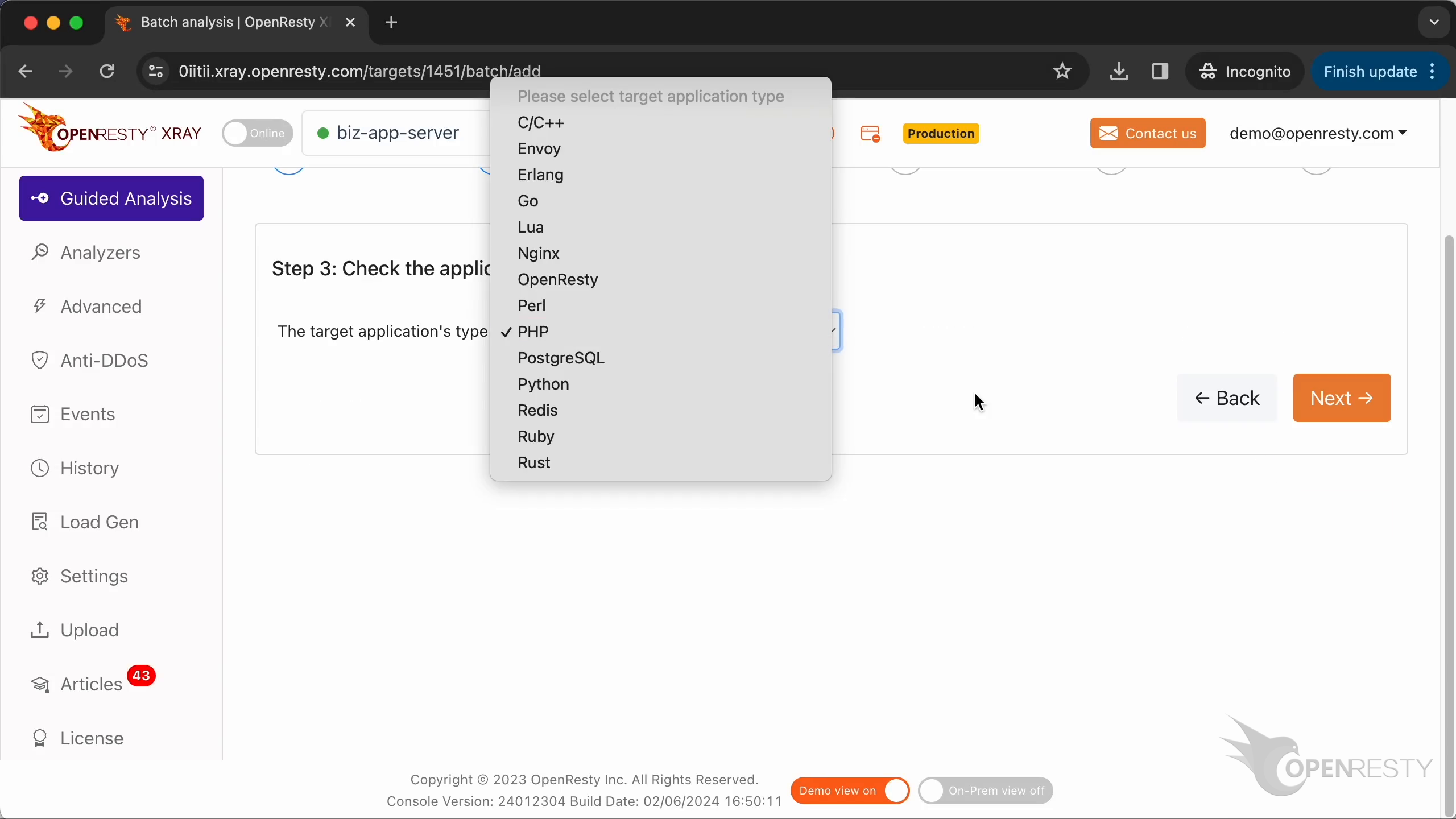
Make sure that the application type is right. Usually, the default should be correct.
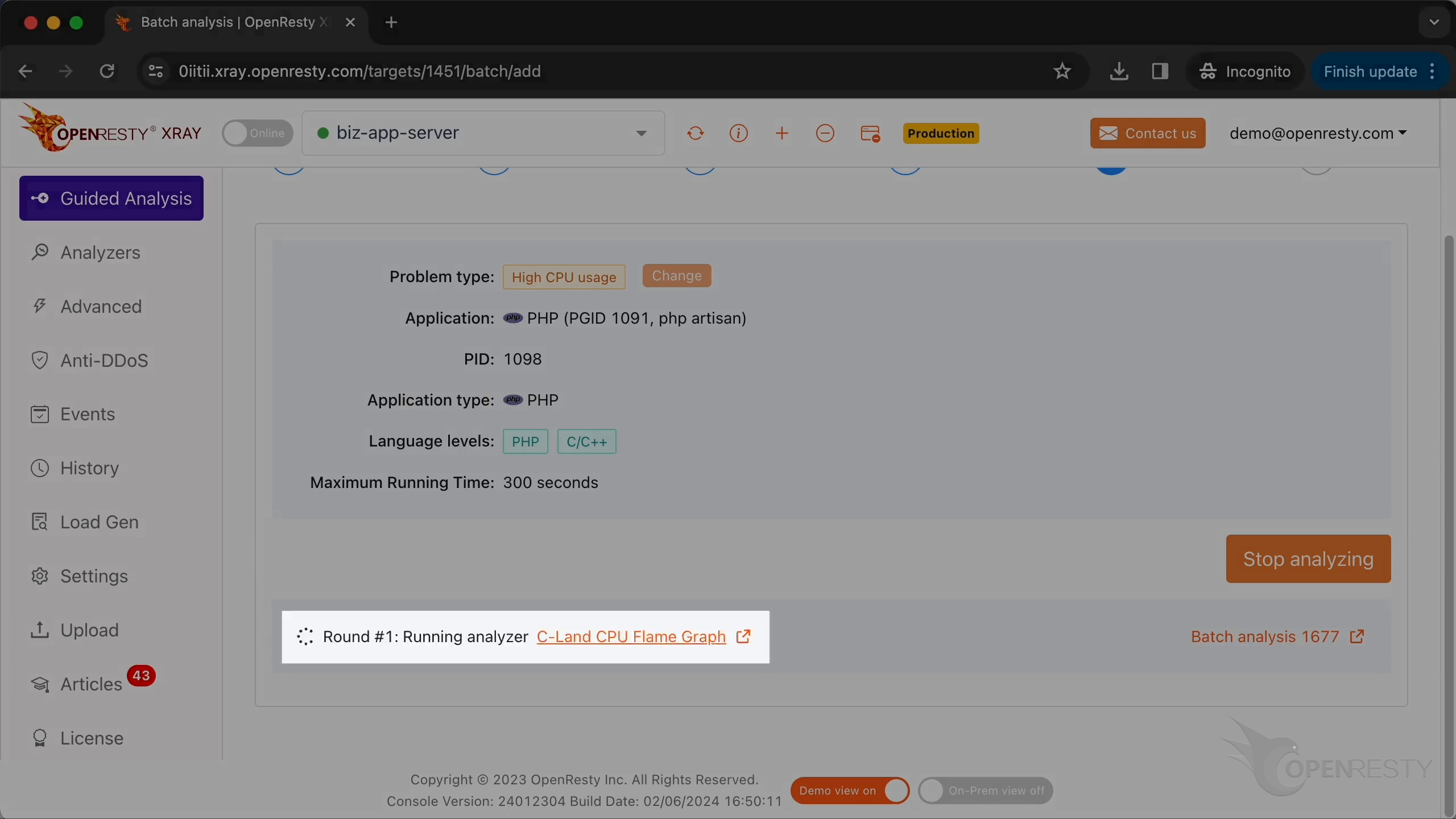
OpenResty XRay can analyze multiple language levels at the same time. We’ll keep both PHP and C/C++ selected.
We can also set the maximum analyzing time. We’ll leave it as 300 seconds, which is the default value.
Let’s start analyzing.
The system will keep performing different rounds of analysis. Now, it’s executing the first round.
The first round is done, and it’s already on to the second one. That’s enough for this case.
Let’s stop analyzing.
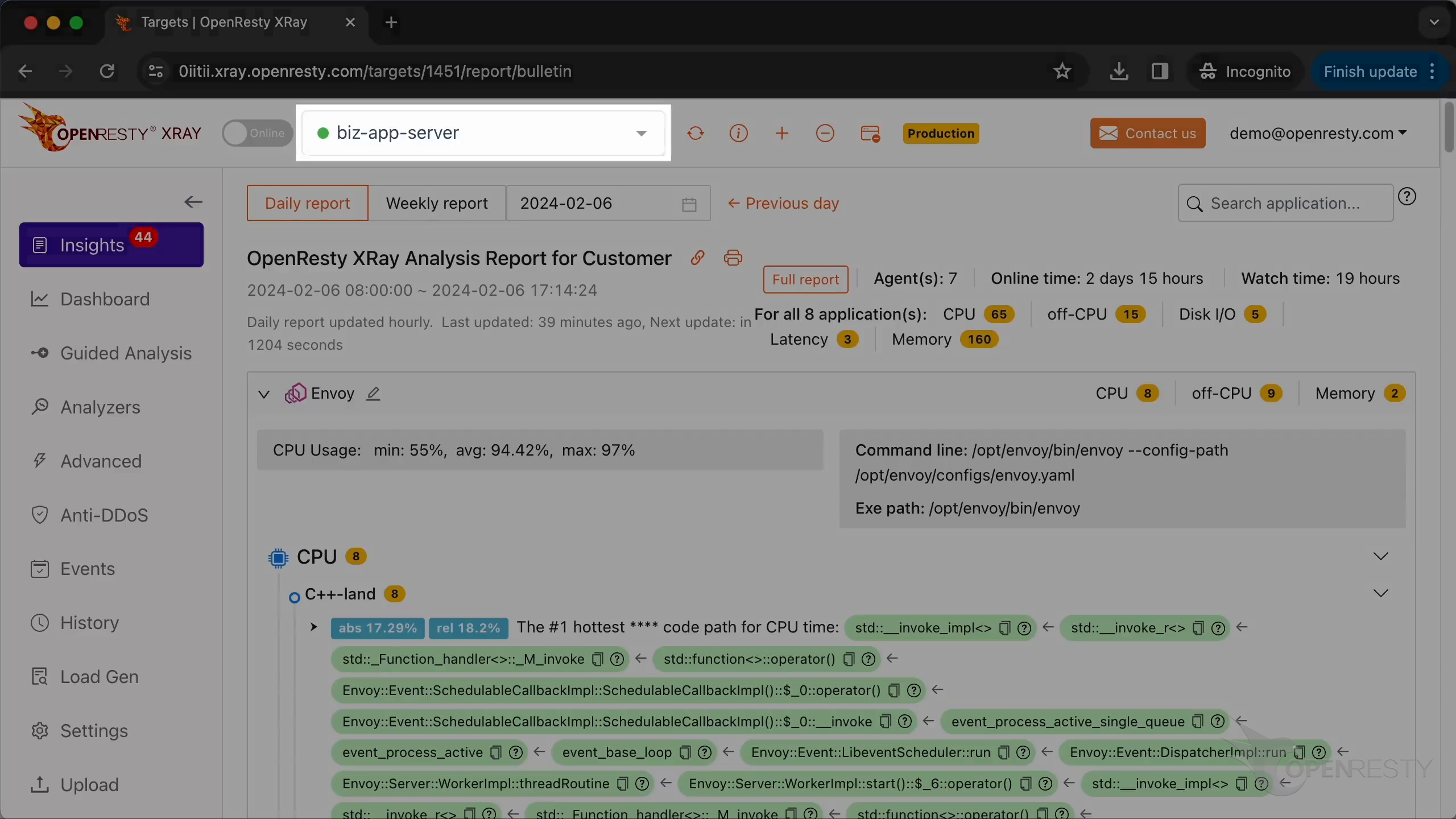
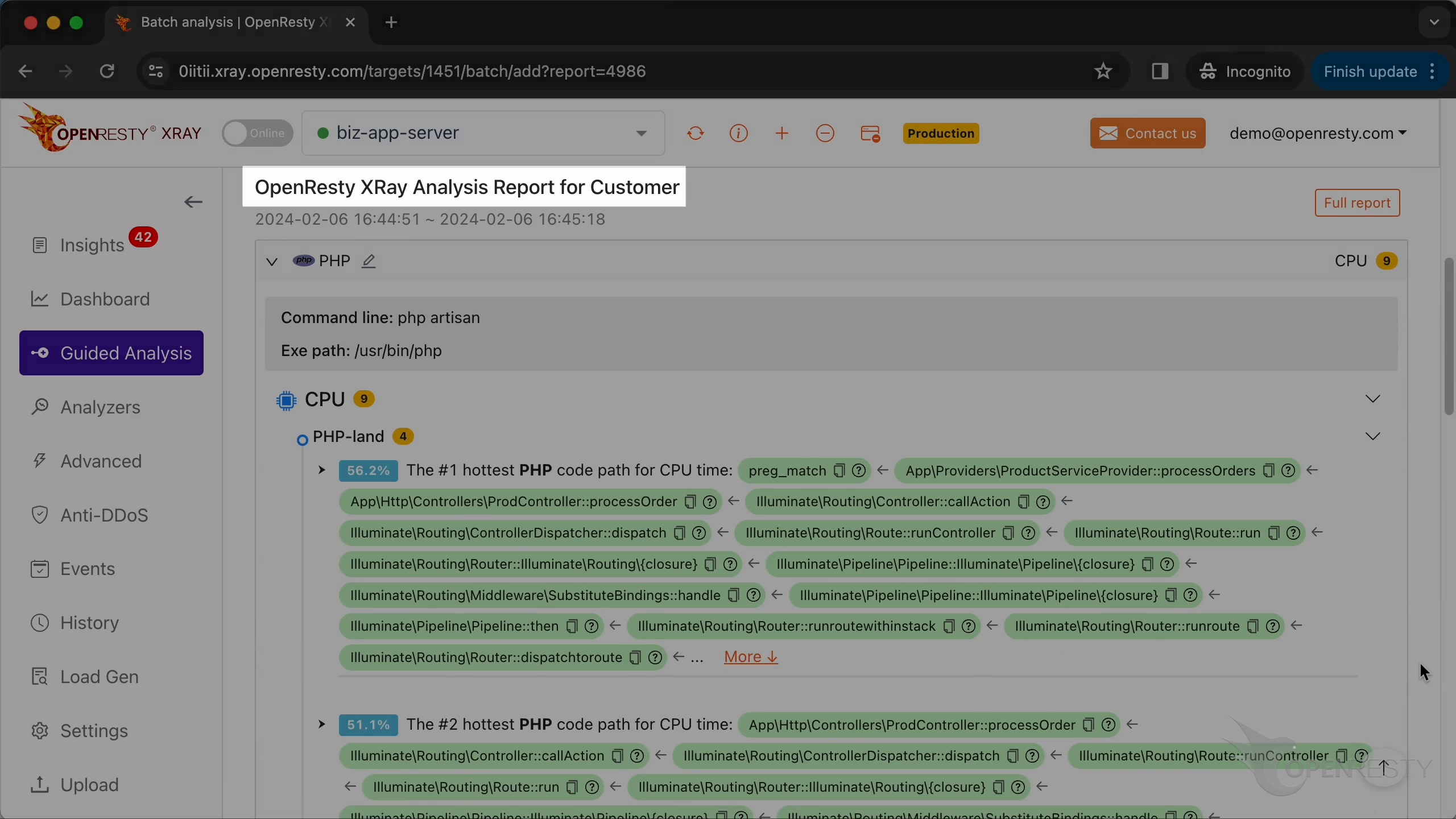
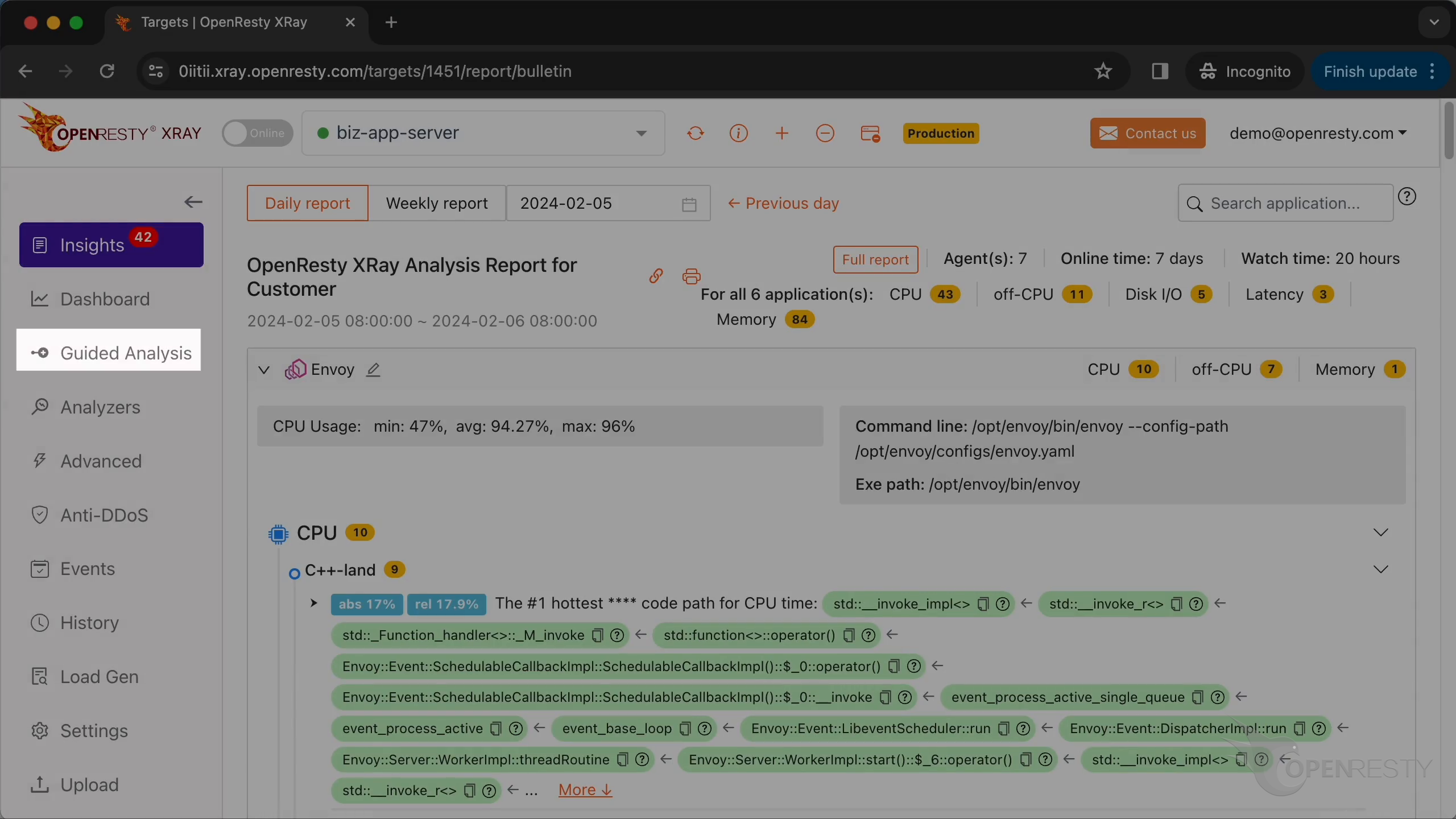
We can see it automatically created an analysis report.
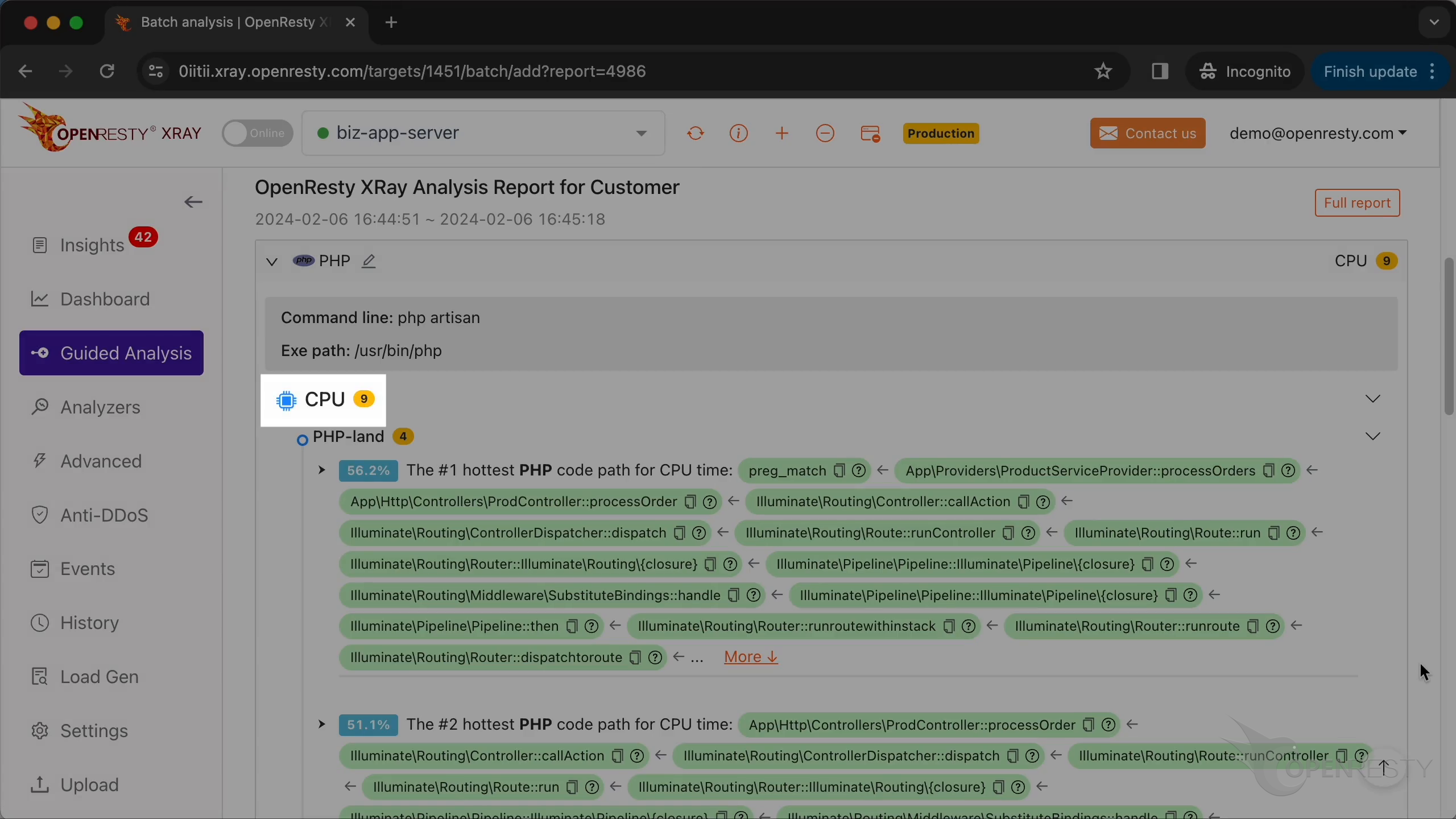
This is the type of problem we diagnose. It’s CPU.
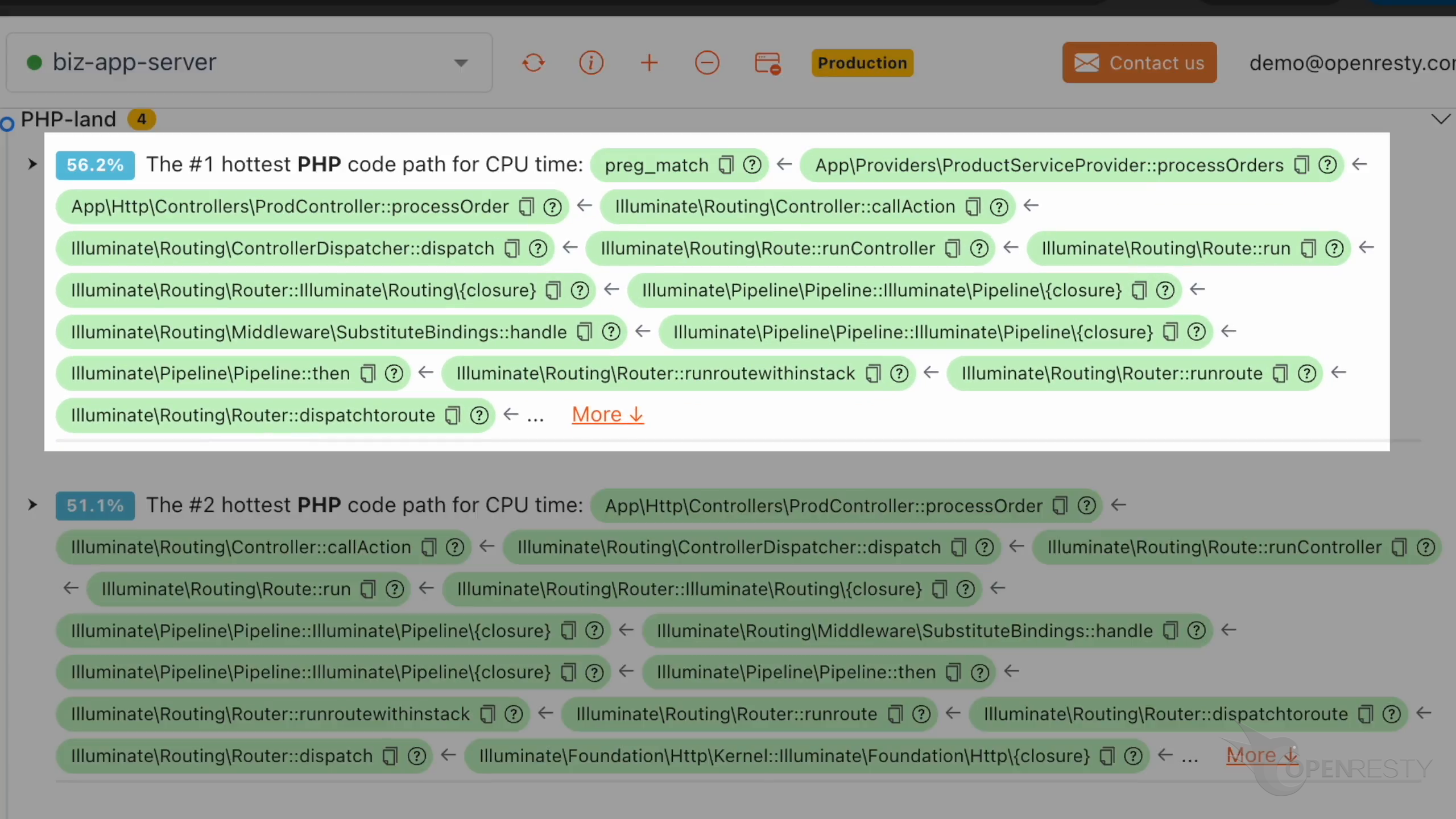
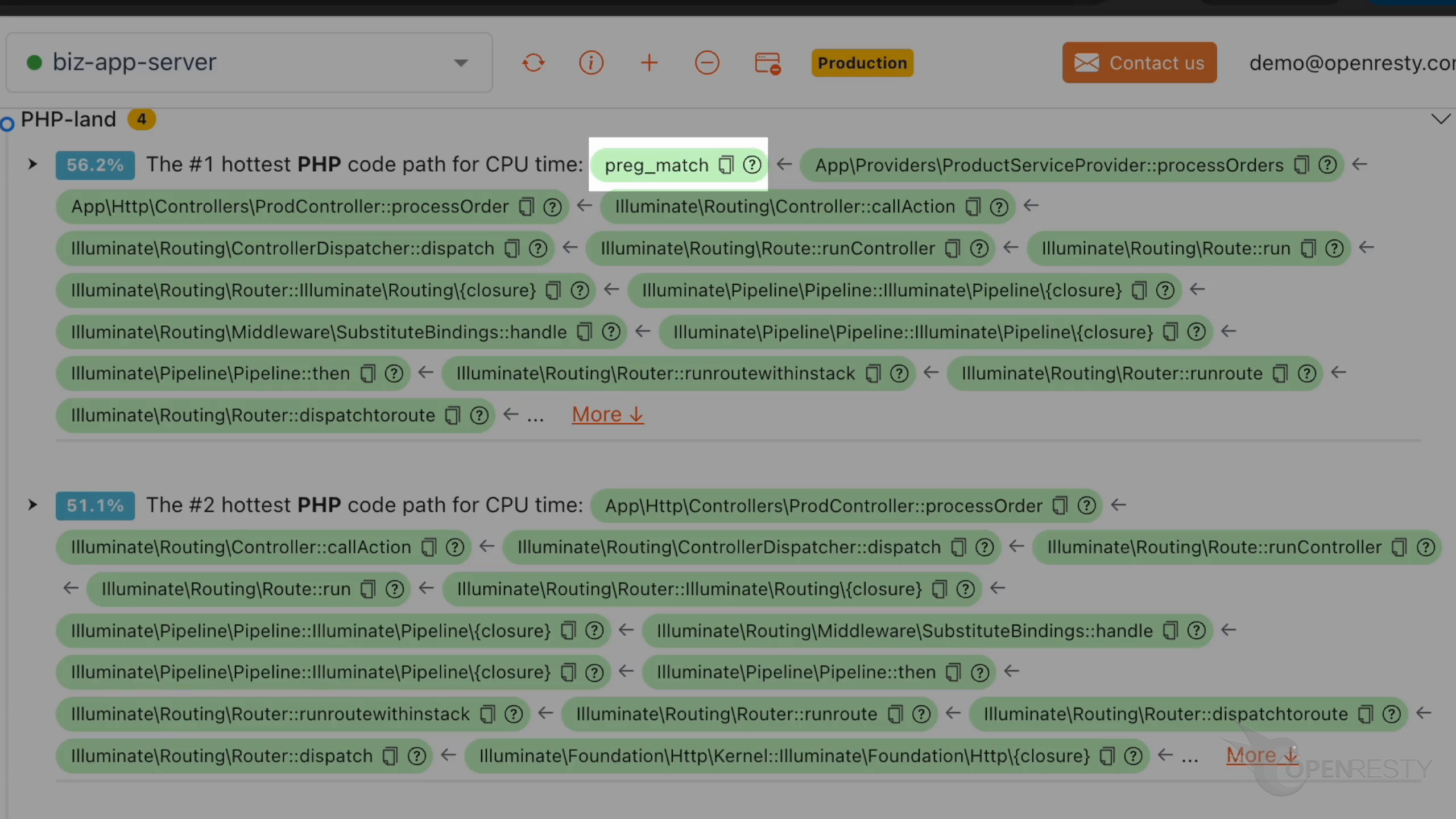
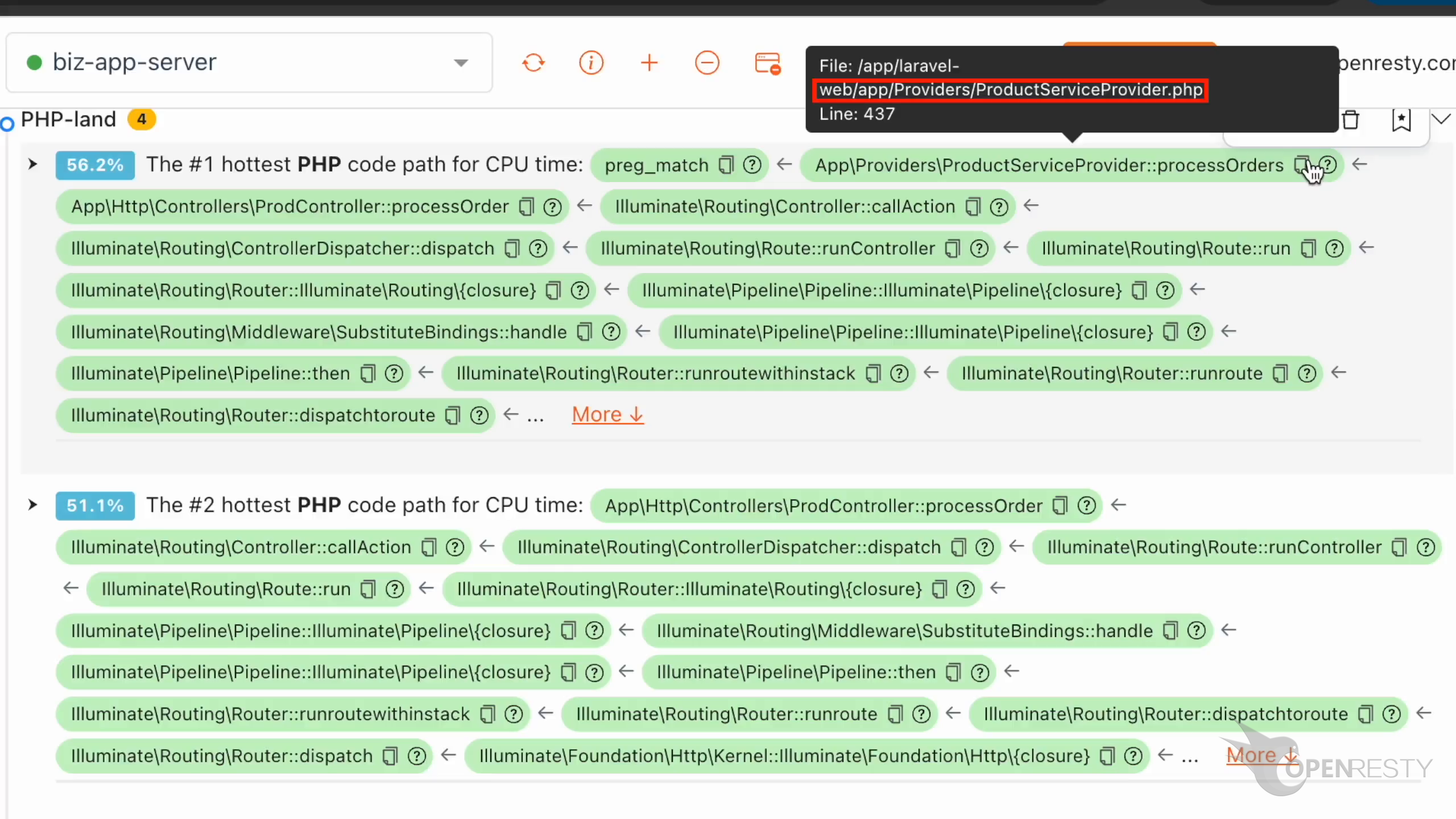
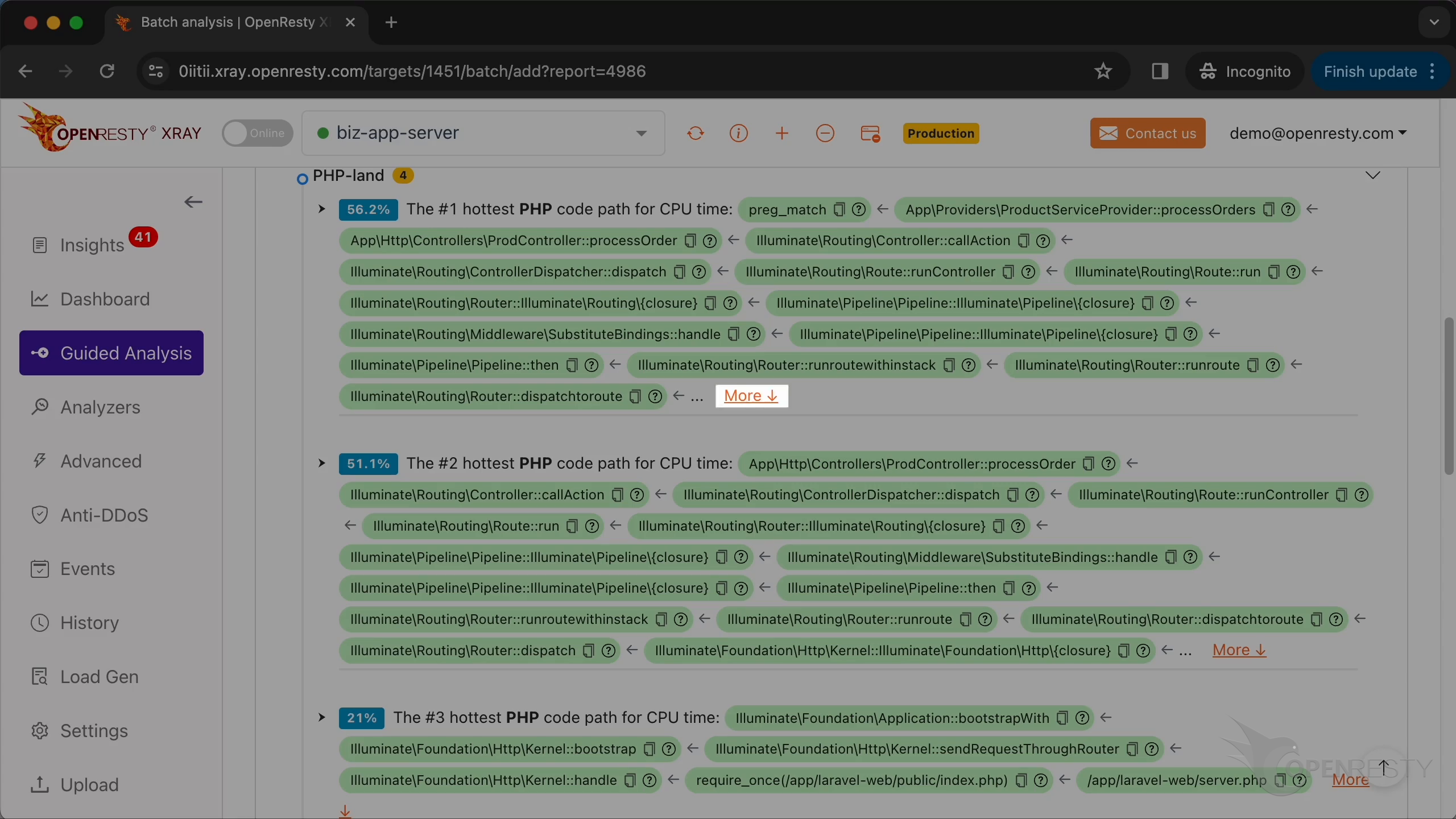
Let’s check the #1 hottest PHP code path using the most CPU time.
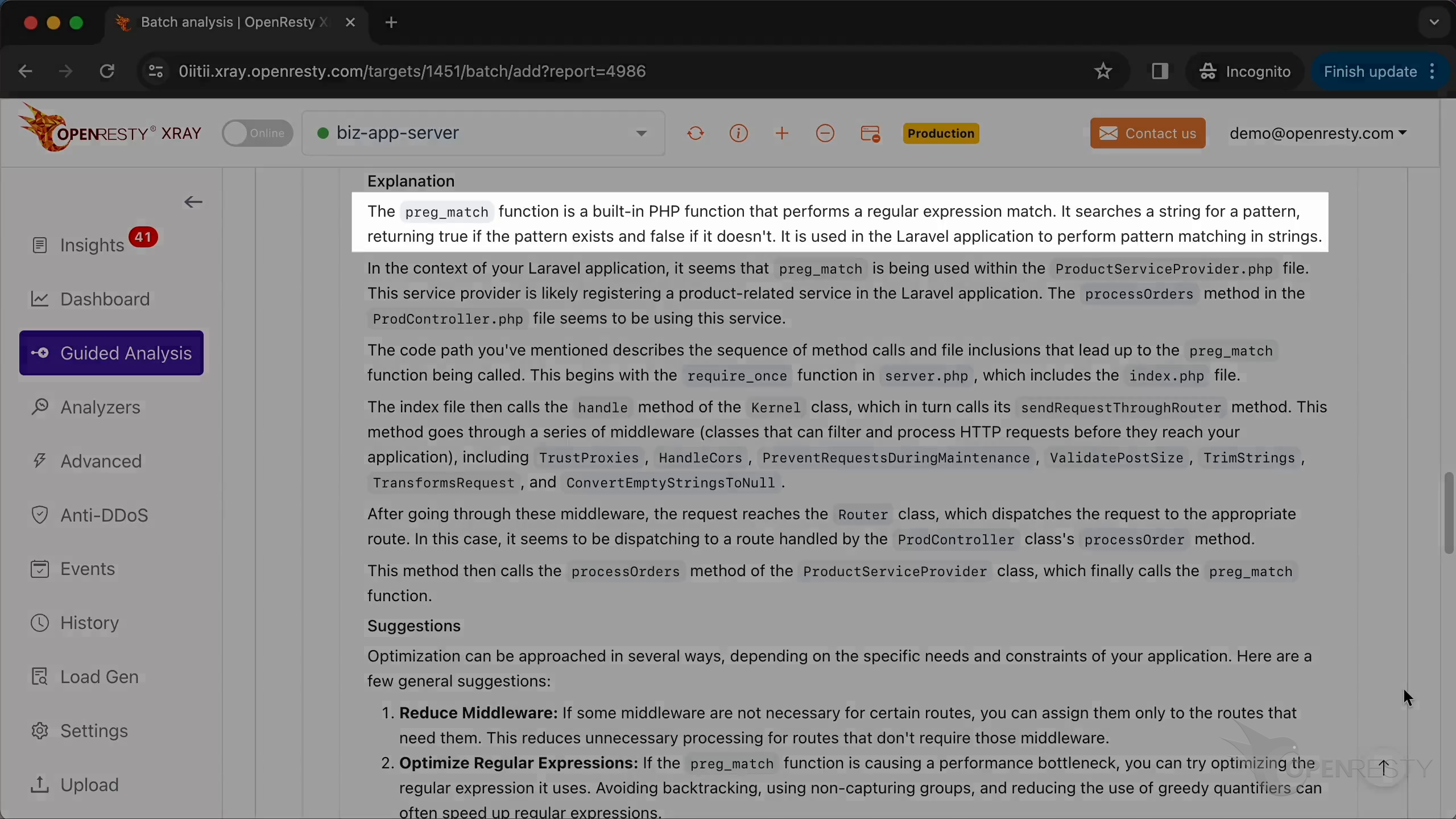
The hottest function call is preg_match. It is a PHP-level wrapper for regular expression matching.
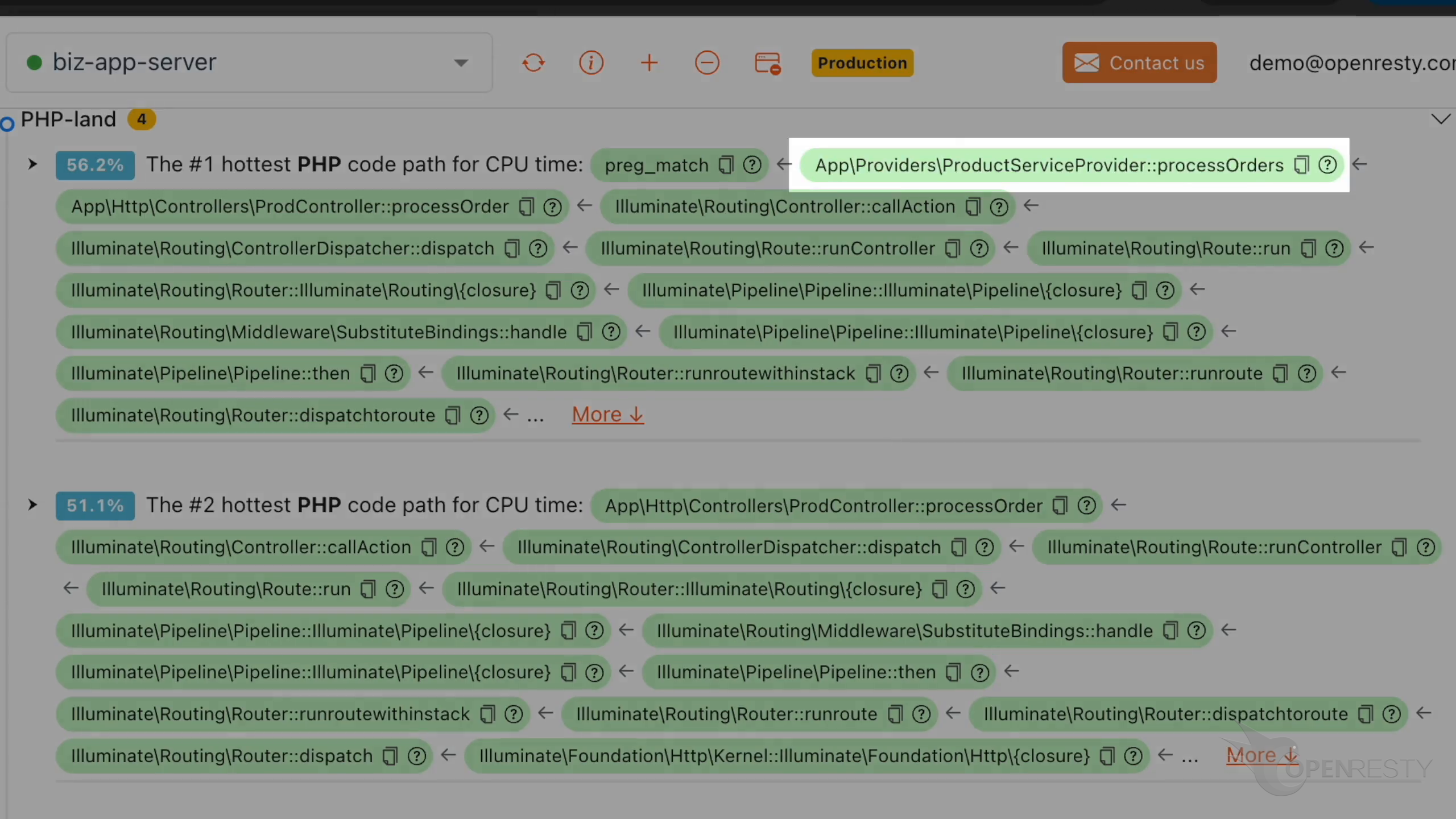
processOrders function is on the business logic level.
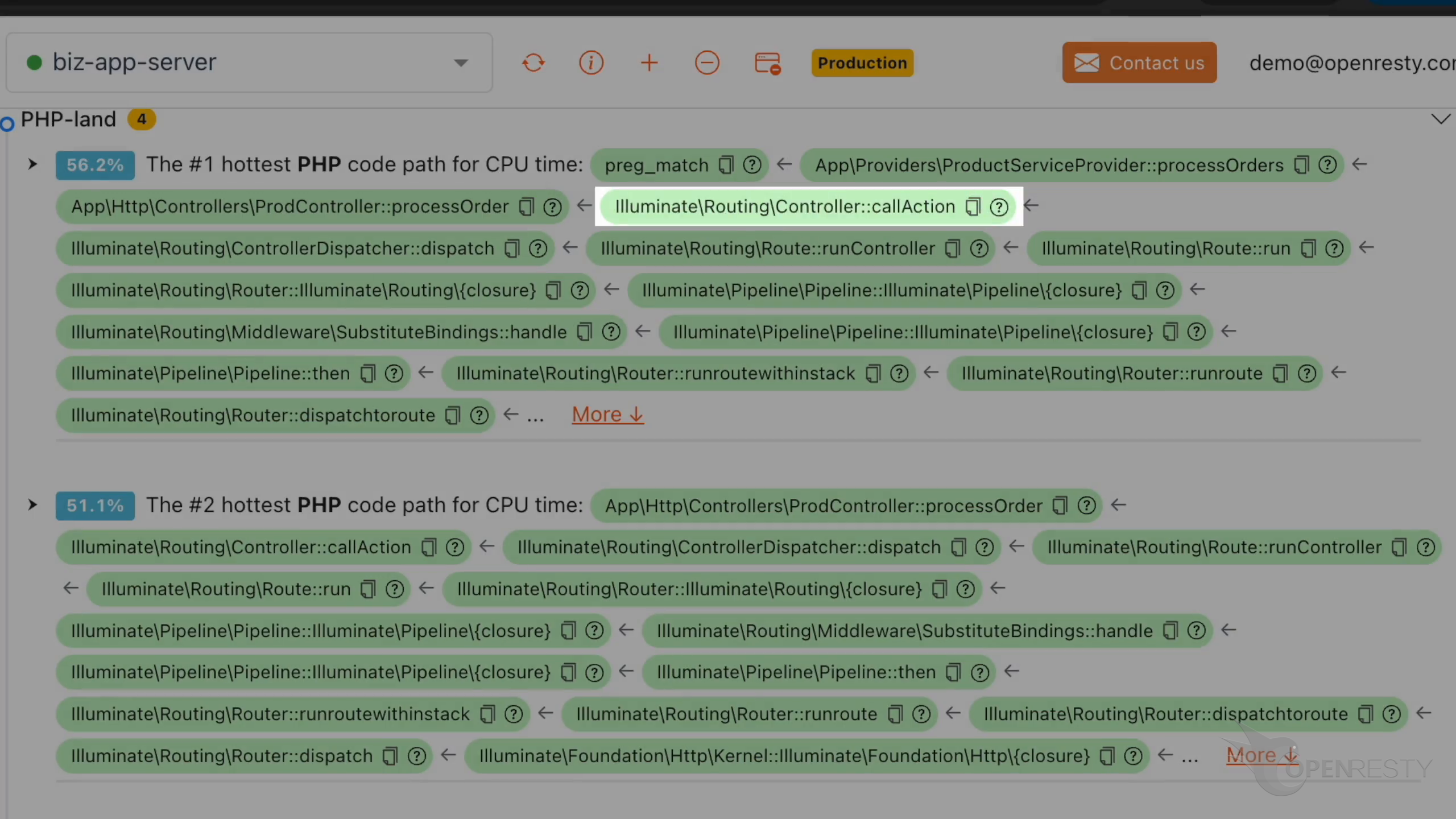
callAction is a method in the Laravel framework for calling the specified action in the controller.
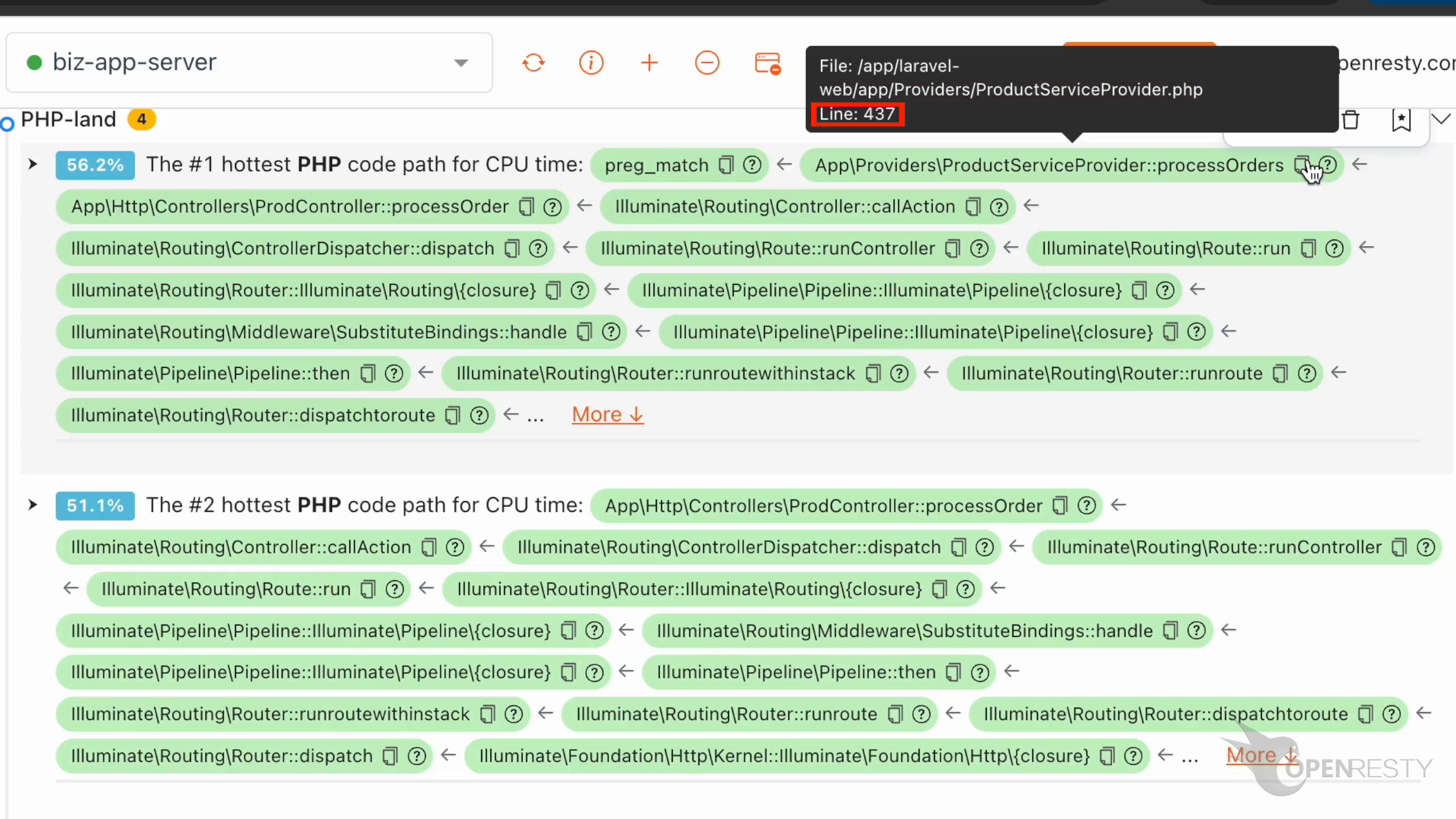
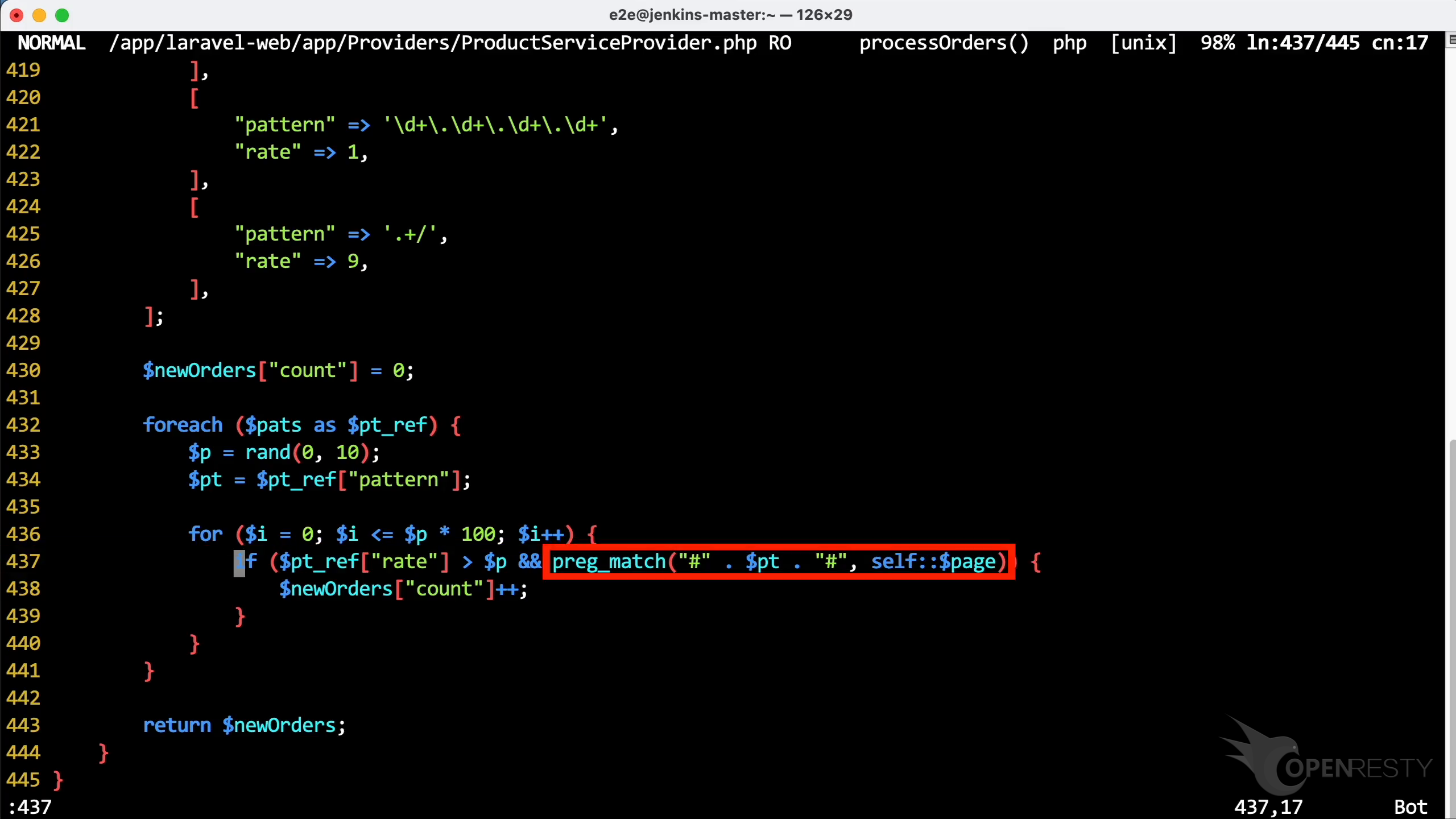
Hover the mouse over the green box for the function processOrders. We can see the PHP source file and the full path for this file in the tooltip.
The source line number is 437.
Click the icon to copy this function’s full source file path.
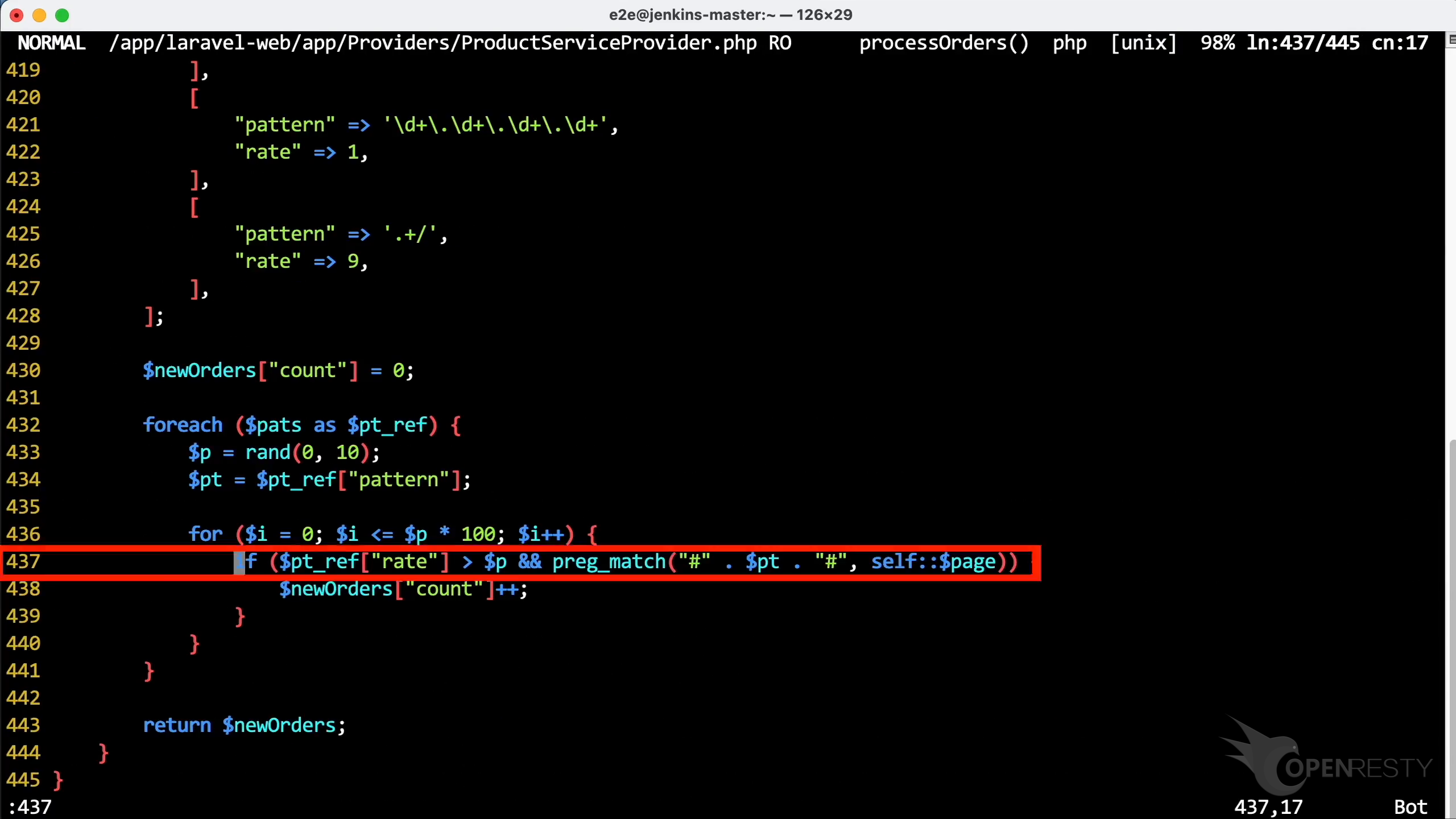
Use the vim editor to open the source file. And look at the PHP code in this file. You can use any editors you like.
Go to line 437, as OpenResty XRay suggested.
You can see that the preg_match is called as reported. Since the regular match is done multiple times in a loop. We can precompile the regular expression to optimize performance.
This source line is inside the processOrders function.
Click on “More”.
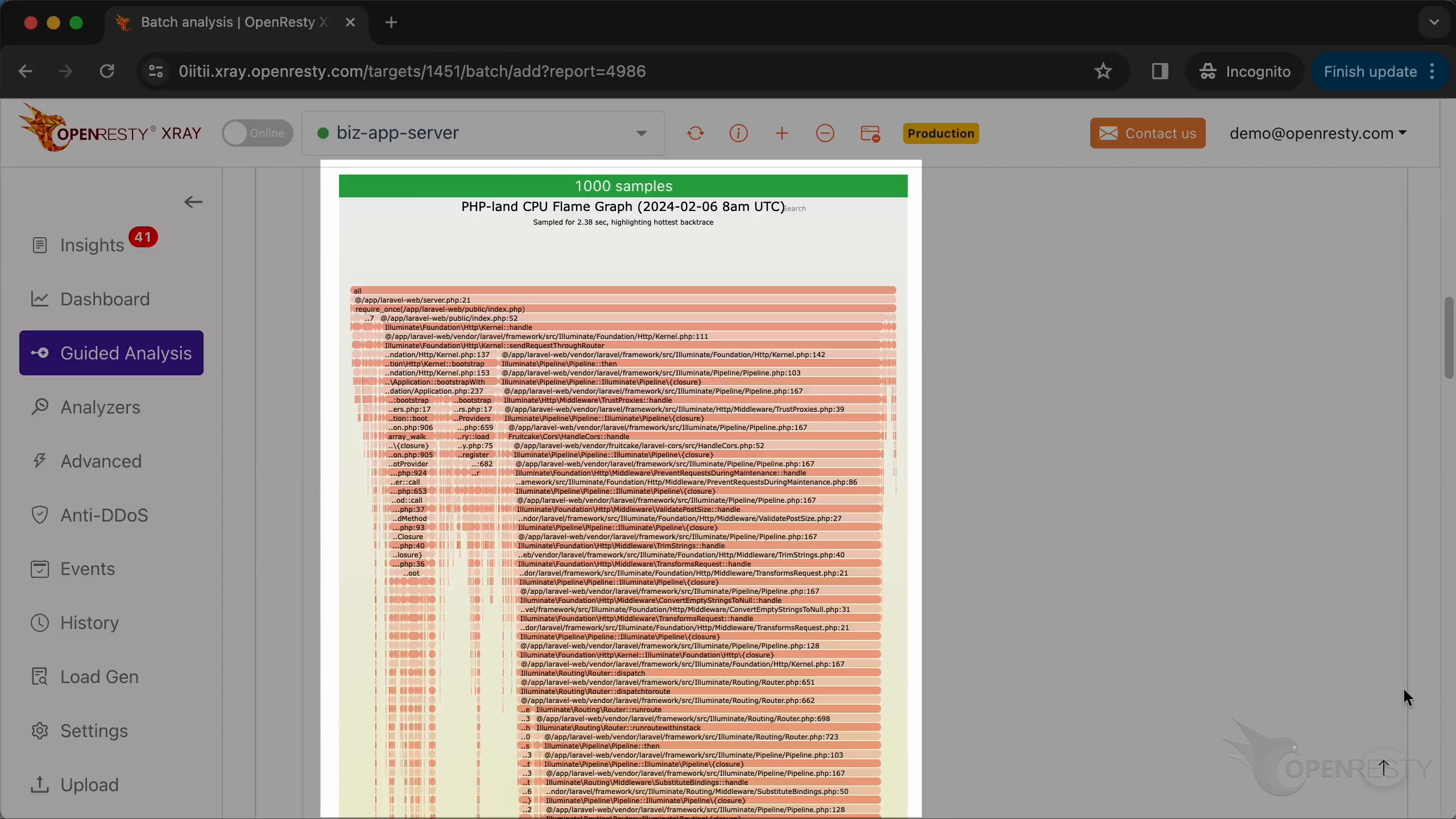
The hot code path was automatically inferred from this PHP-land CPU flame graph.
Below are more detailed explanations and suggestions regarding the current issue.
It mentions the preg_match function we saw earlier.
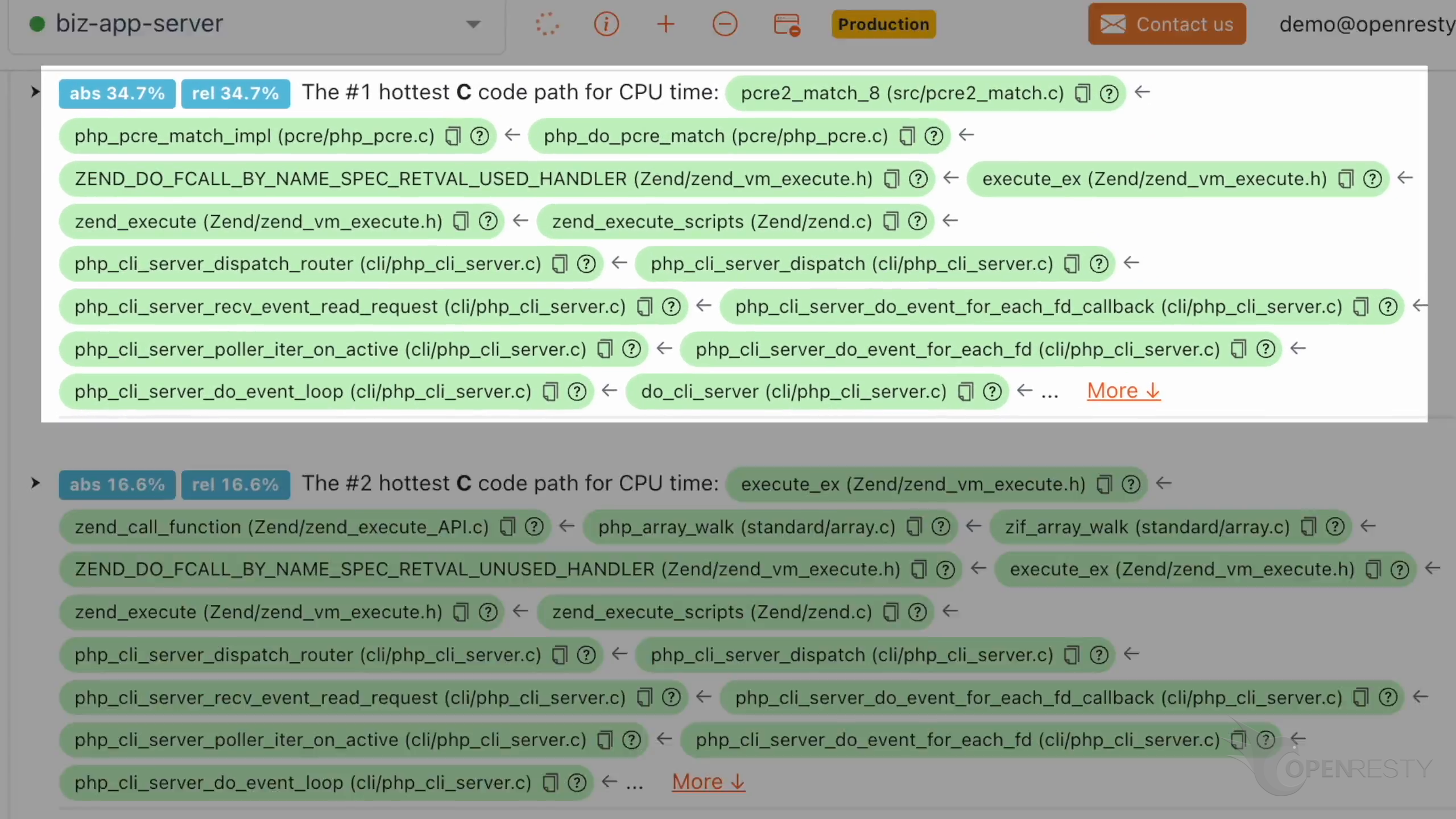
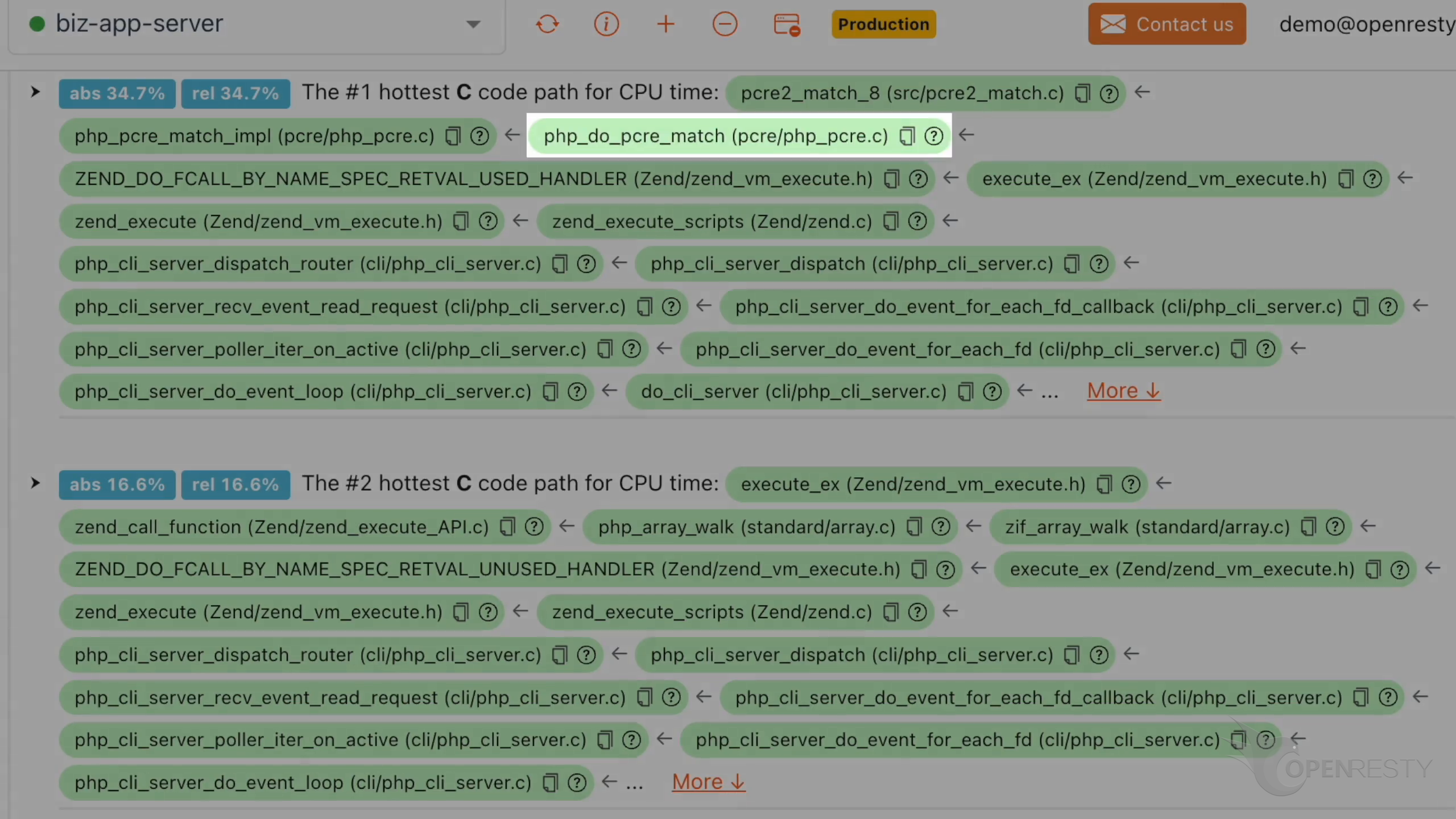
Look at the #1 hottest C code path using the most CPU time.
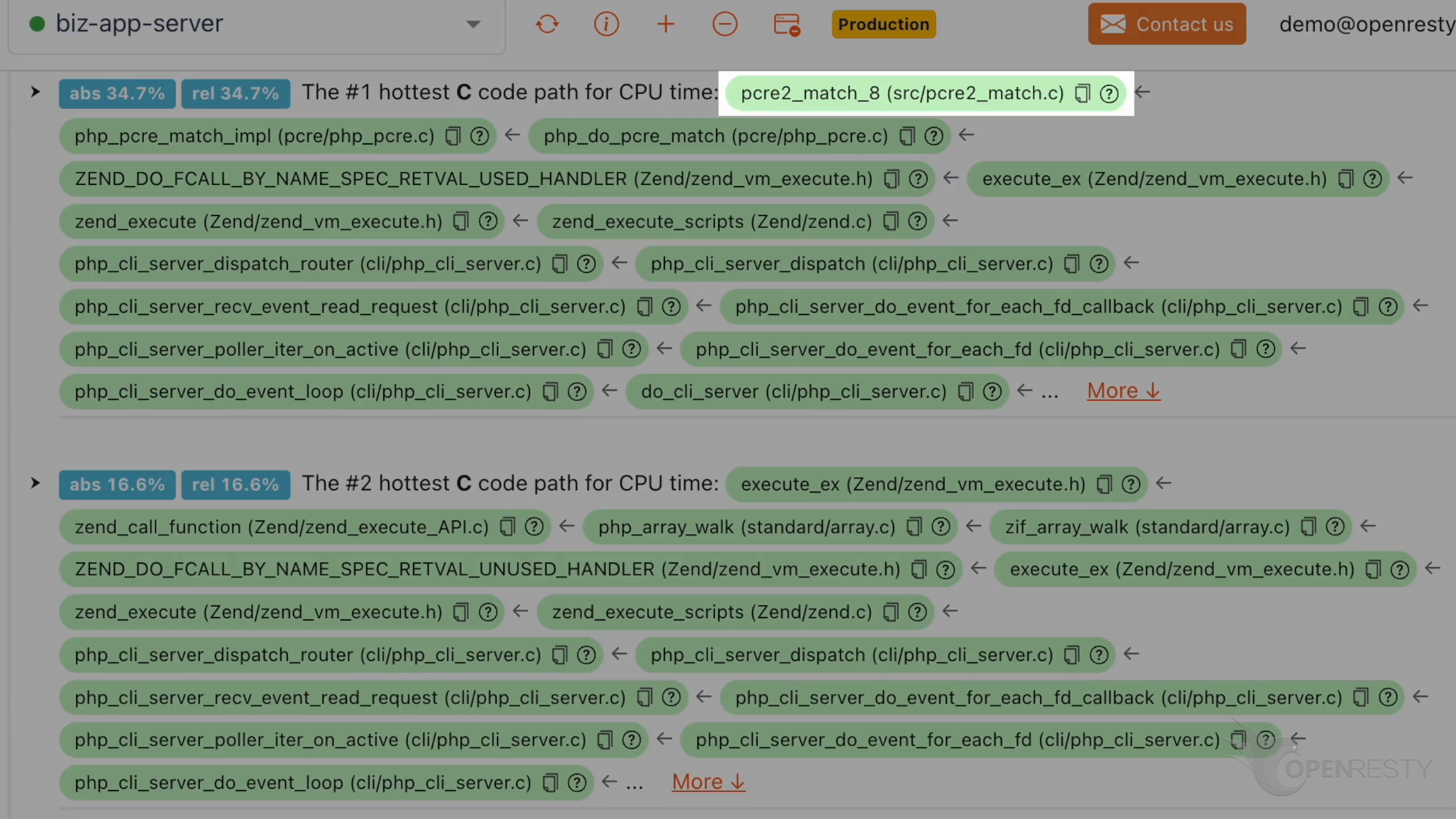
pcre2_match_8 function is part of the PCRE2 library.
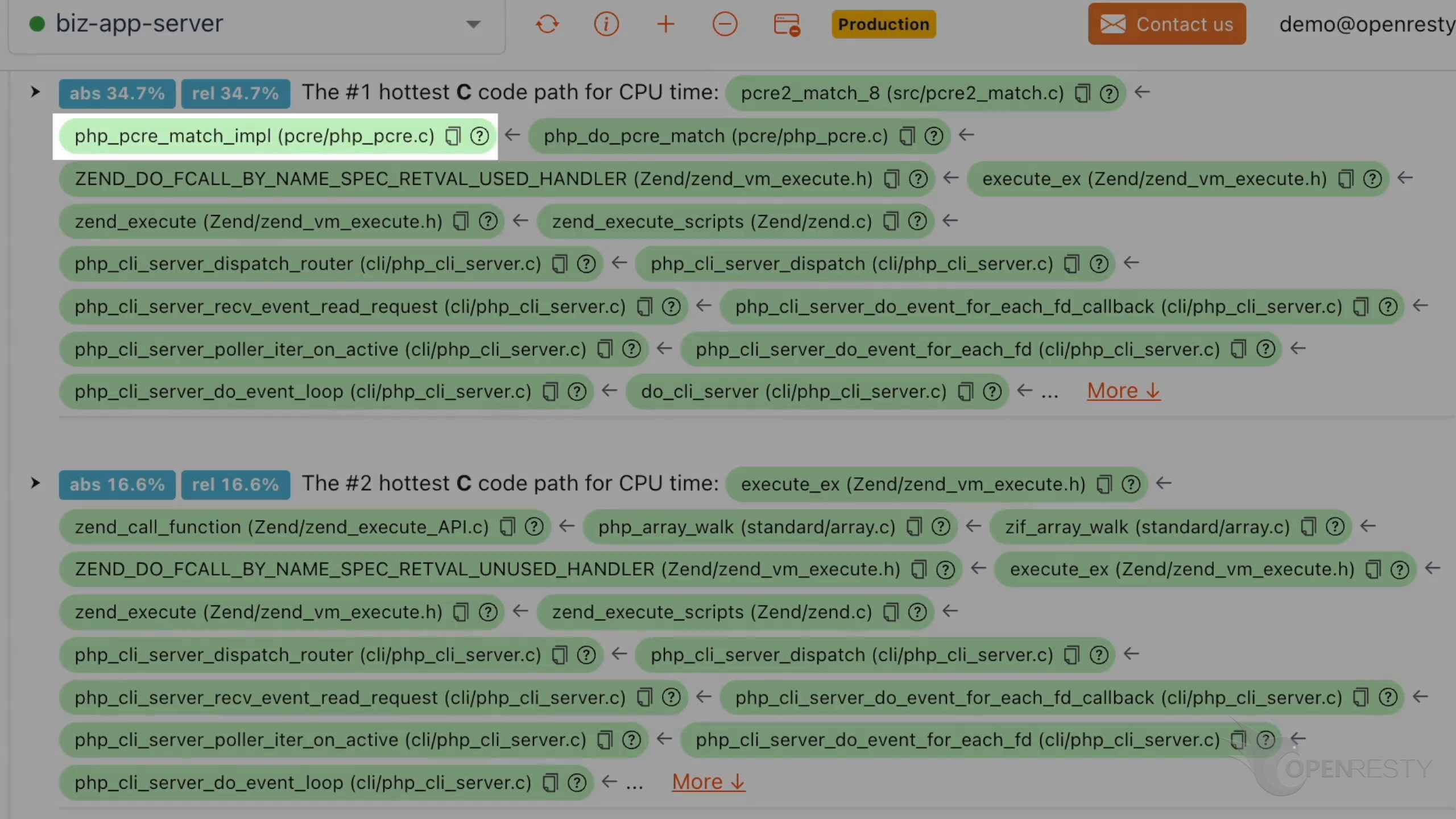
php_pcre_match_impl function internally calls the PCRE2 implementation for regular expression matching.
php_do_pcre_match implements the preg_match function. It matches a regular expression against a string.
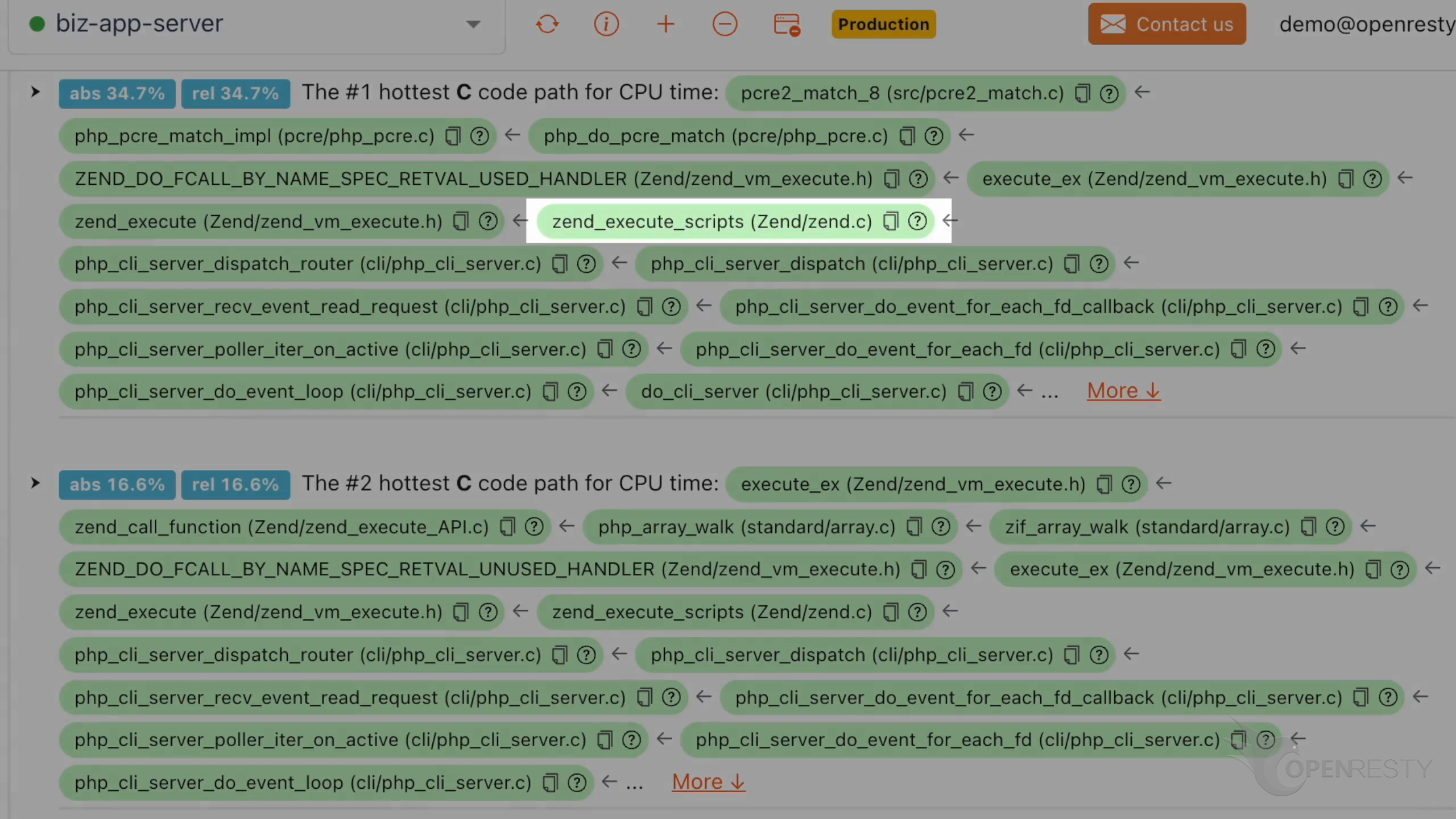
zend_execute_scripts function executes the PHP script. Apparently, this resembles the hottest PHP code path we just saw earlier.
Automatic analysis and reports
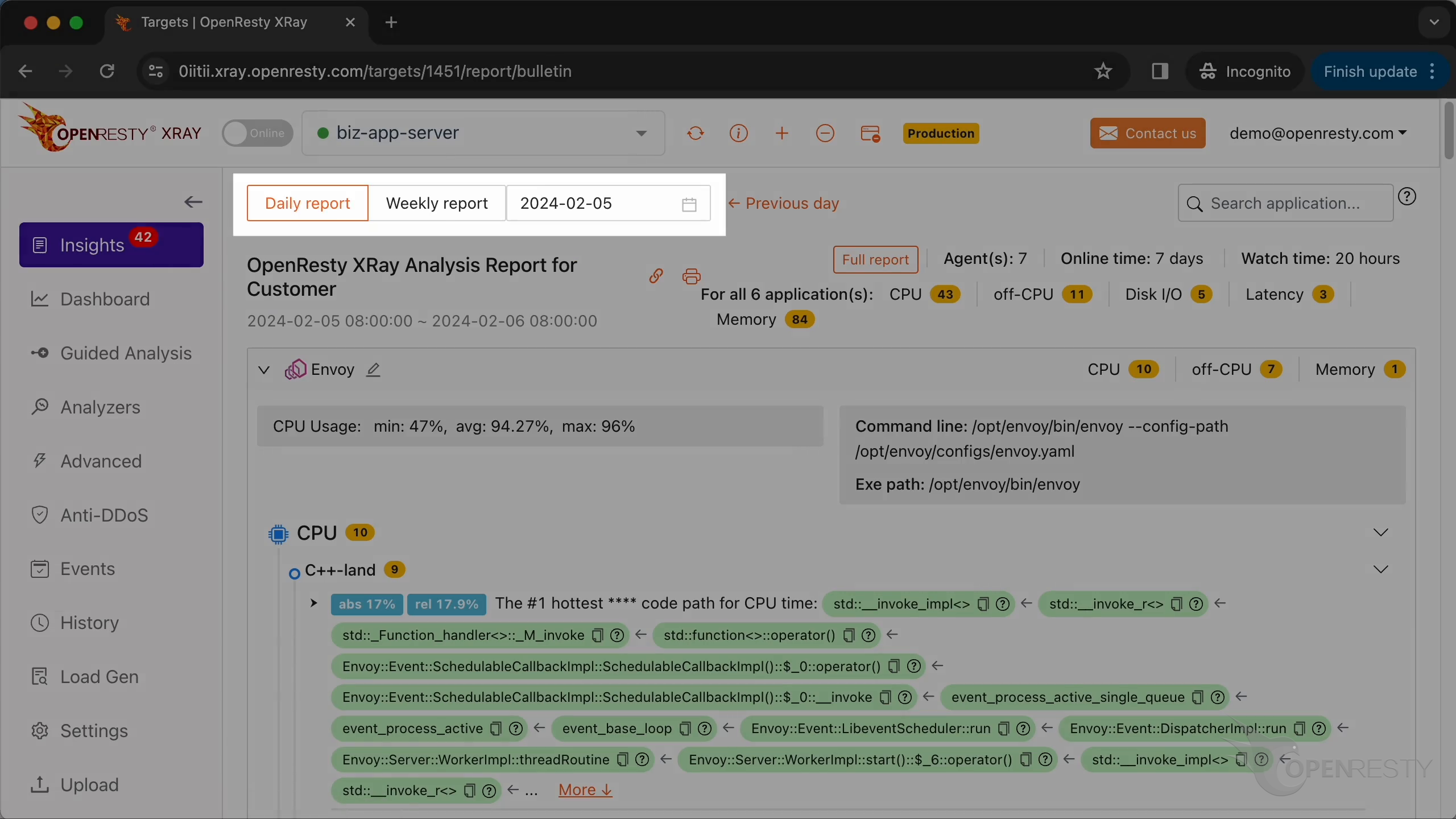
OpenResty XRay can also monitor online processes automatically and generate analysis reports. Go to the “Insights” page.
You can find the automatic reports on the “Insights” page for daily and weekly periods. For this reason, you don’t have to use the Guided Analysis feature.
Though Guided analysis is useful for application development and demonstration purposes.
What is OpenResty XRay
OpenResty XRay is a dynamic-tracing product that automatically analyzes your running applications to troubleshoot performance problems, behavioral issues, and security vulnerabilities with actionable suggestions. Under the hood, OpenResty XRay is powered by our Y language targeting various runtimes like Stap+, eBPF+, GDB, and ODB, depending on the contexts.
If you like this tutorial, please subscribe to this blog site and/or our YouTube channel. Thank you!
About The Author
Yichun Zhang (Github handle: agentzh), is the original creator of the OpenResty® open-source project and the CEO of OpenResty Inc..
Yichun is one of the earliest advocates and leaders of “open-source technology”. He worked at many internationally renowned tech companies, such as Cloudflare, Yahoo!. He is a pioneer of “edge computing”, “dynamic tracing” and “machine coding”, with over 22 years of programming and 16 years of open source experience. Yichun is well-known in the open-source space as the project leader of OpenResty®, adopted by more than 40 million global website domains.
OpenResty Inc., the enterprise software start-up founded by Yichun in 2017, has customers from some of the biggest companies in the world. Its flagship product, OpenResty XRay, is a non-invasive profiling and troubleshooting tool that significantly enhances and utilizes dynamic tracing technology. And its OpenResty Edge product is a powerful distributed traffic management and private CDN software product.
As an avid open-source contributor, Yichun has contributed more than a million lines of code to numerous open-source projects, including Linux kernel, Nginx, LuaJIT, GDB, SystemTap, LLVM, Perl, etc. He has also authored more than 60 open-source software libraries.