How to pass the real client IP addresses to backend servers via special request headers
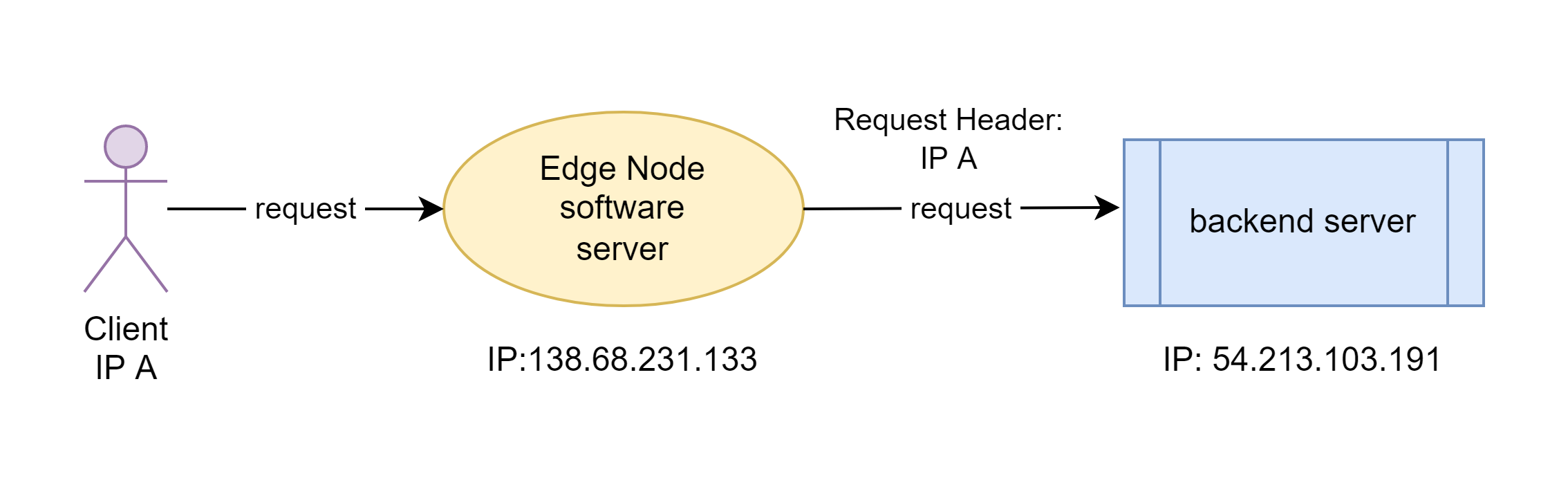
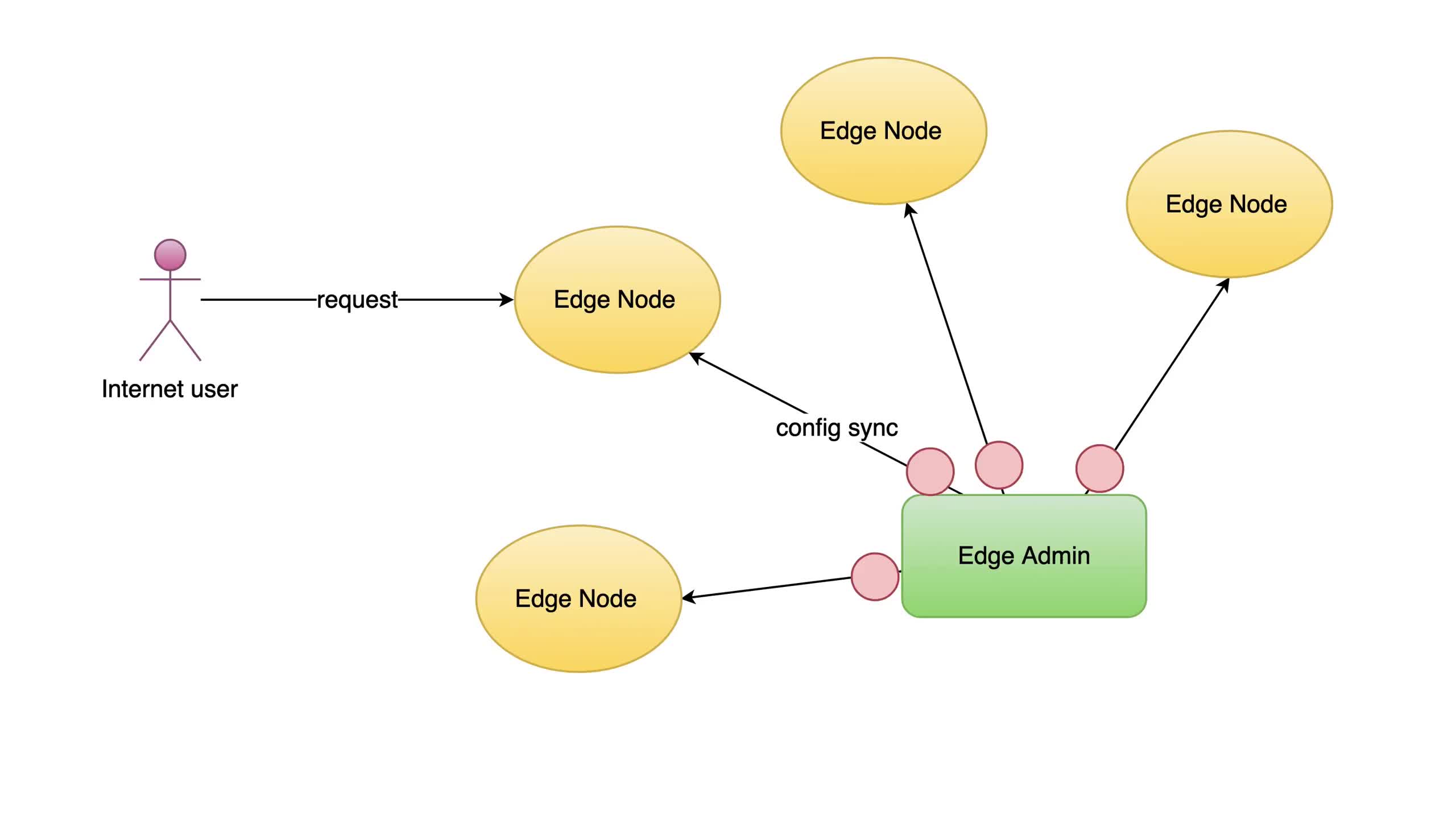
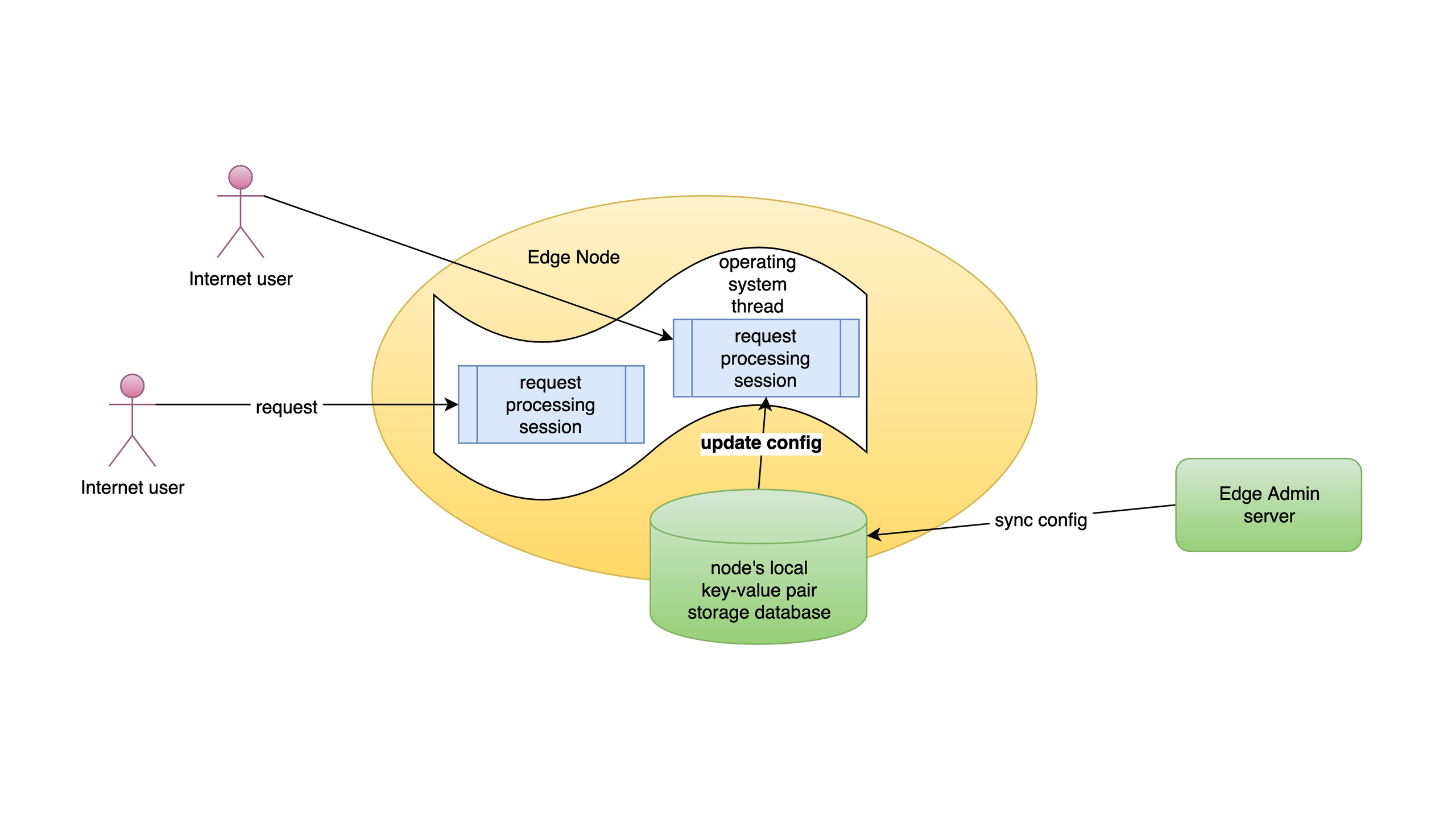
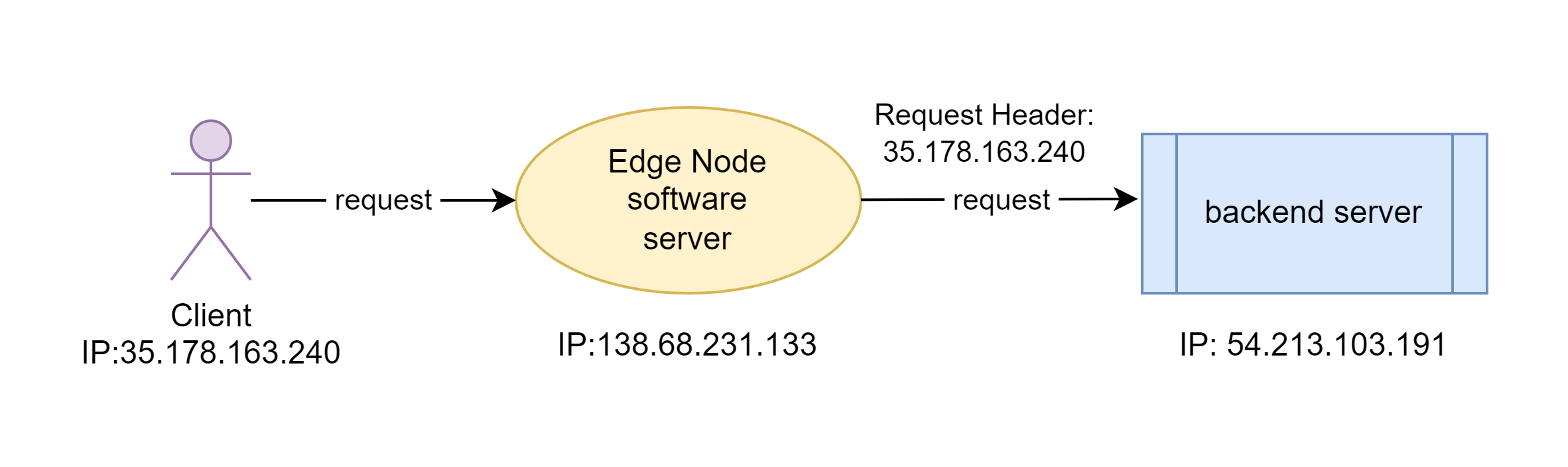
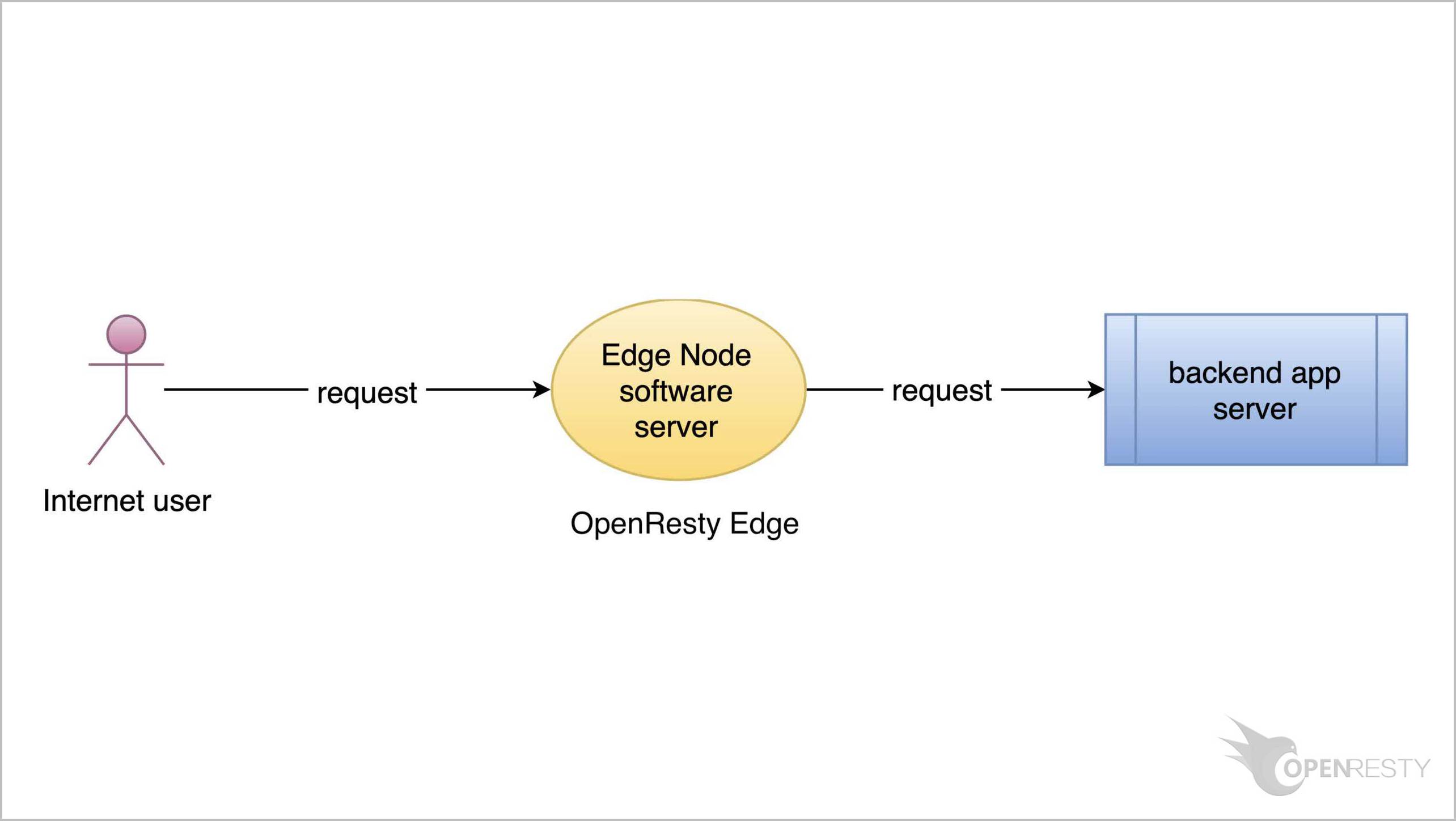
Today I’d demonstrate another feature in OpenResty Edge. That is, to pass the real client IP addresses to backend servers via special request headers. Usually, the client IP addresses seen by the backend servers or origin sites are those of the gateway or proxy servers instead of the original clients’. If the origin site needs the real client IP addresses, we need to create a new request header and put the client IP addresse there. This way, the backend servers can just read the request header.
Set up page rules for applications
Let’s go to a web console of OpenResty Edge. This is our sample deployment of the console. Every user has her own deployment.
We can still use our continuing sample application, test-edge.com.
Enter the application.
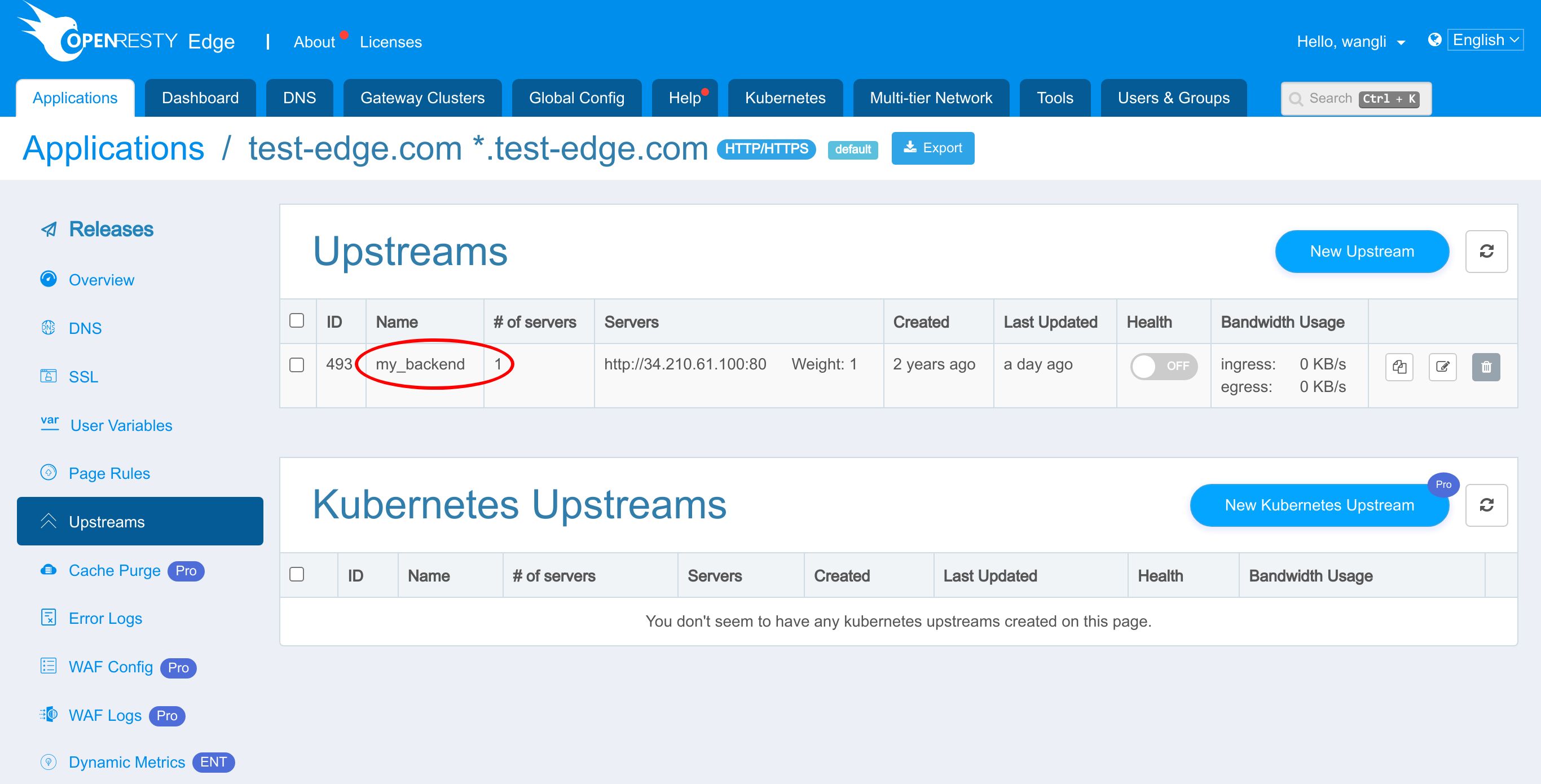
We already have an upstream defined in our earlier tutorial.
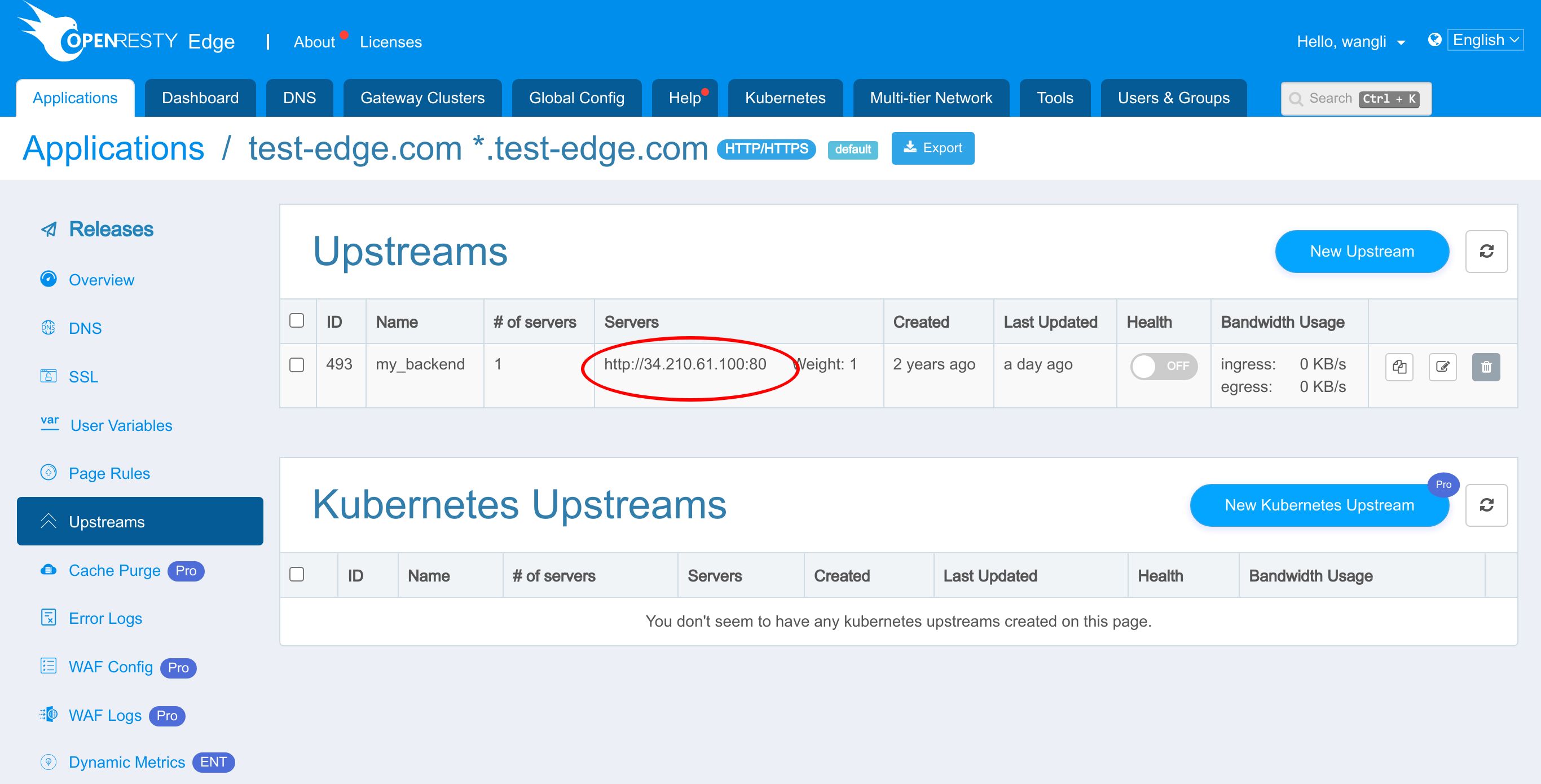
This my_backend upstream has a backend server defined already.
Note the IP address of the backend server ends with .100. We will use this IP address later.
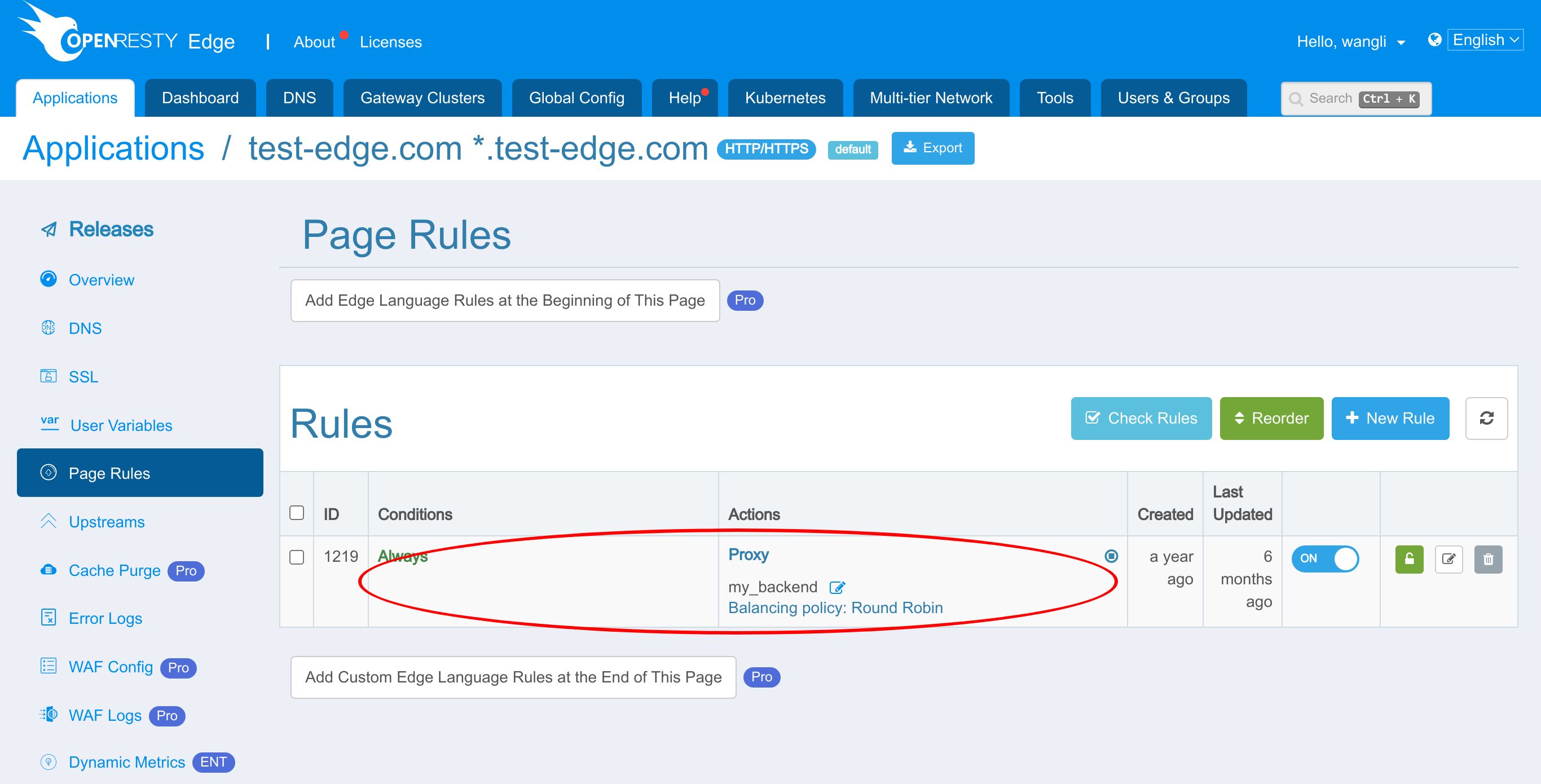
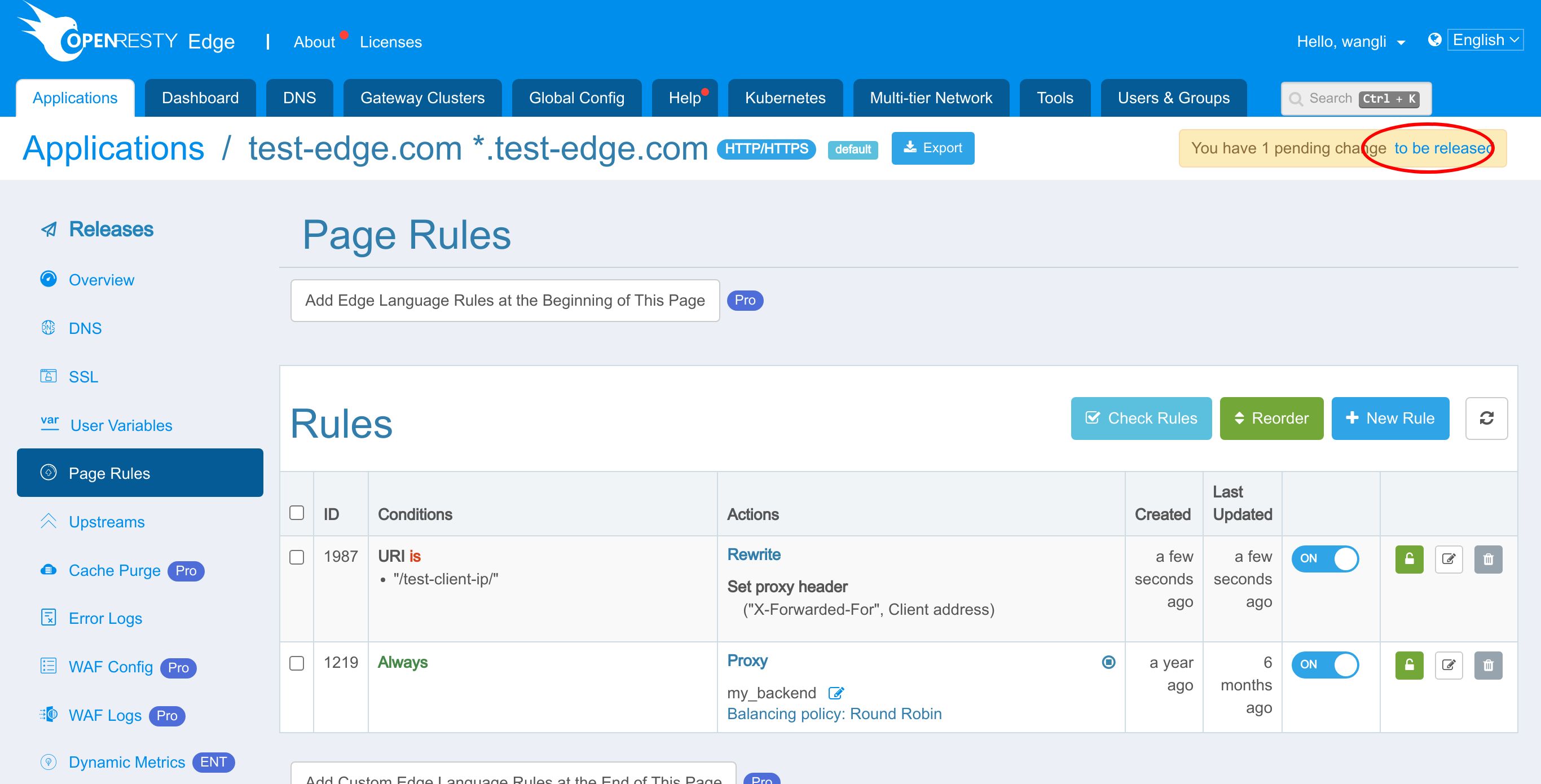
We also have a page rule already defined.
This page rule sets up a reverse proxy to the upstream we just saw.
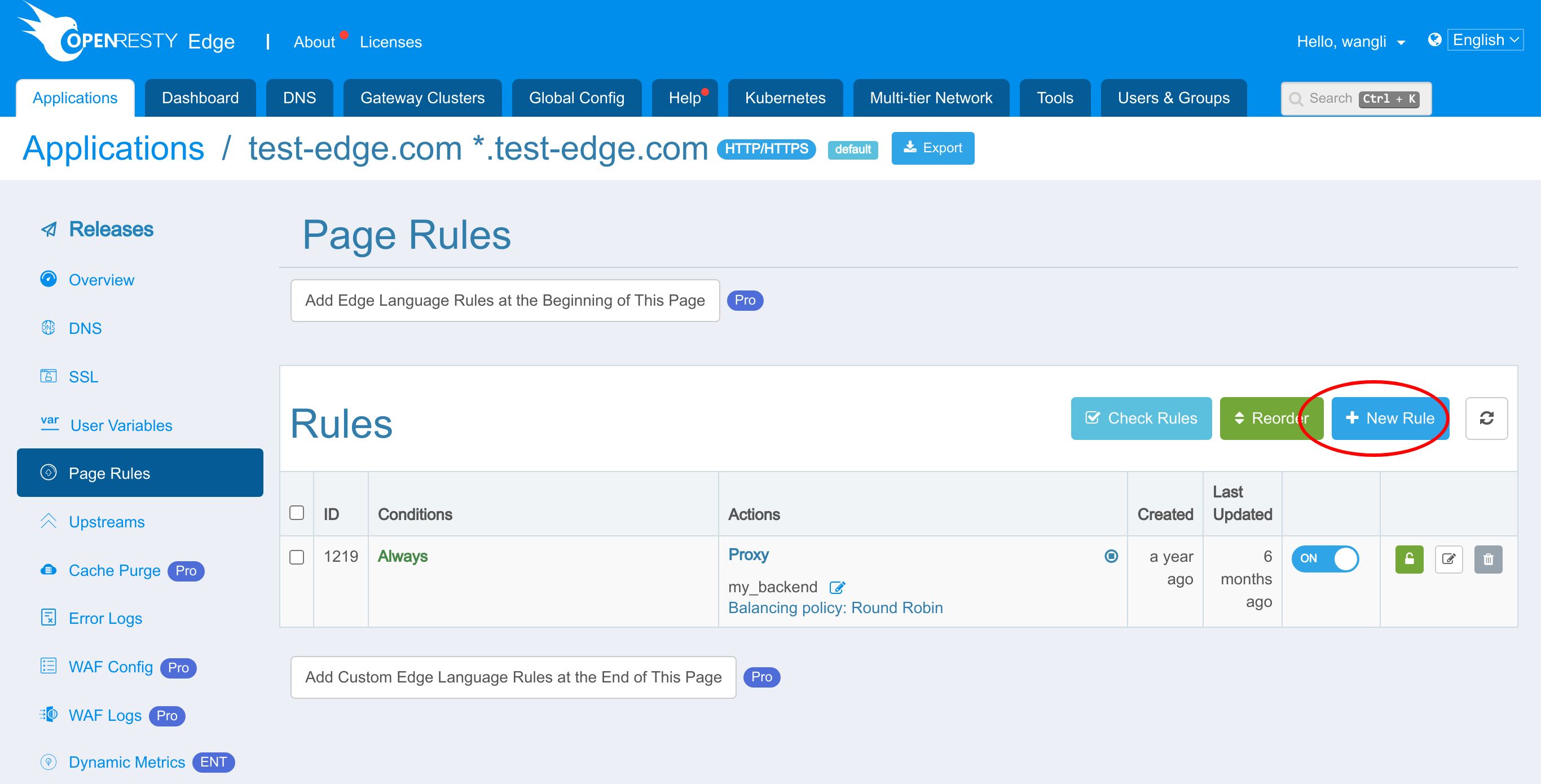
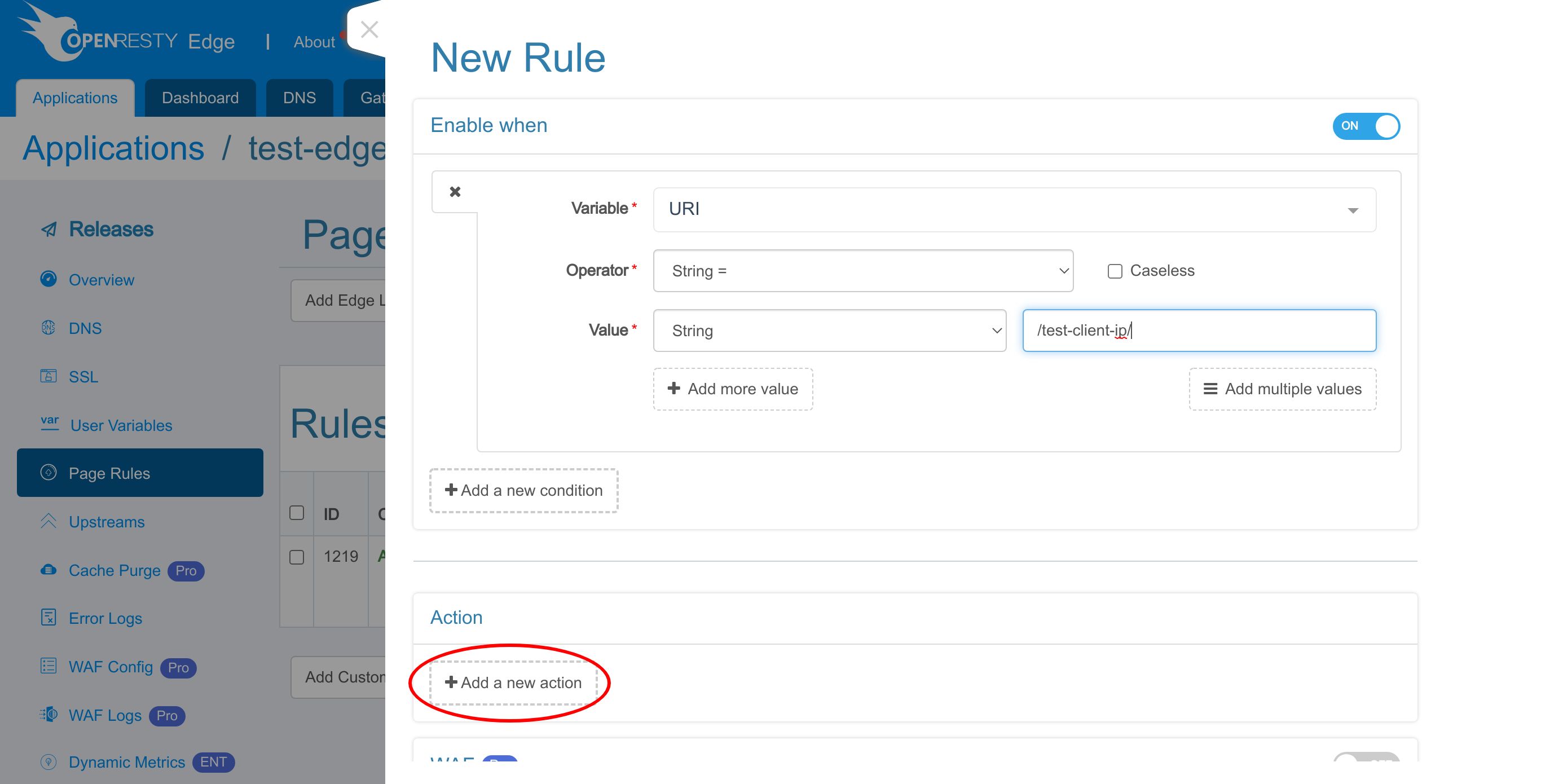
Now let’s add a new page rule to set client ip to the X-Forwarded-For request header.
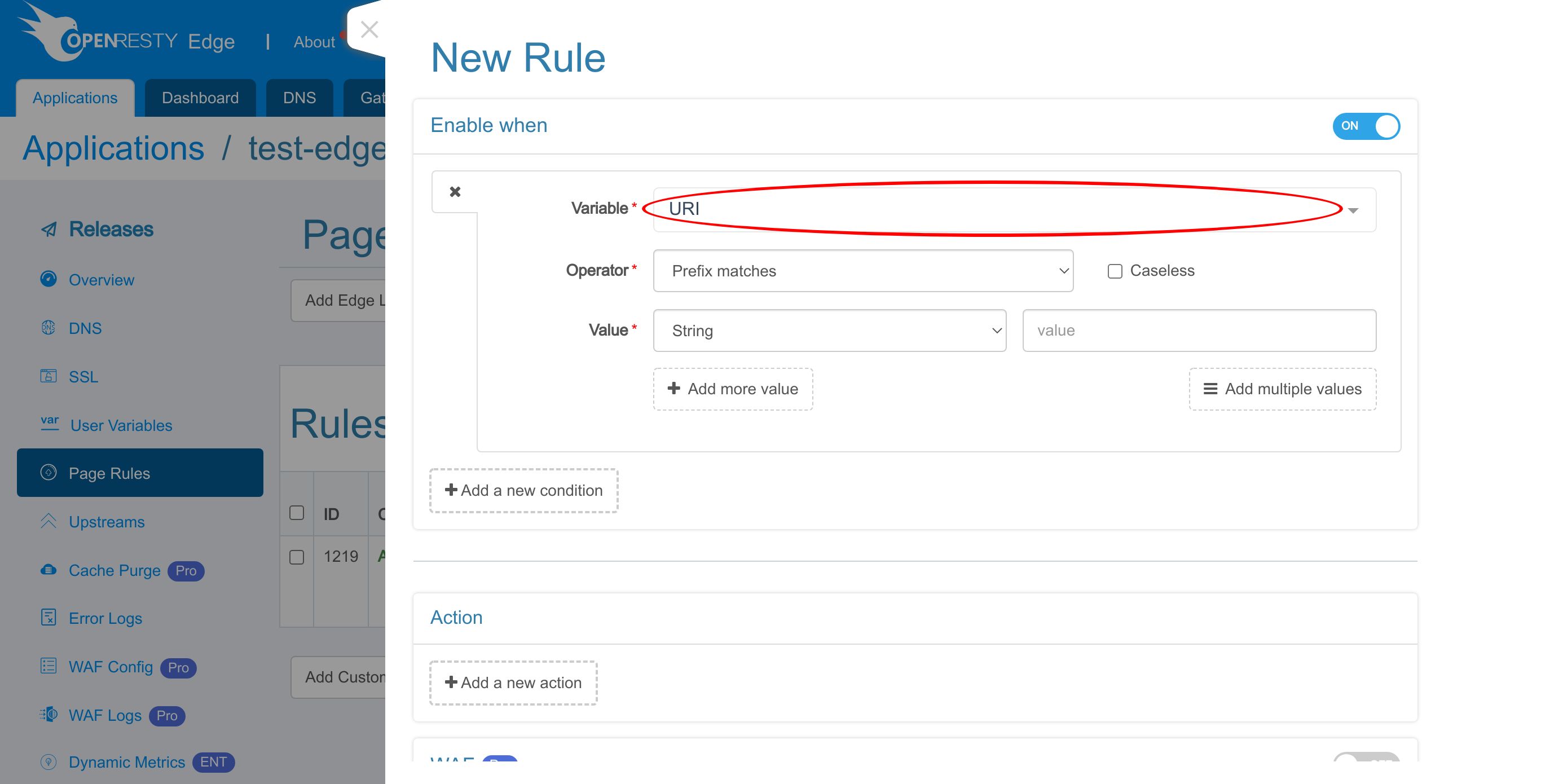
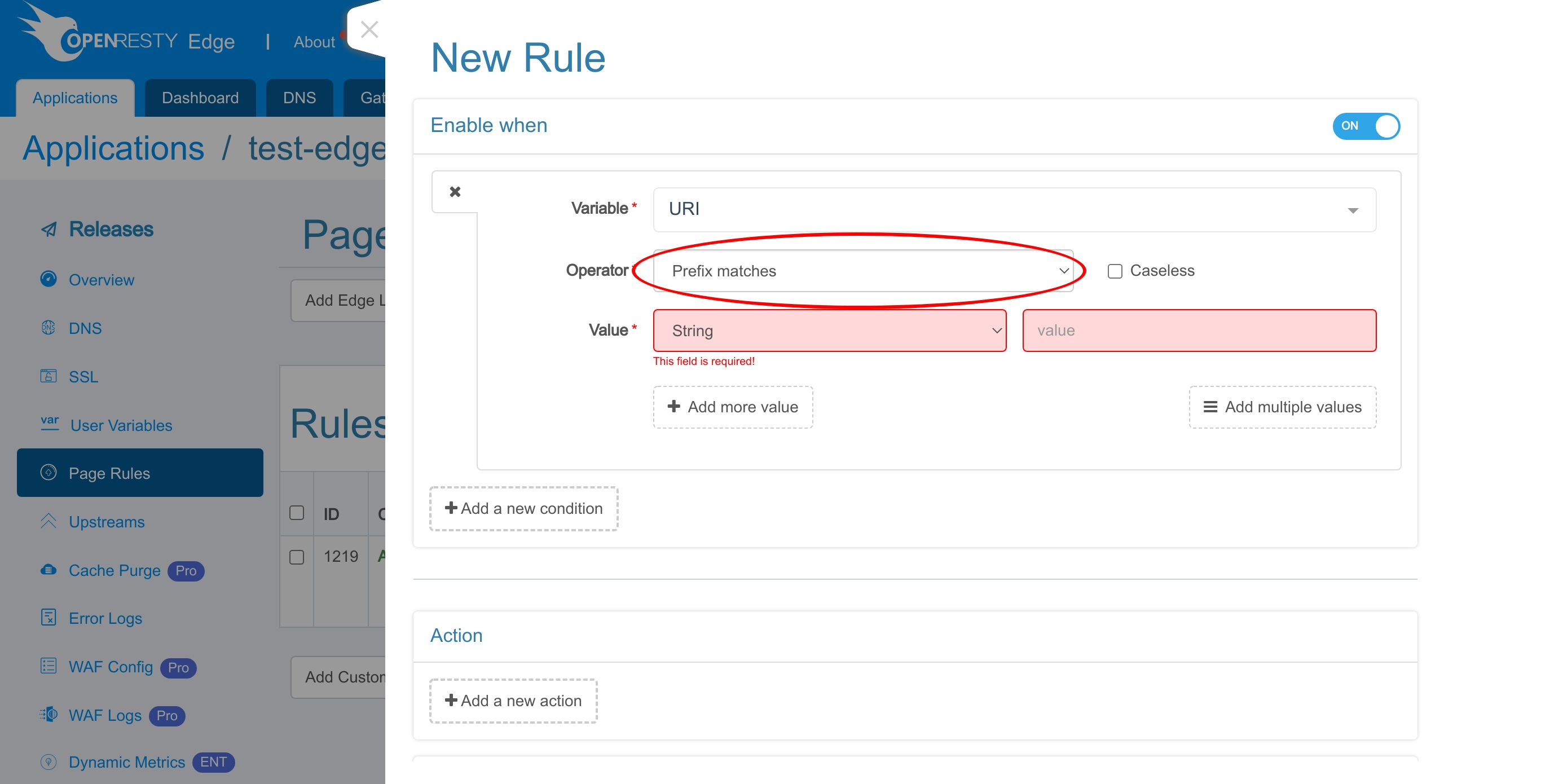
We enable a rule condition to check for the URI /test-client-ip/.
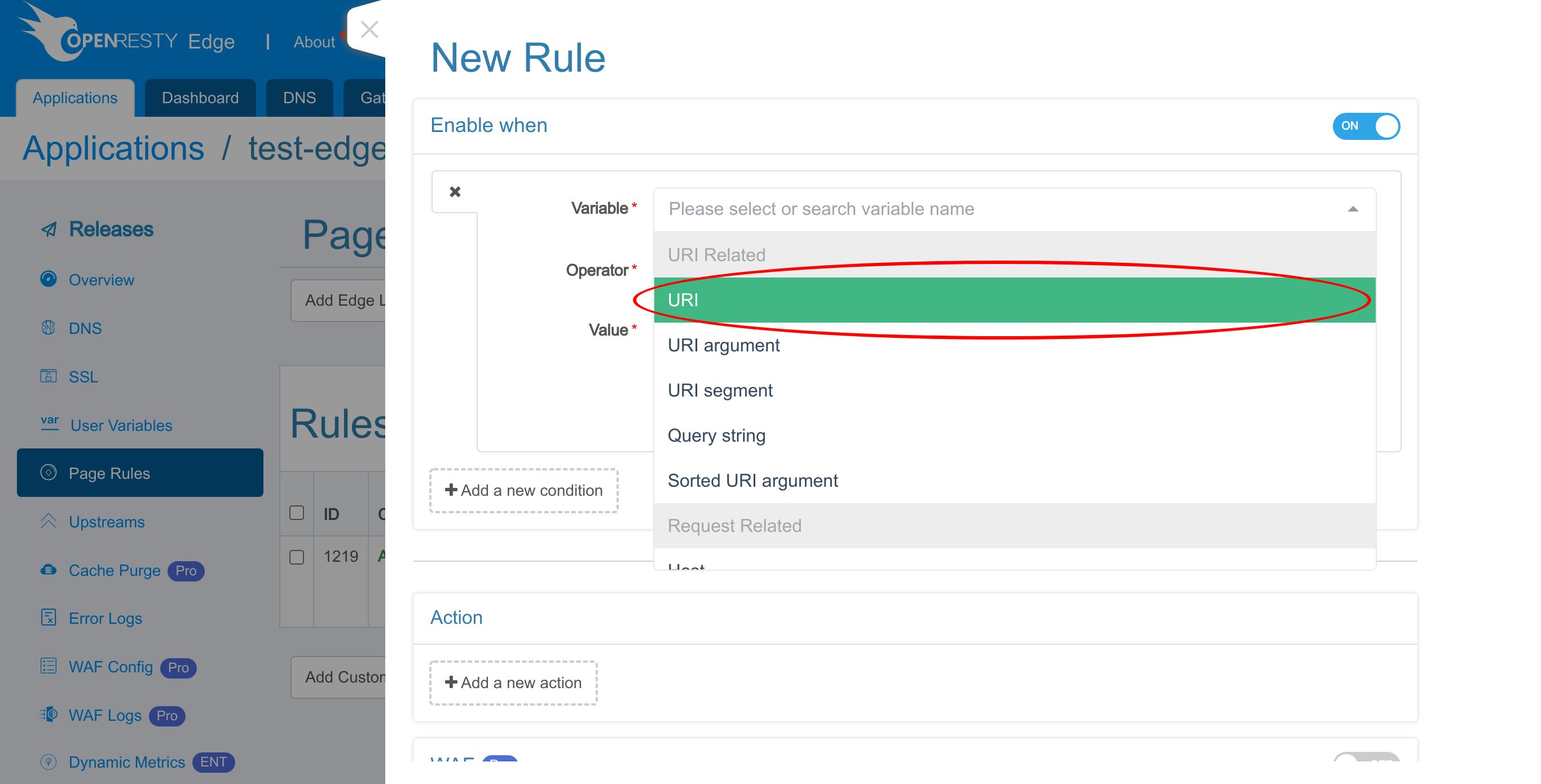
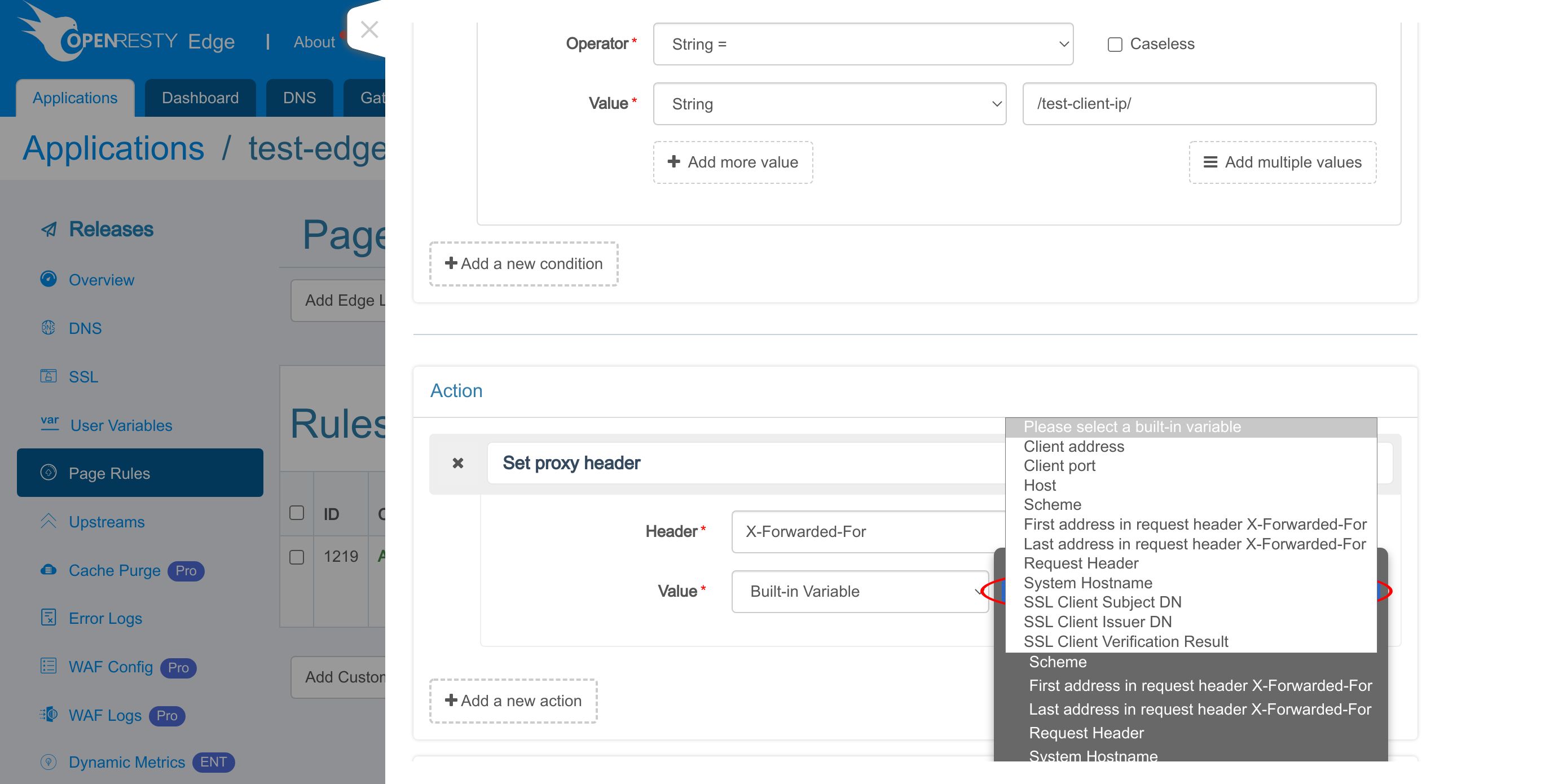
Let’s see all the variables we can choose from.
Select URI.
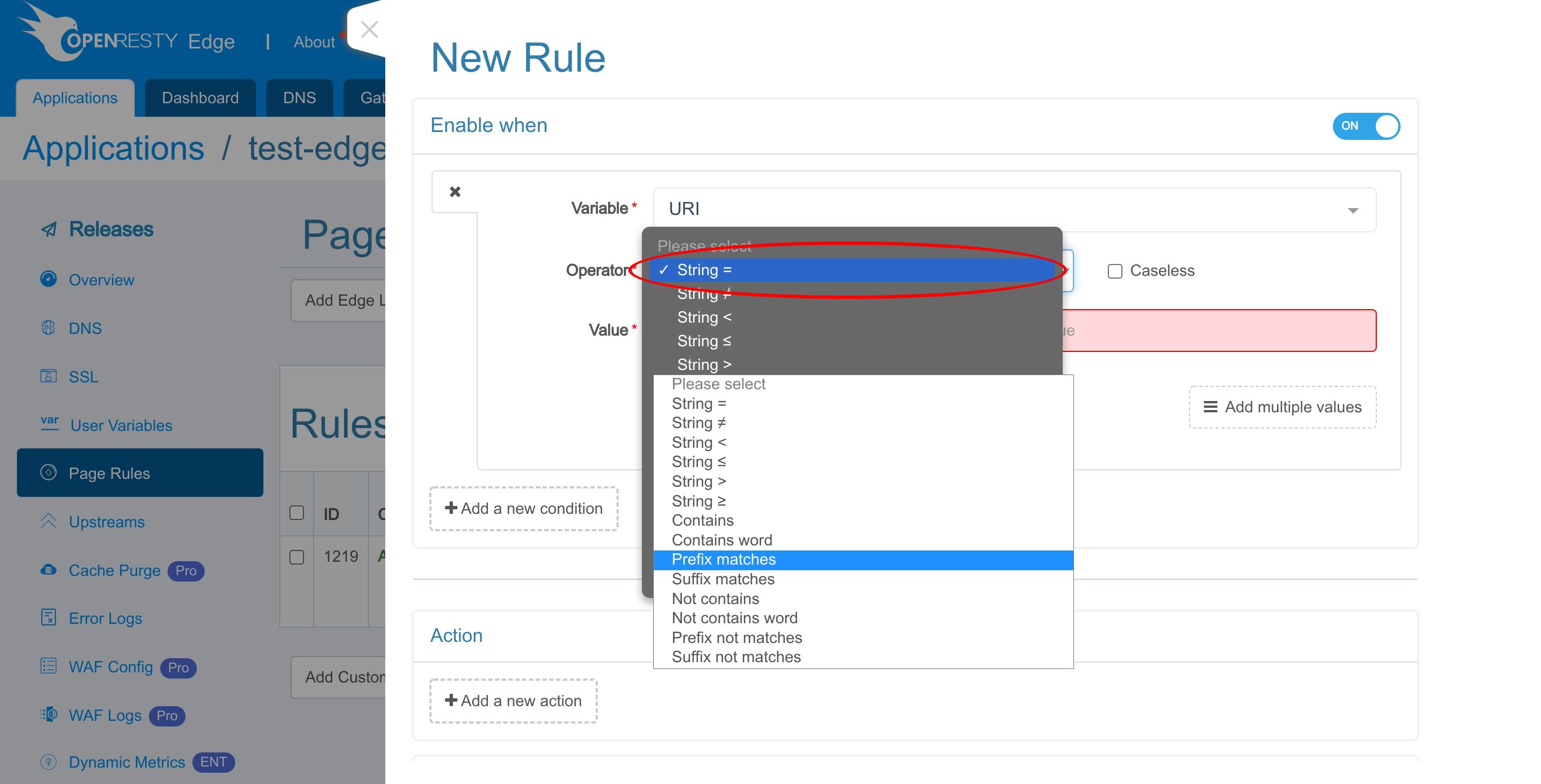
We choose the string equality operator.
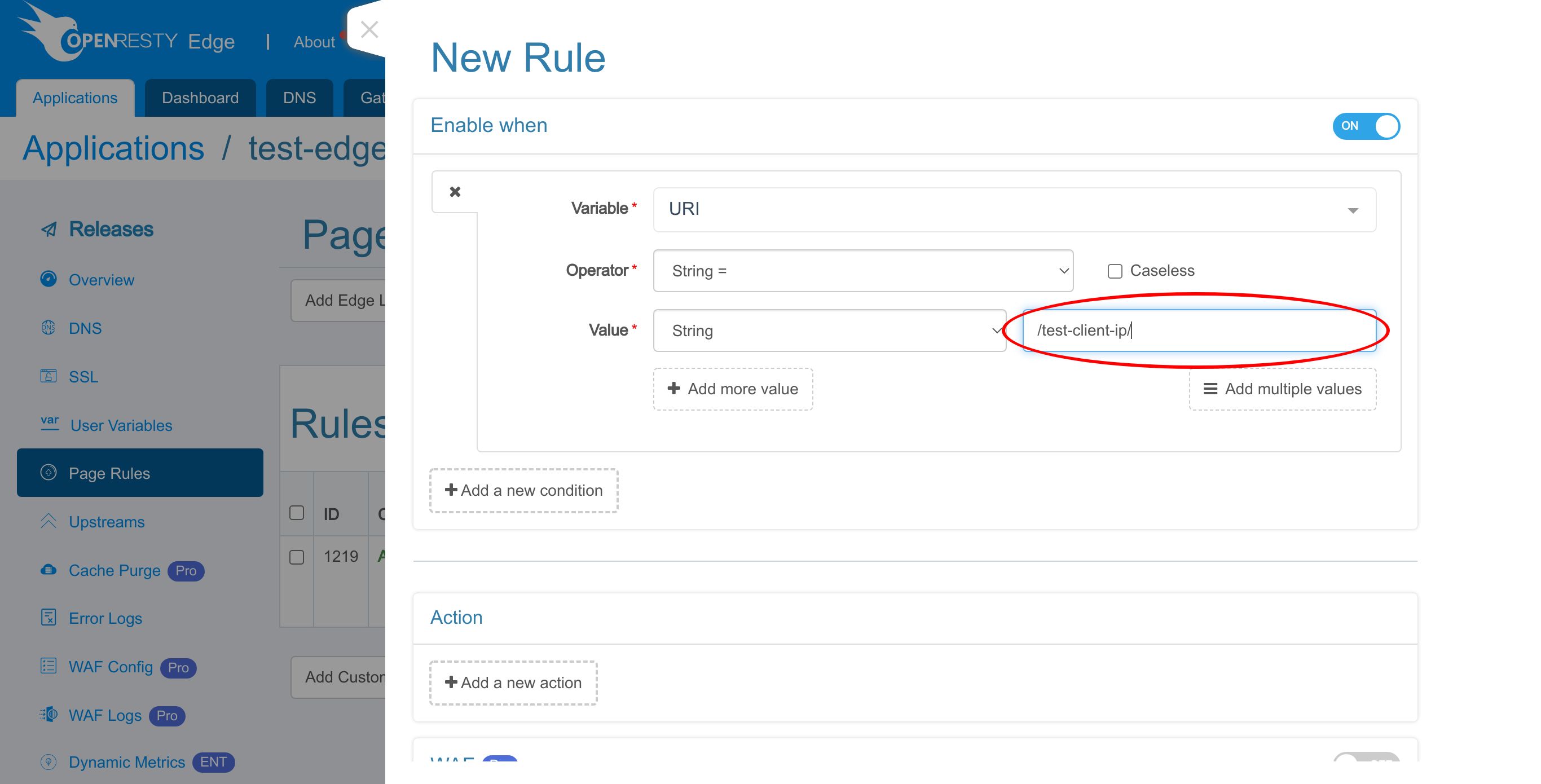
Enter the URI /test-client-ip/.
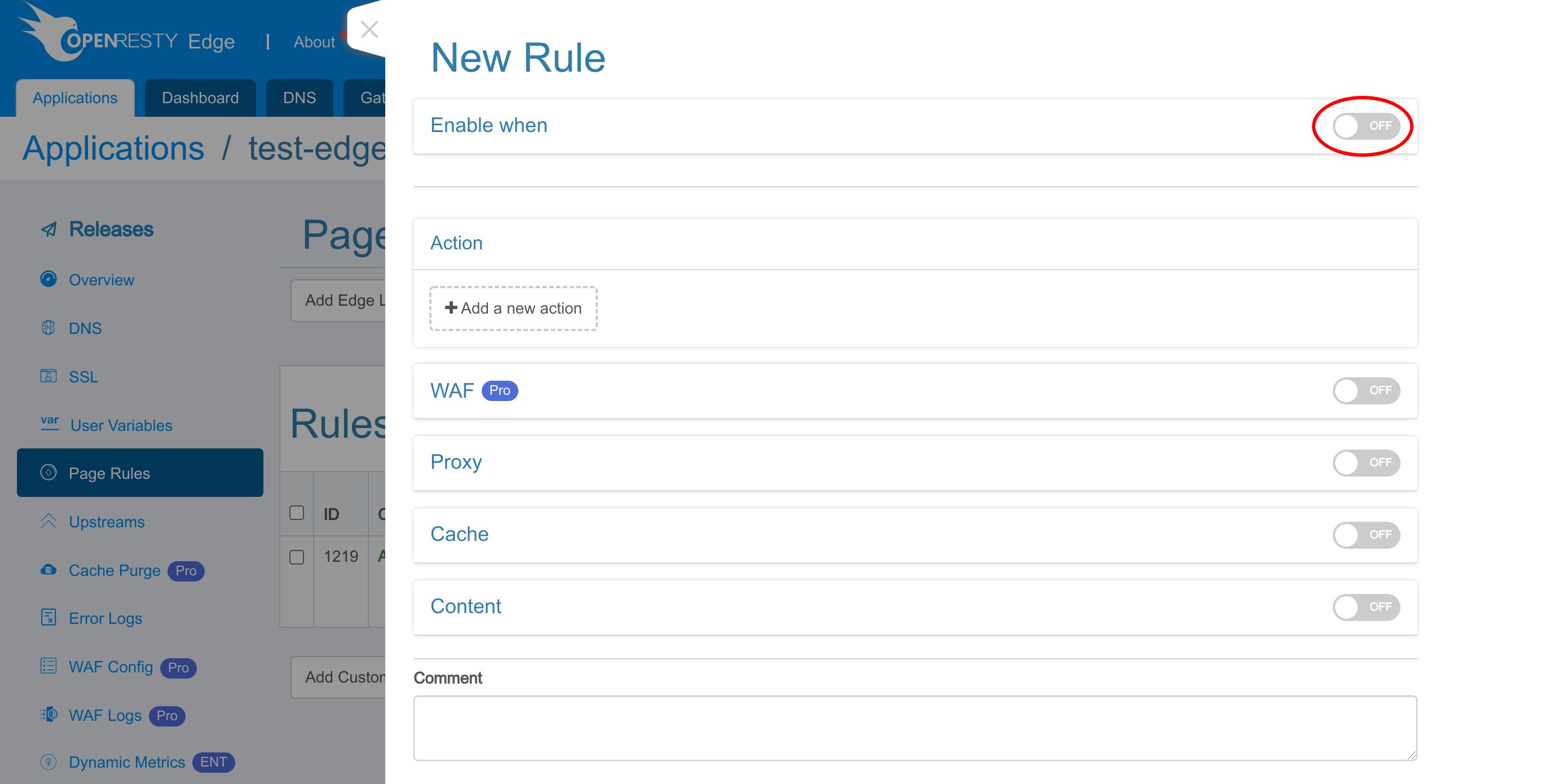
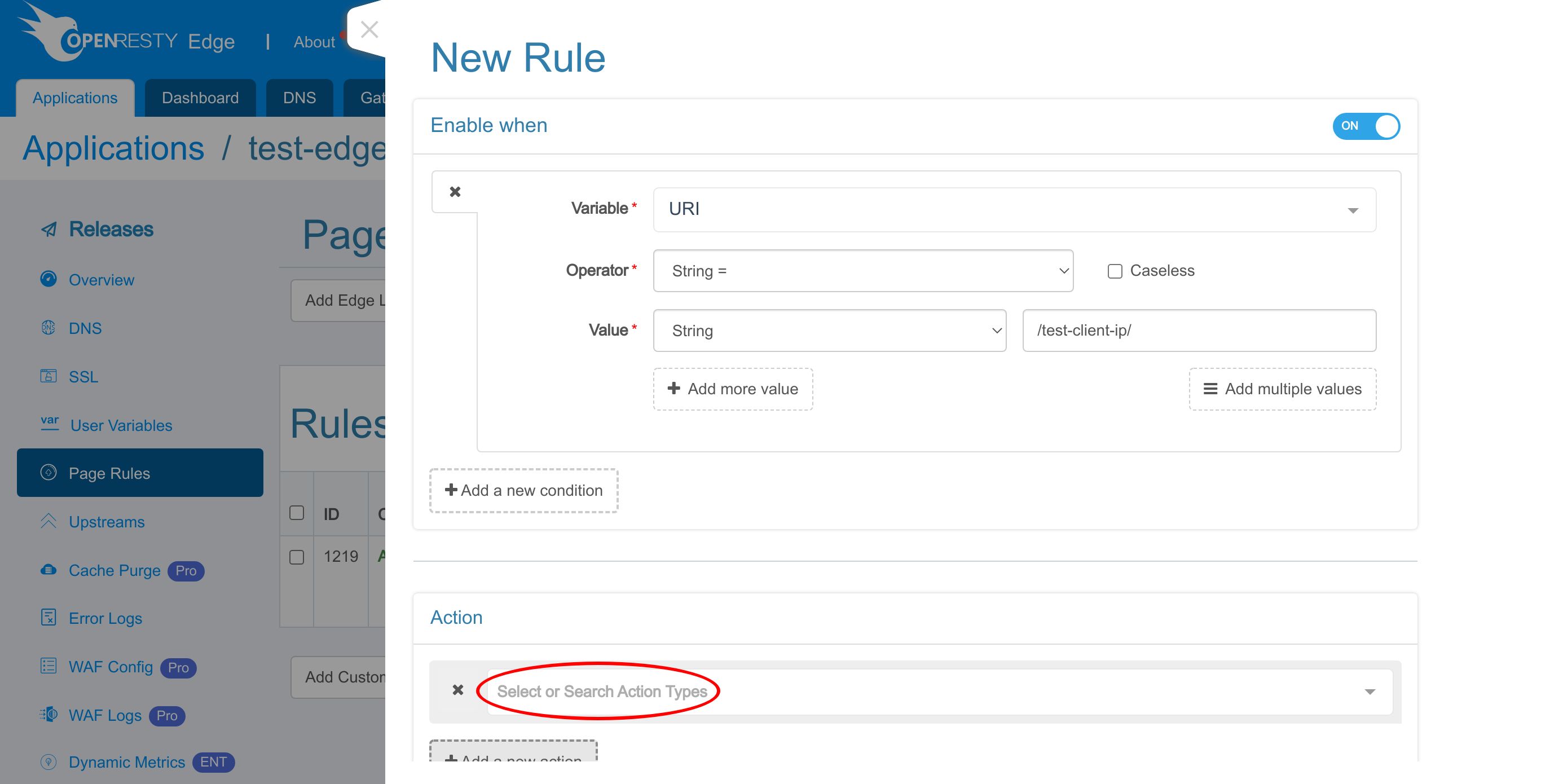
Then add a new action.
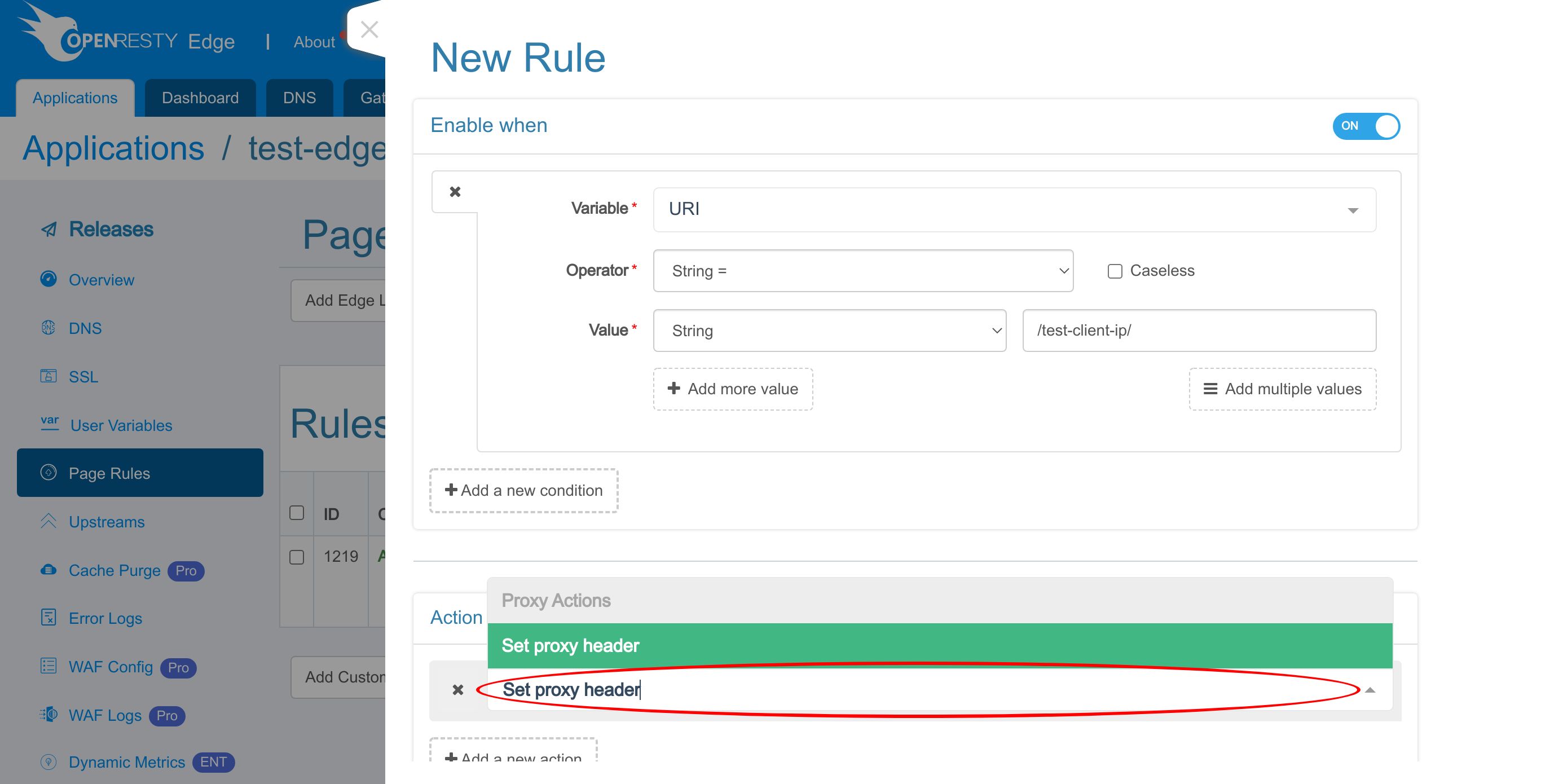
We can search for the action.
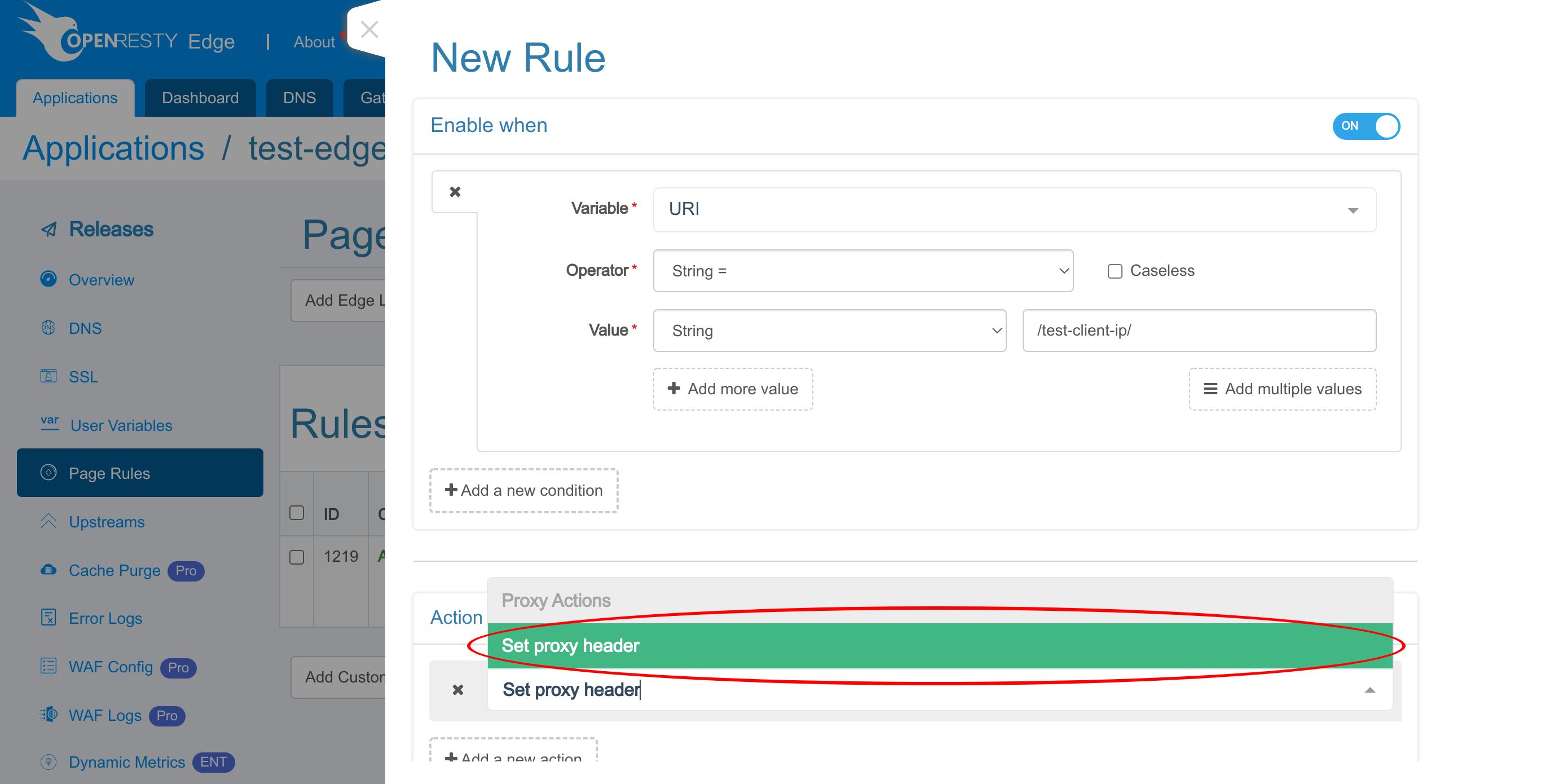
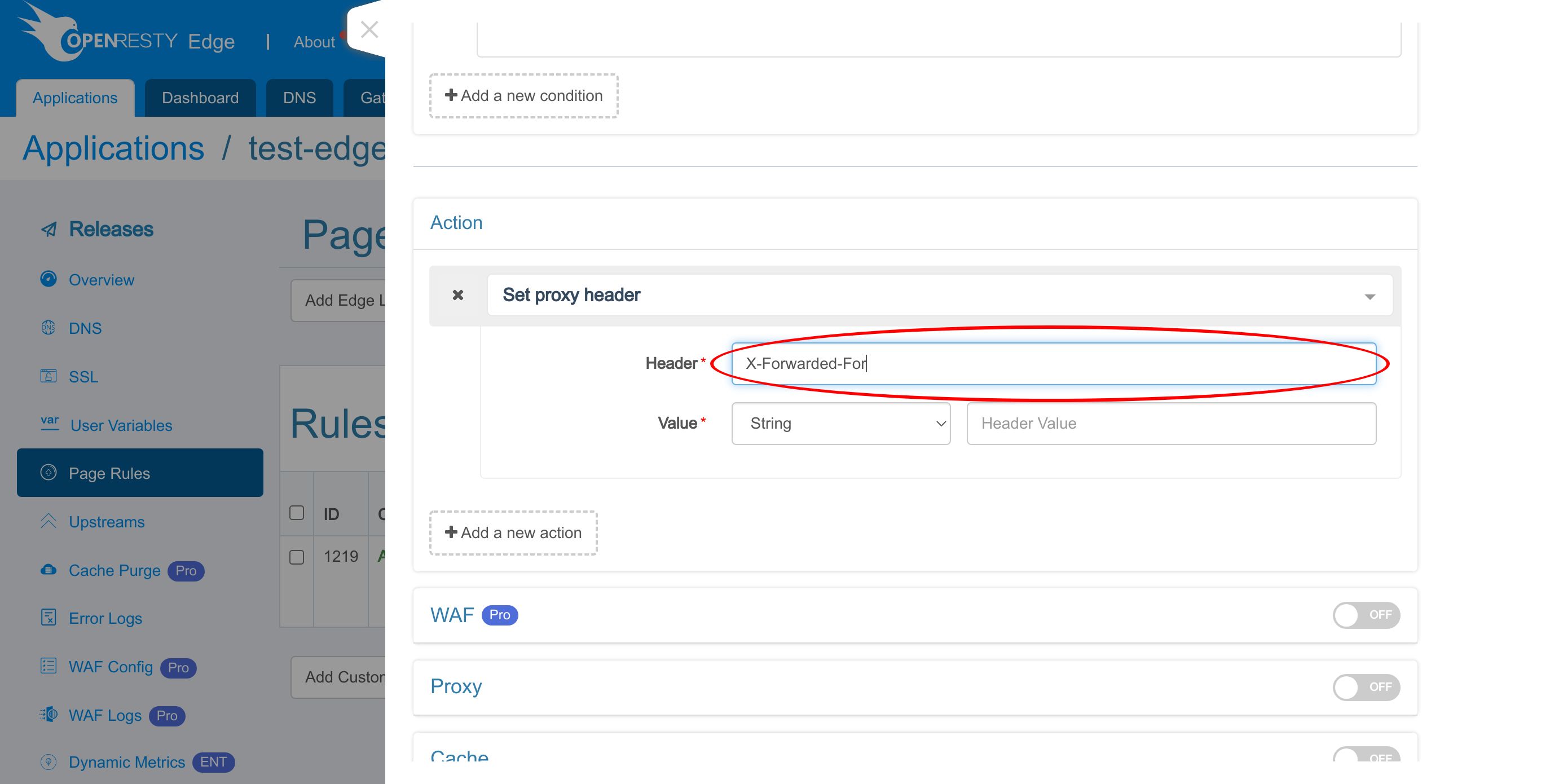
Search for “Set proxy header”.
Select it.
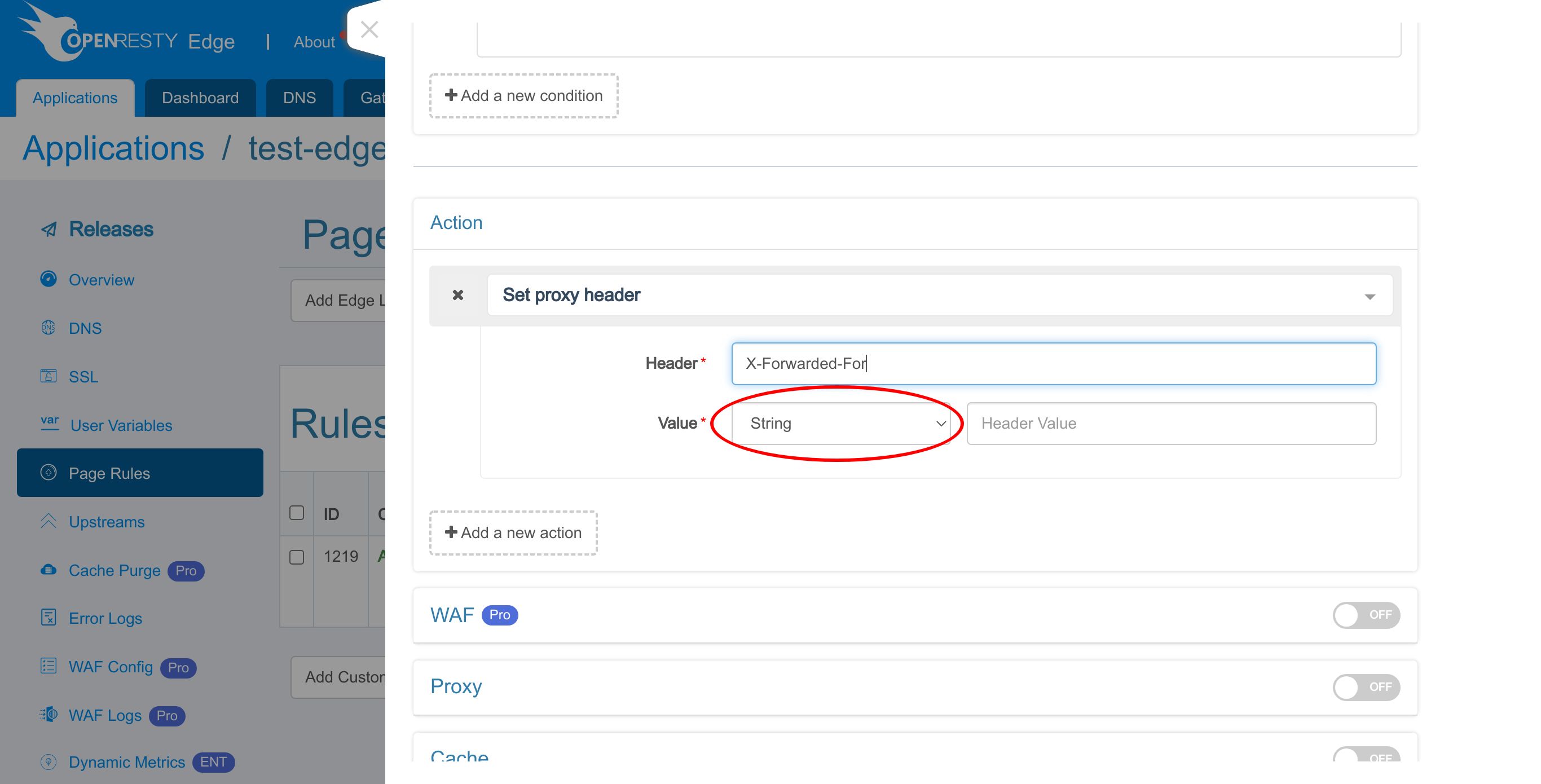
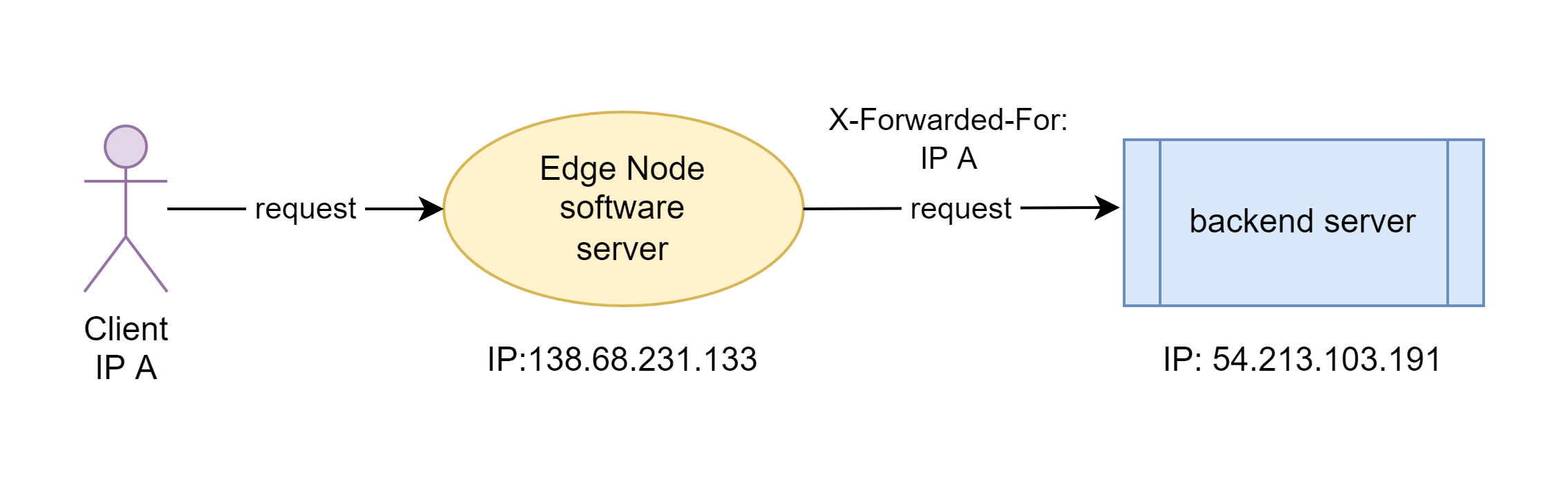
We enter the header name, “X-Forwarded-For”. It’s a commonly used request for this purpose. You can use any other names you like, like X-Real-IP.
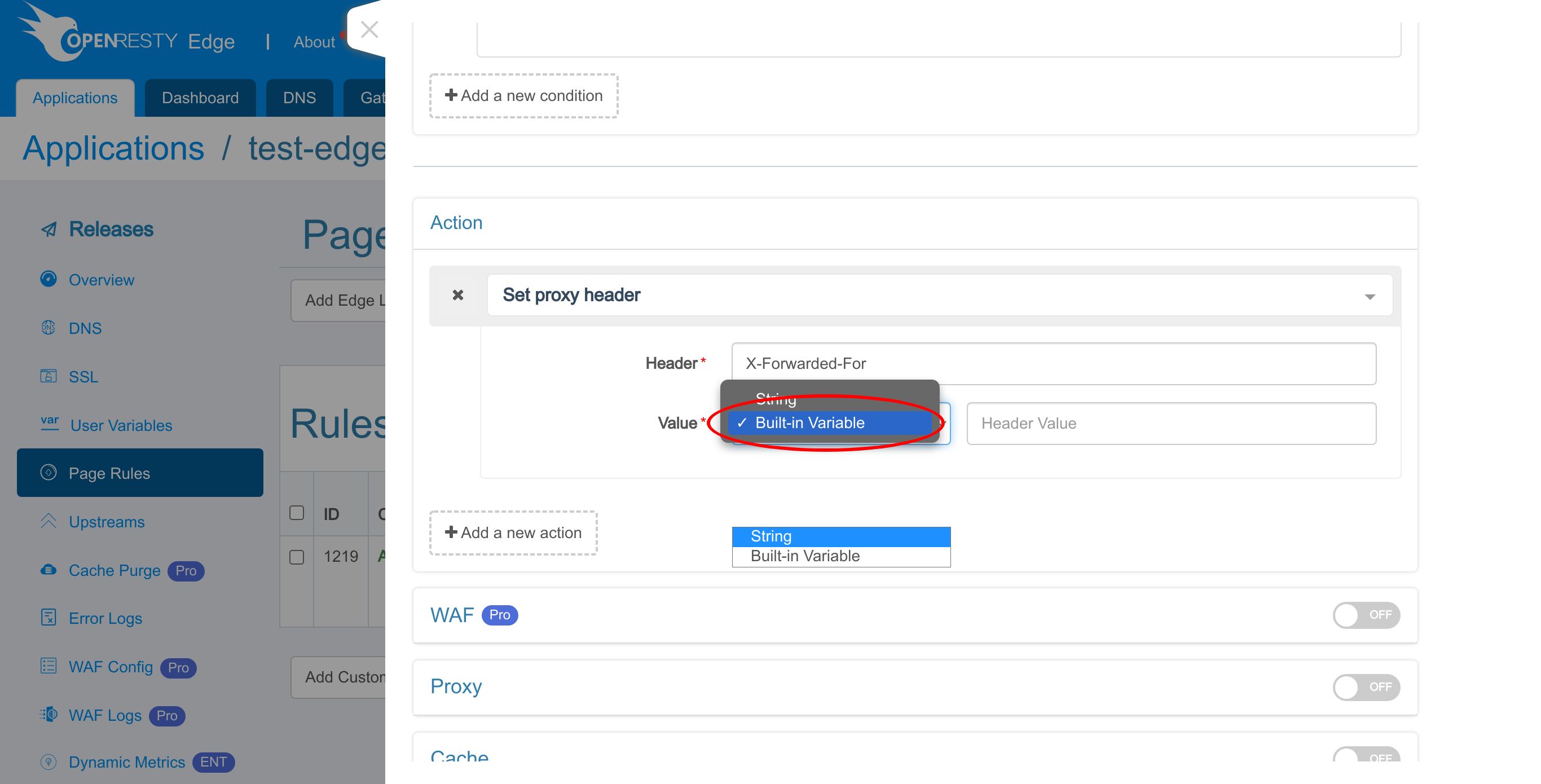
Choose the value type. We can specify a literal string value for the request.
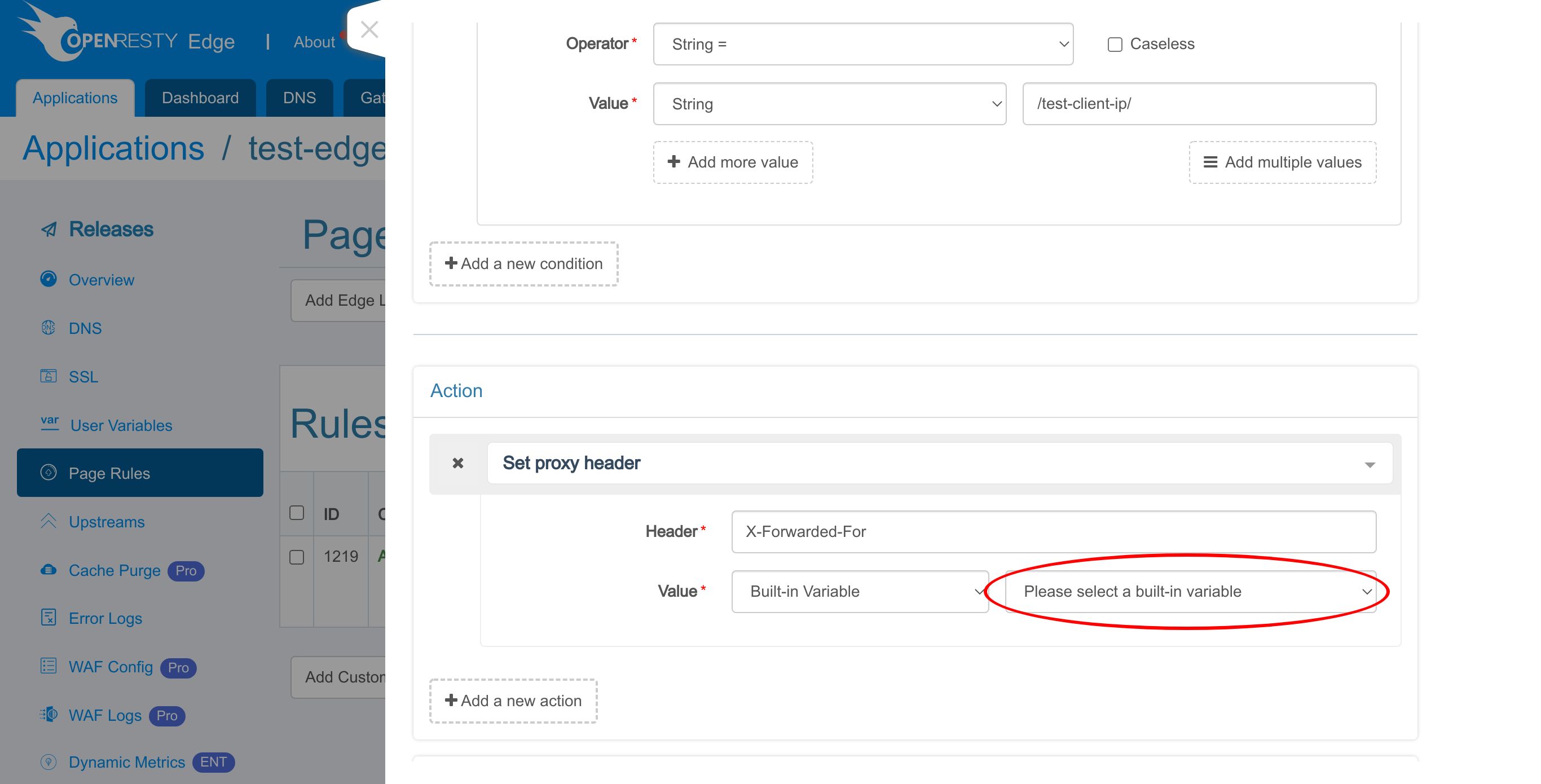
or specify a built-in variable provided by OpenResty Edge.
It supports several built-in variables and more are coming in the future.
We choose Client address here.
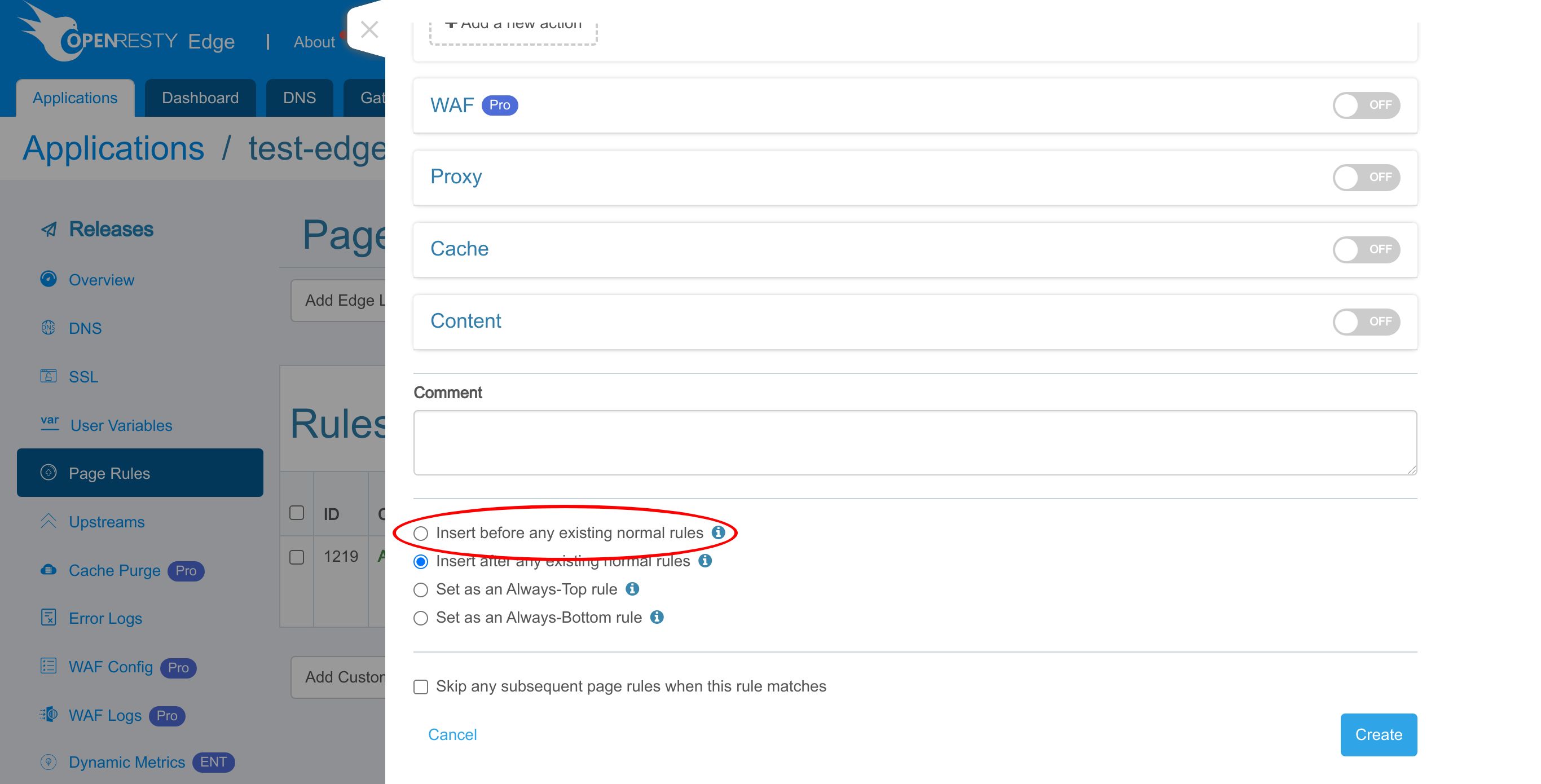
We make sure this rule runs before any existing normal rules.
Save our changes to this page rule.
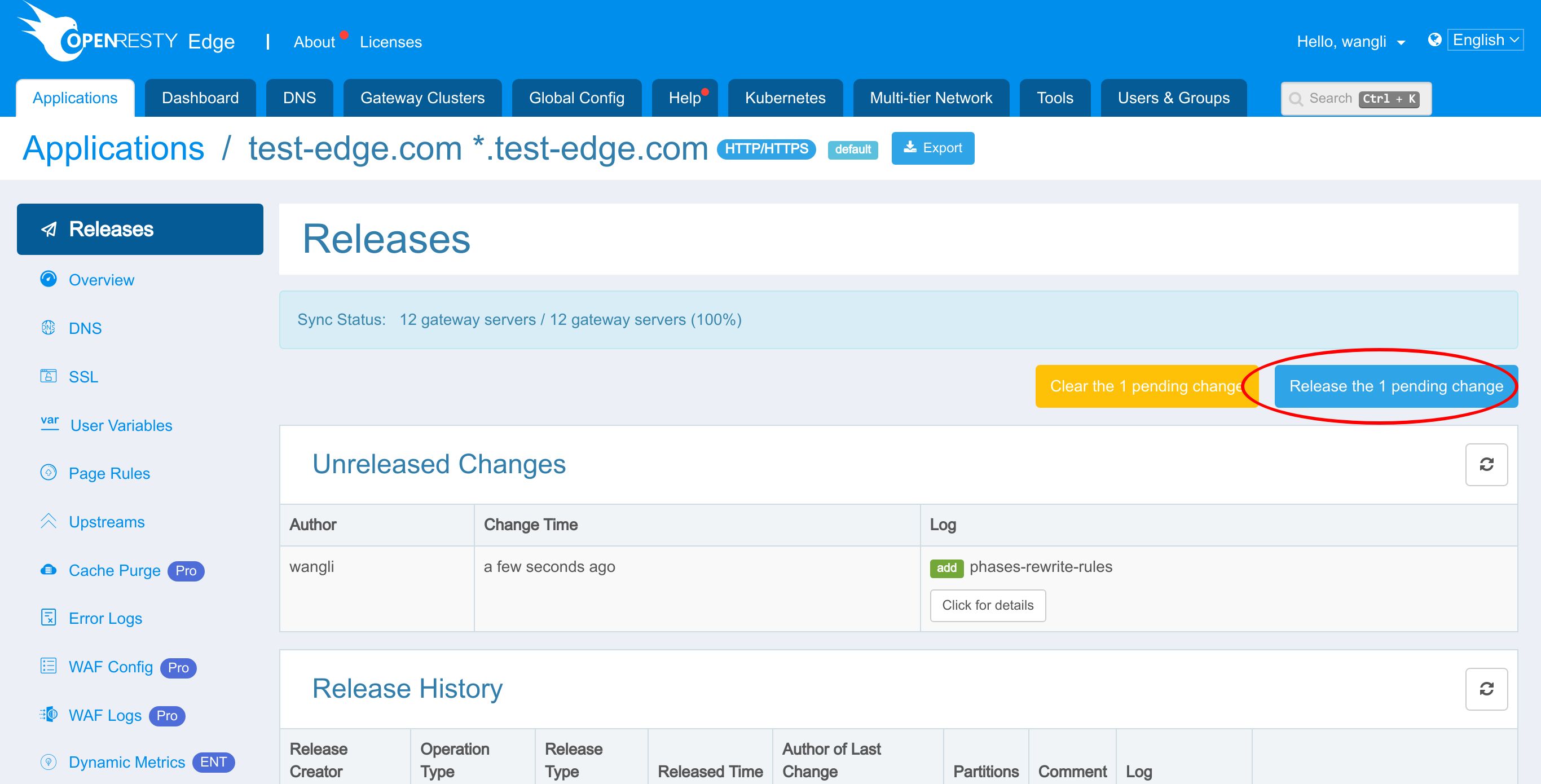
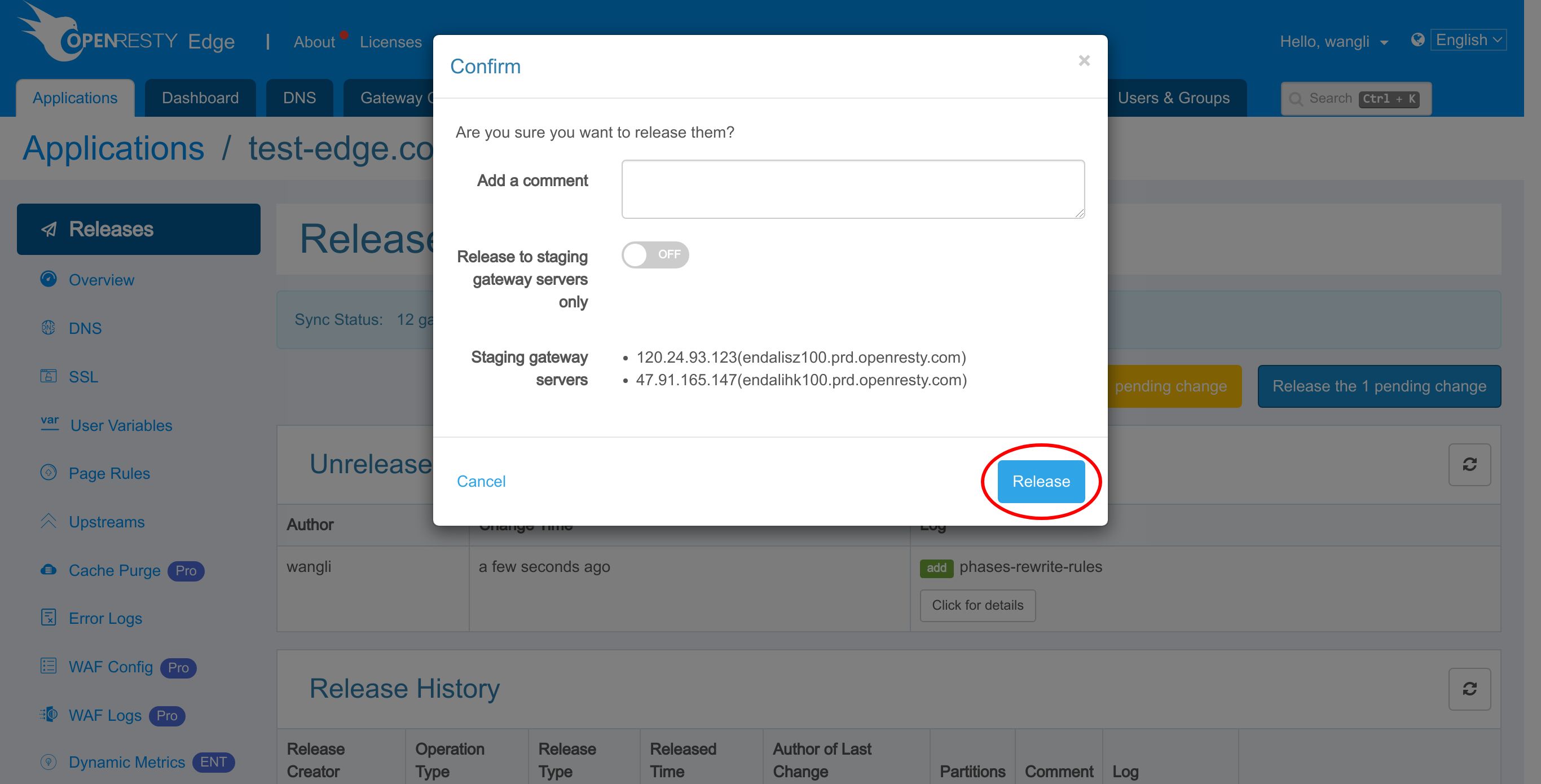
We need to make a new release to push out our new changes, as always.
Click on this button.
Ship it!
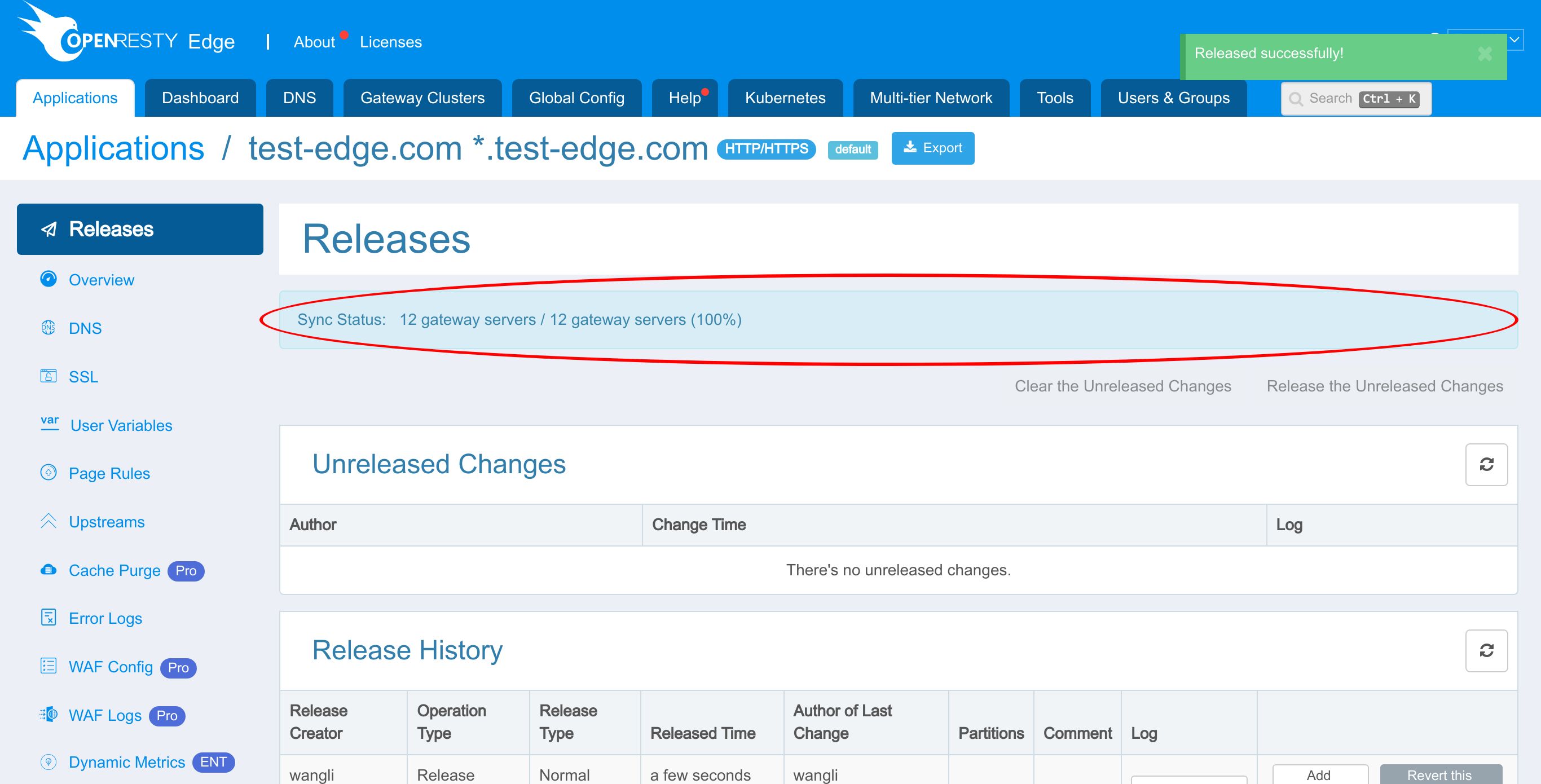
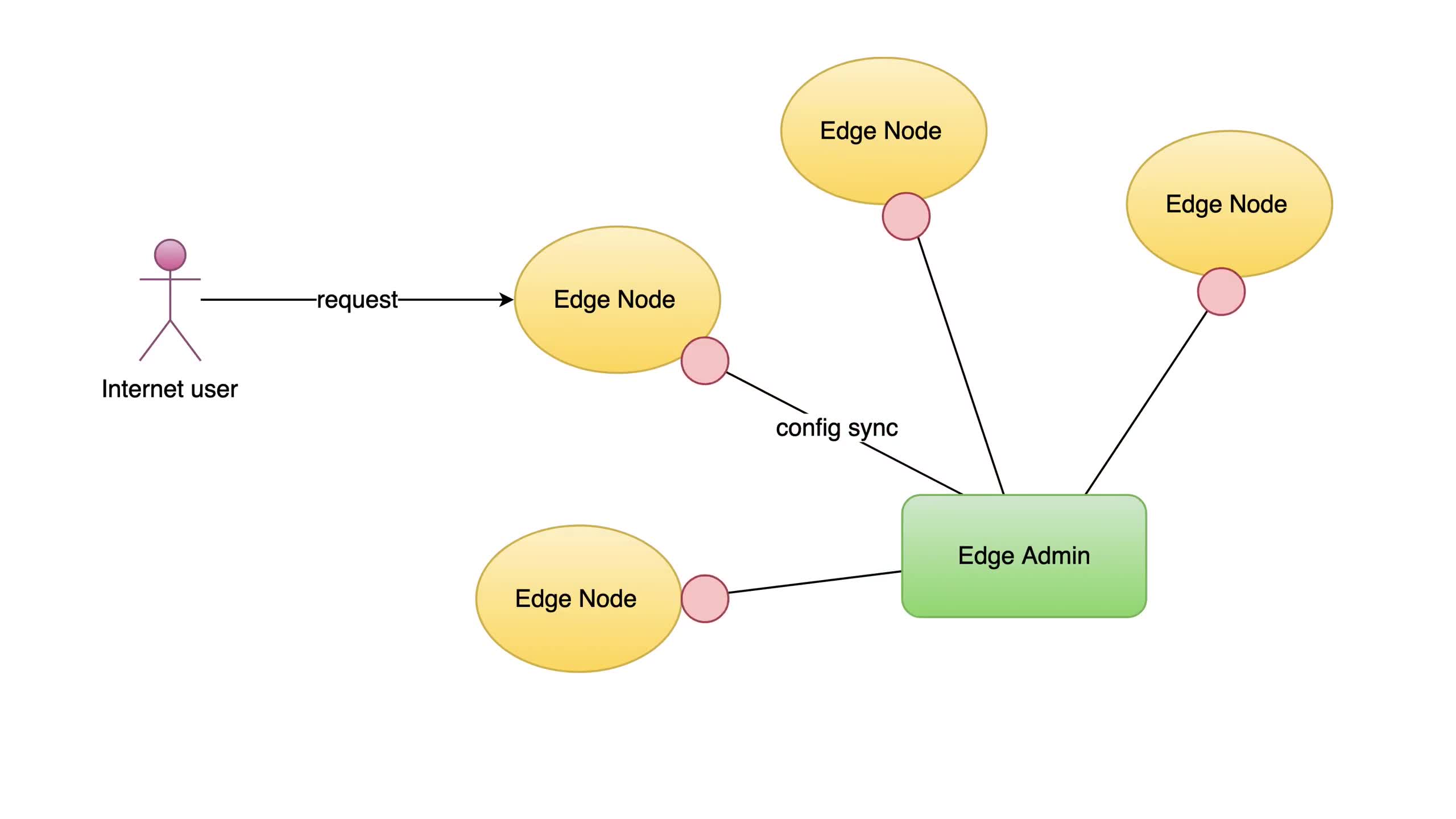
Our new release is now synchronized to all our gateway servers.
Now the new page rule has been pushed to all the gateway clusters and servers.
Our configuration changes do NOT require server reload, restart, or binary upgrade. So it’s very efficient and scalable.
Test
We’ll then send test requests to the gateway servers. And then we check the “X-Forwarded-For” request header received by the backend server.
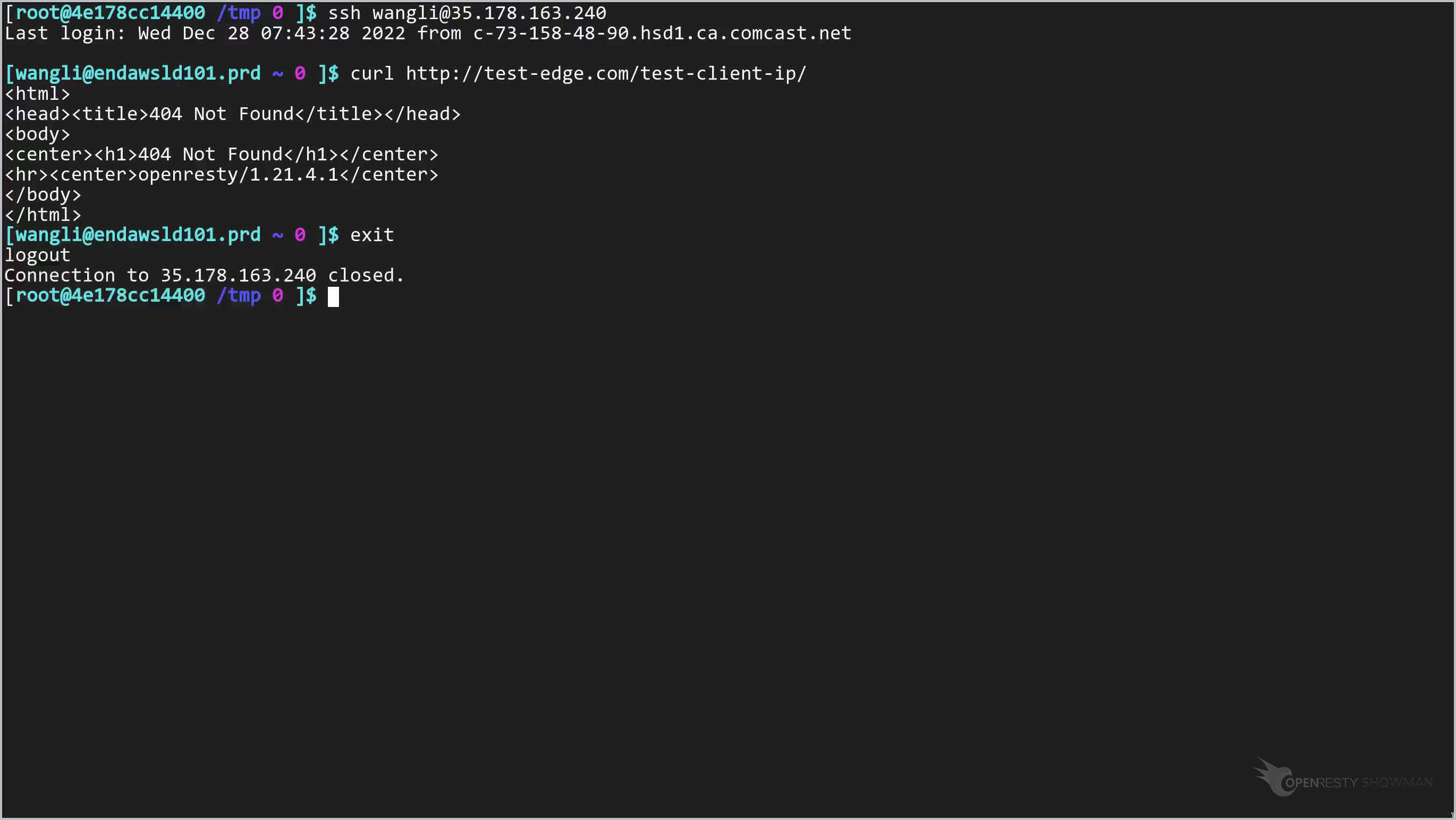
On the terminal, we log onto a remote server in London, UK.
Note the IP address of the server ends of .240.
Log onto the server.
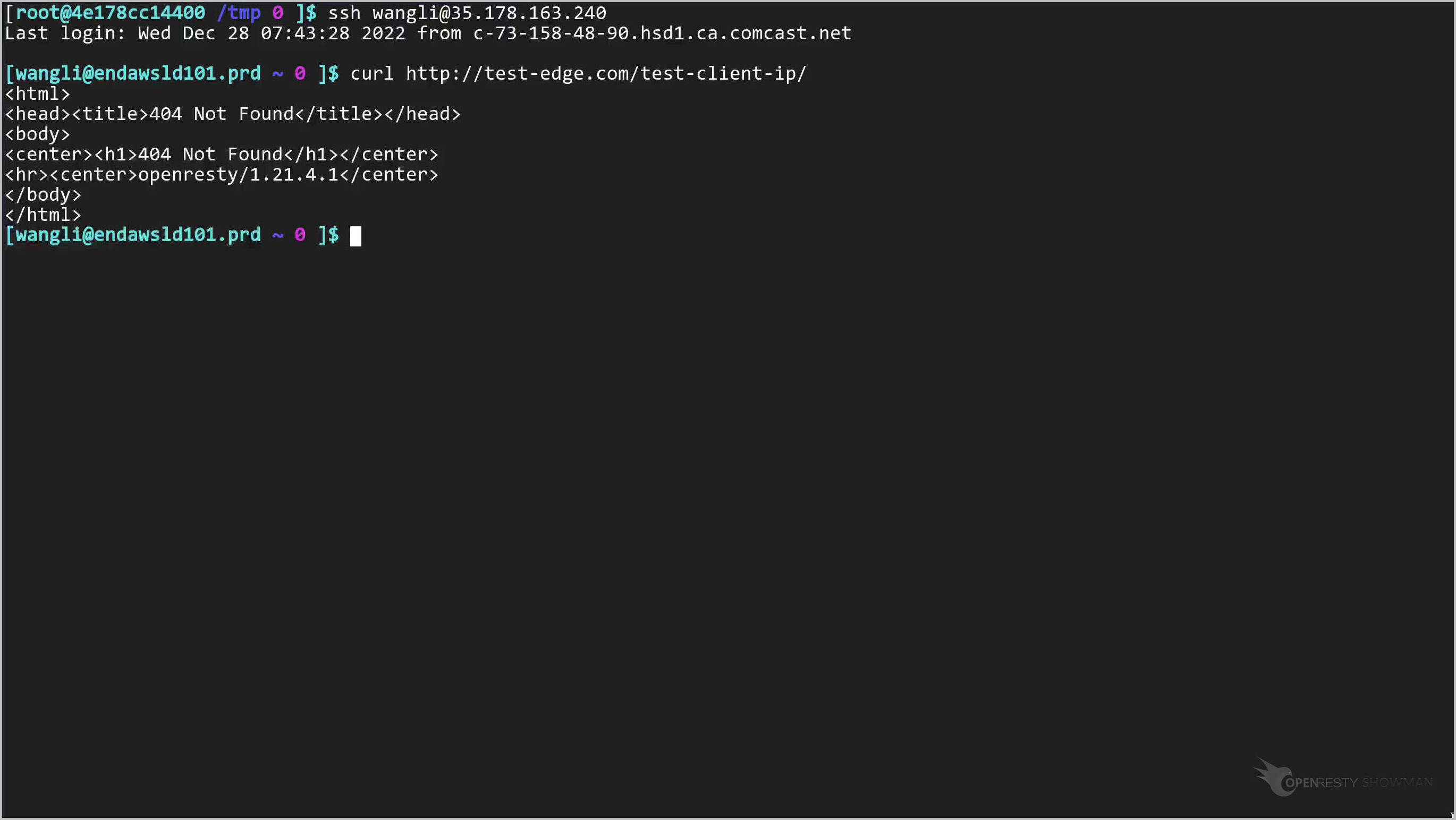
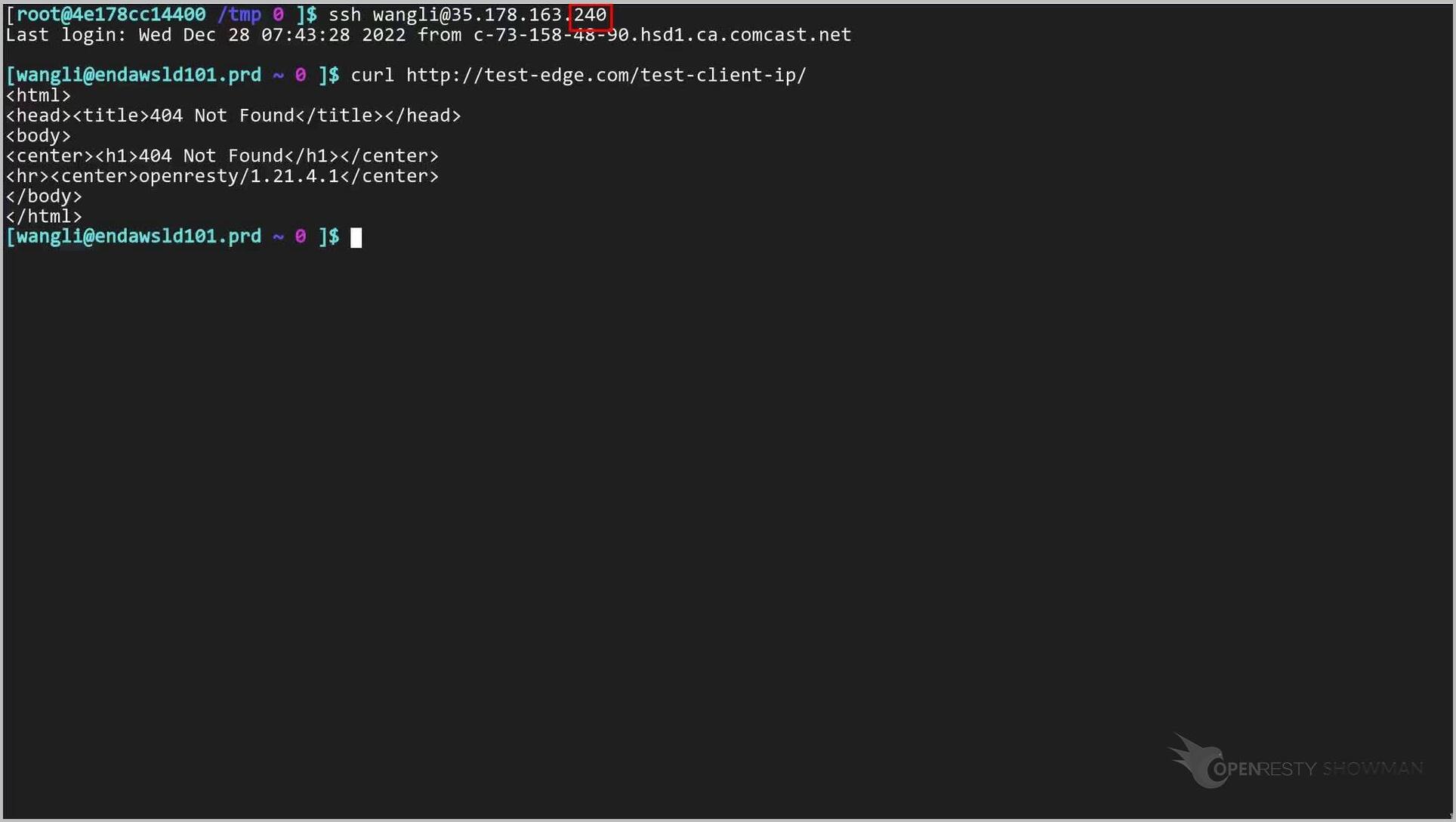
Send an HTTP request with the curl command-line utility.
curl http://test-edge.com/test-client-ip/
So the real client IP for this request should also end with .240.
Quit the server.
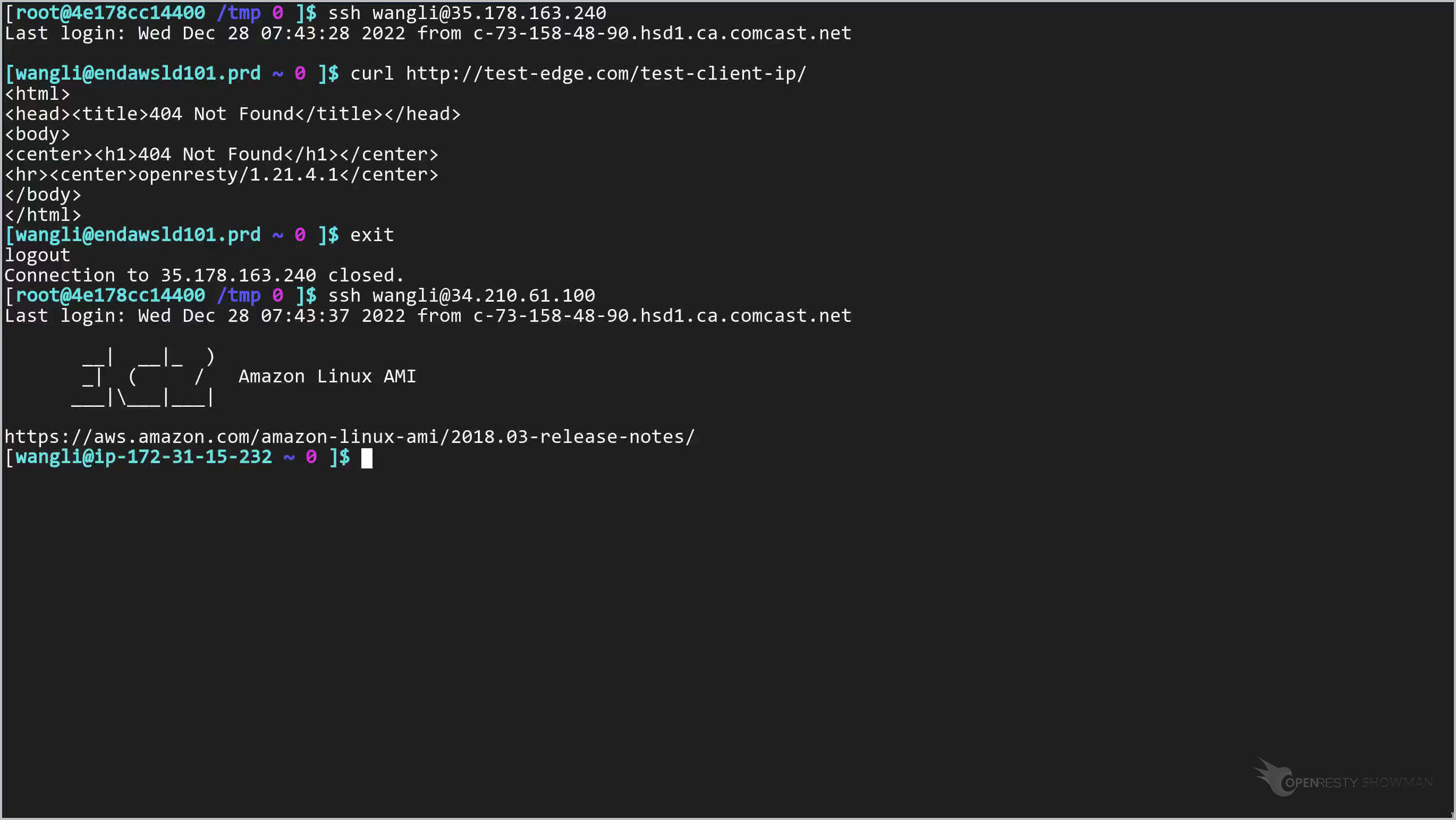
Then we log into the backend server of the IP address ending with .100:
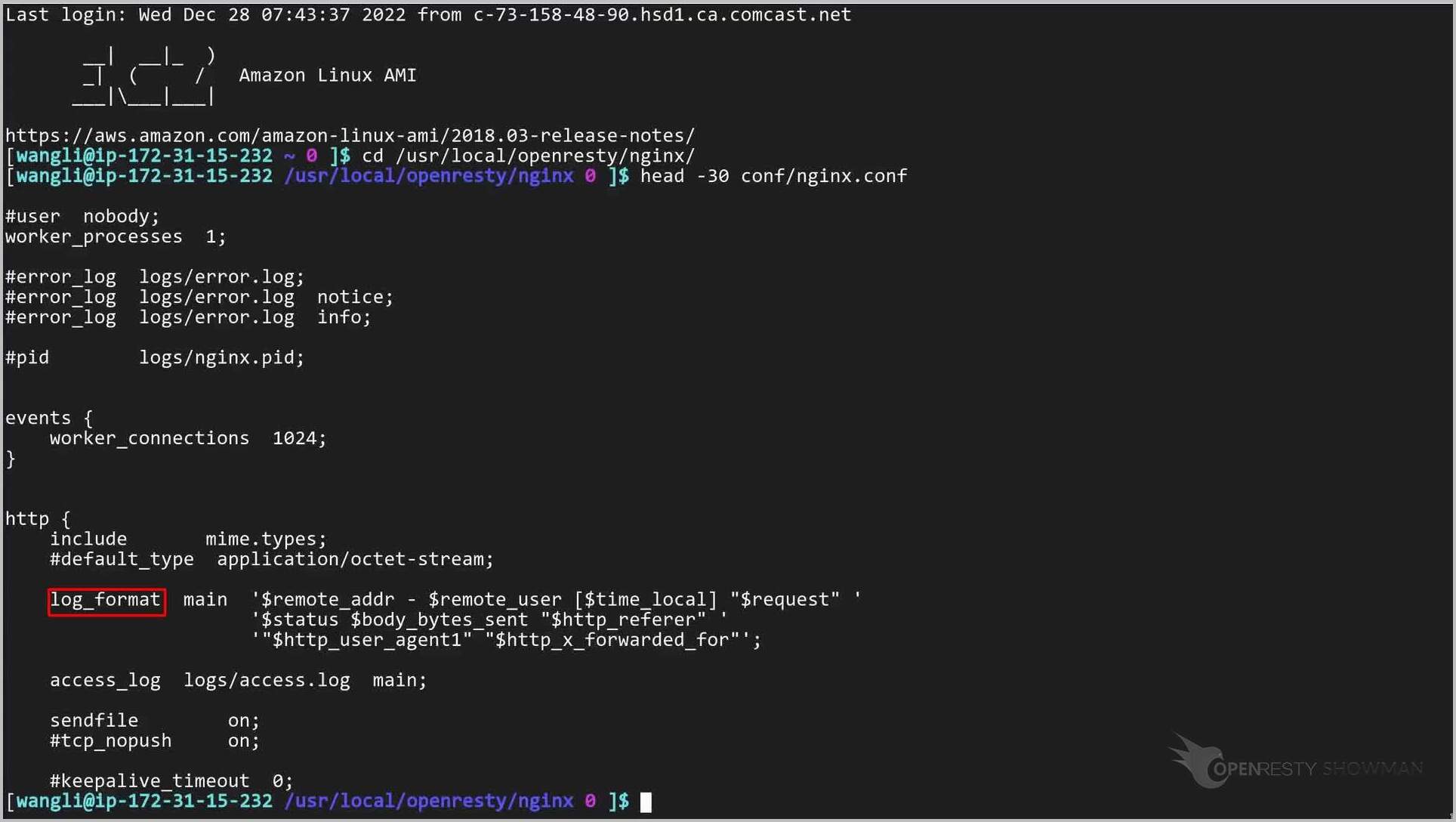
Let’s see the access log format defined in the Nginx configuration file.
cd /usr/local/openresty/nginx/
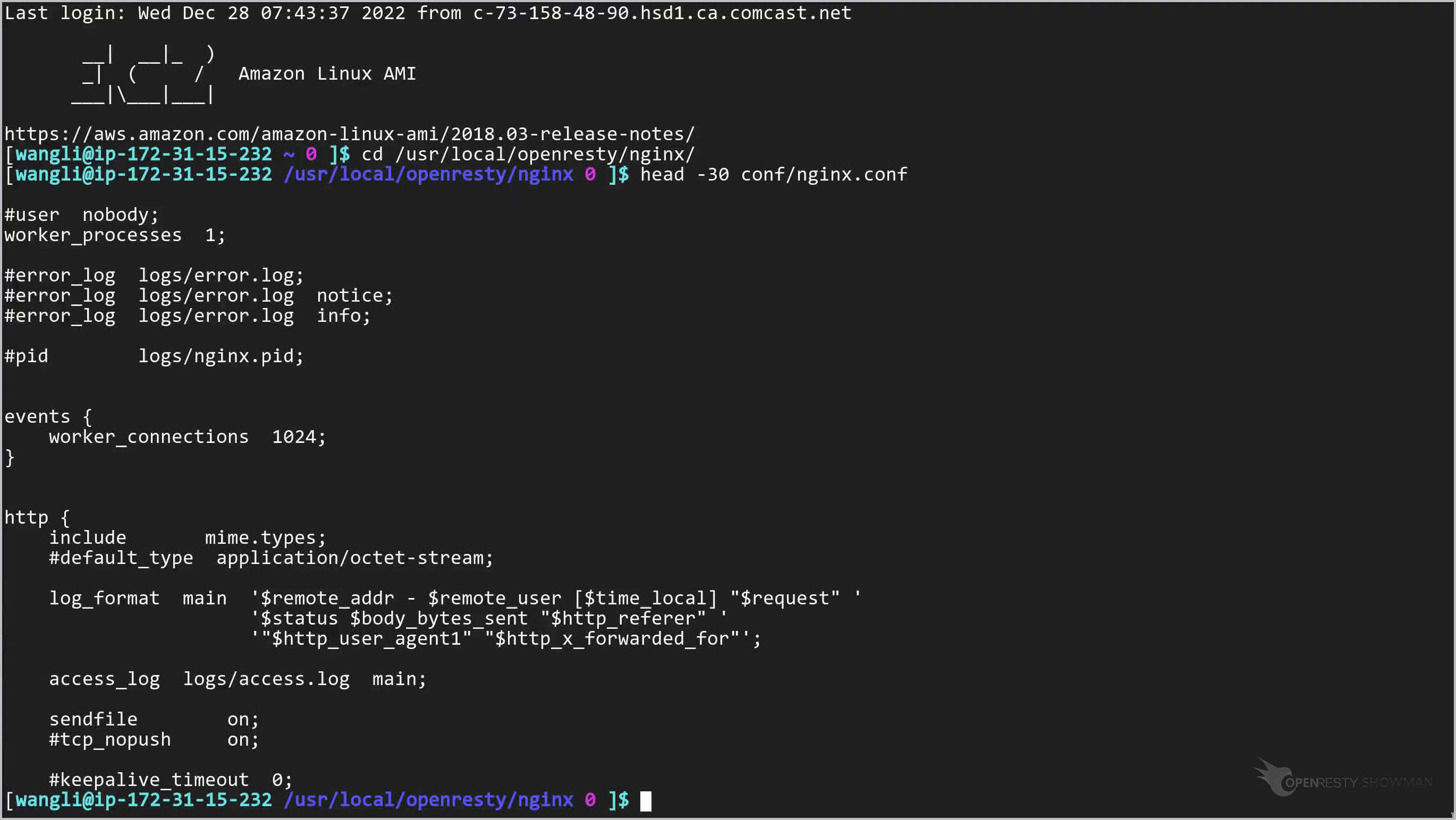
Show the top 30 lines of the Nginx configuration file.
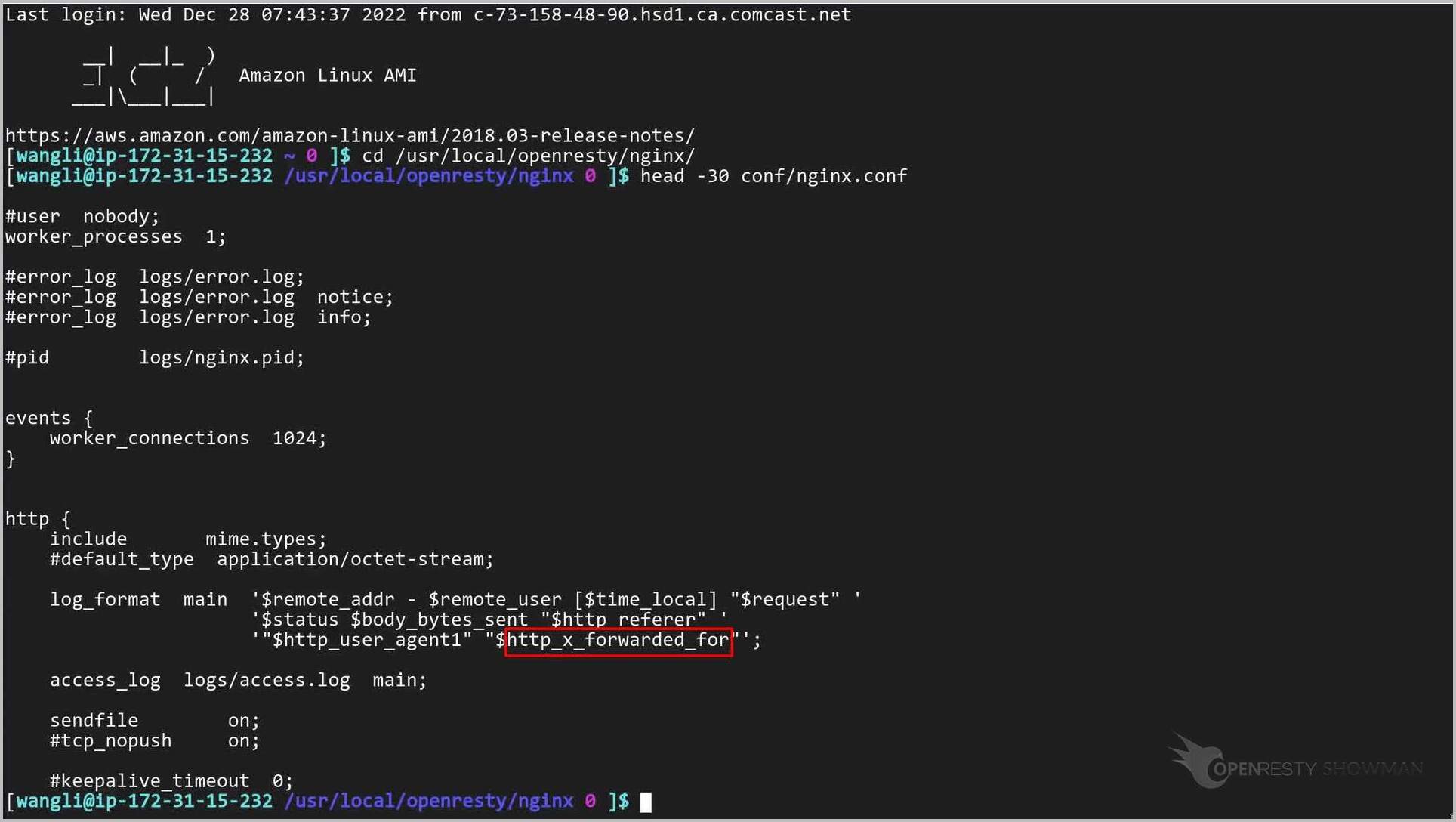
Find the log_format directive.
Note that the “X-Forwarded-For” header value is the last field in an access log message.
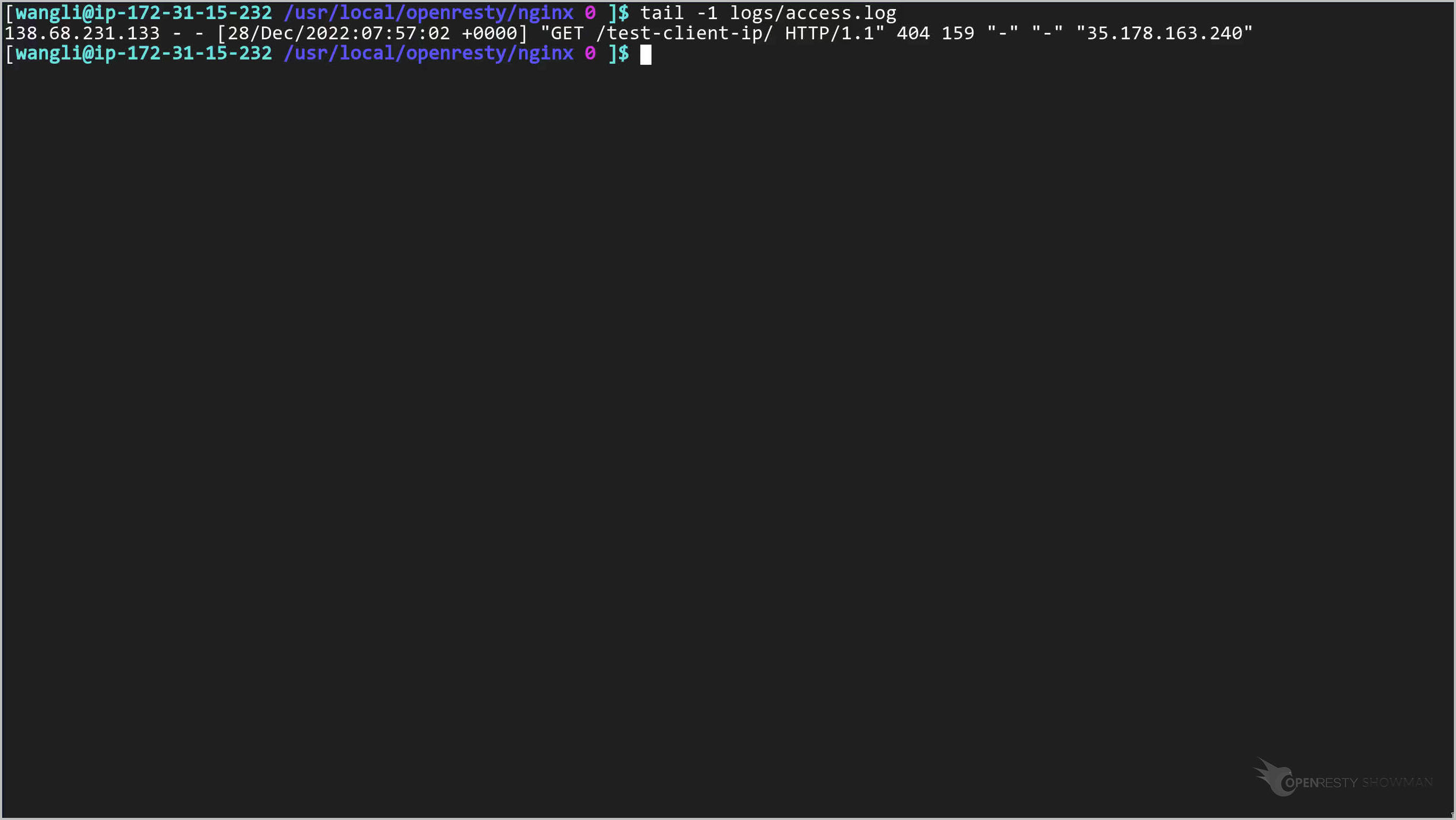
Check the last line in the backend server’s access log file.
clear
tail -1 logs/access.log
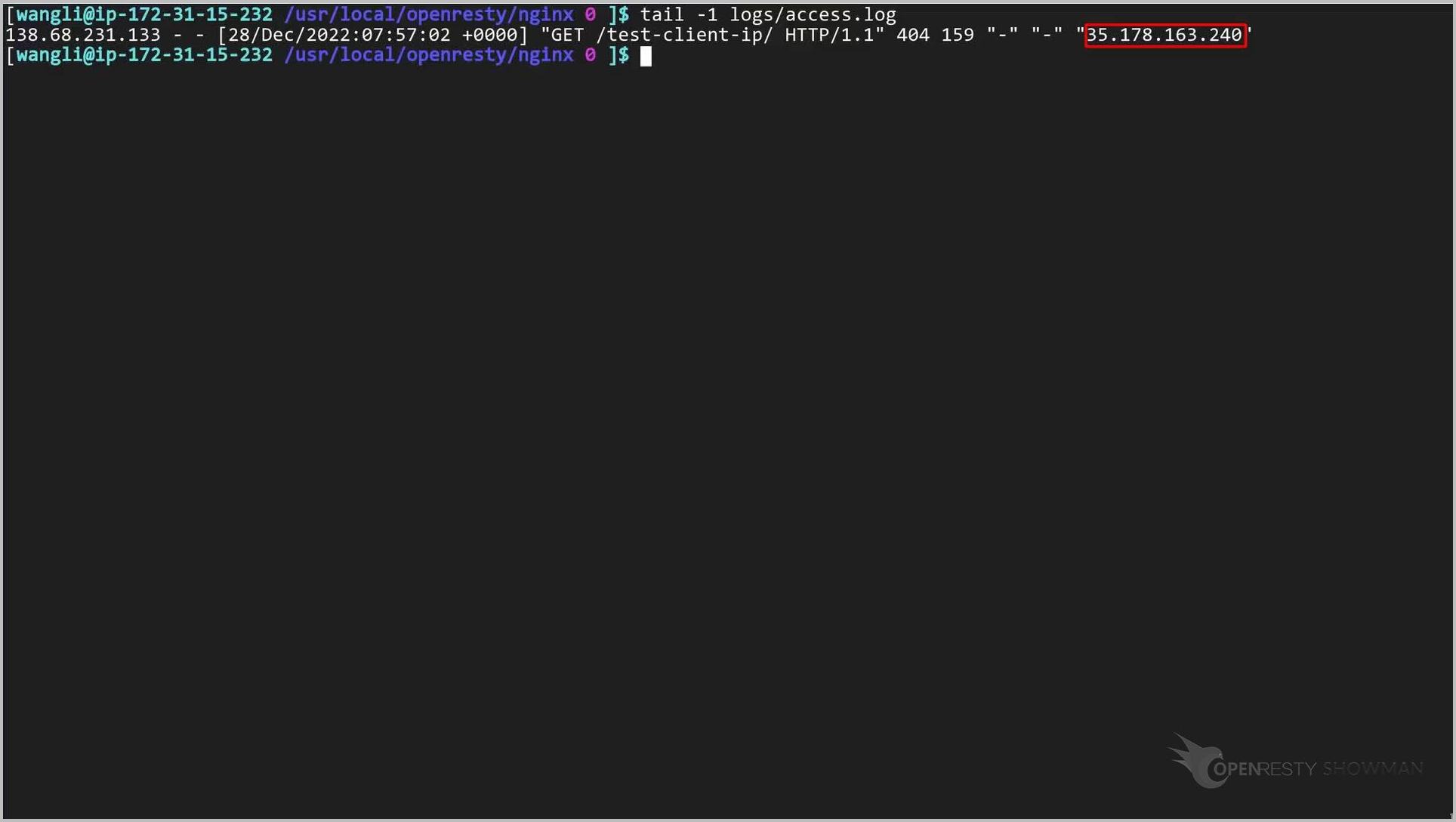
The X-Forwarded-For header of the forwarded request is indeed the IP address ending with .240.
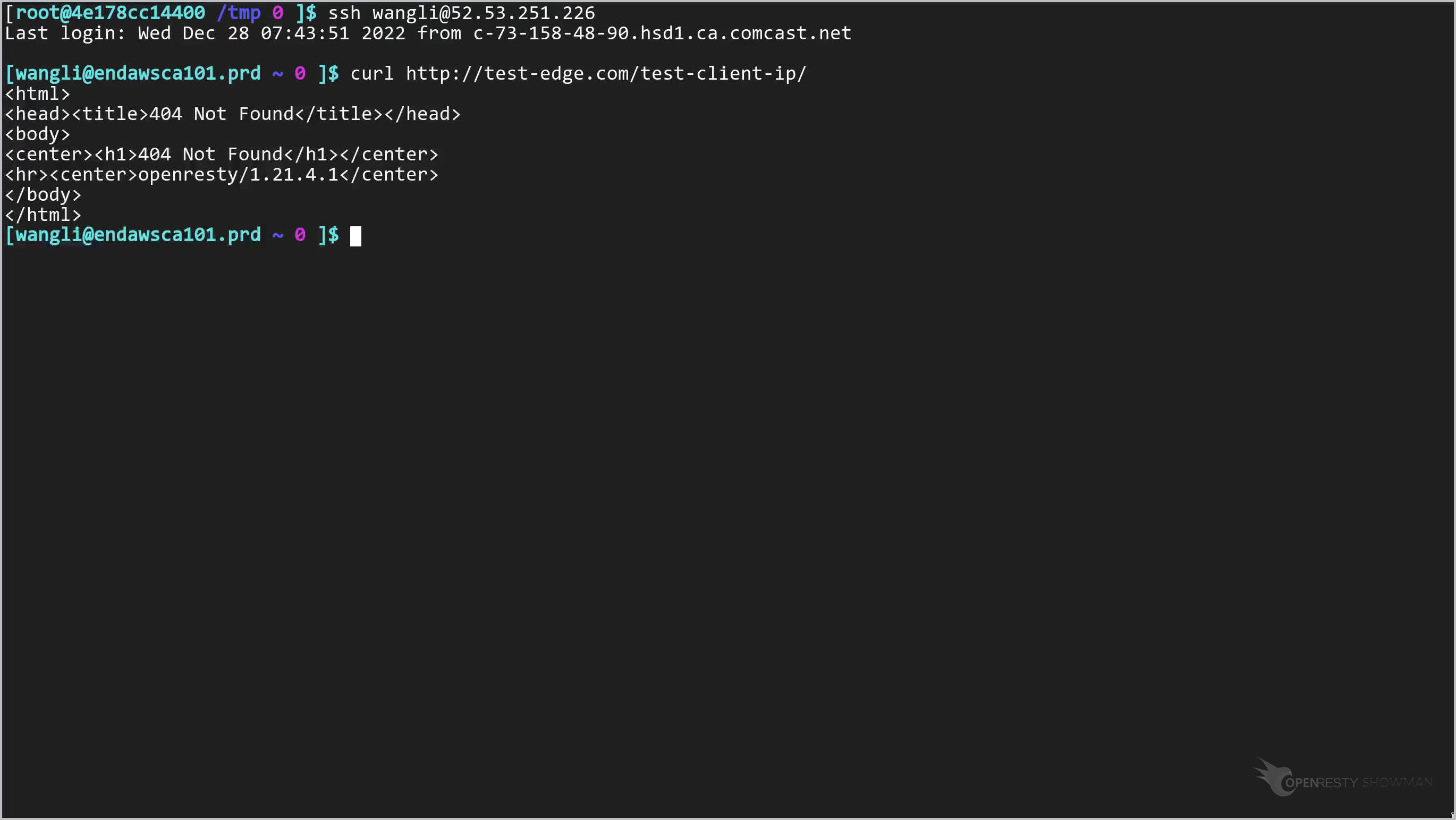
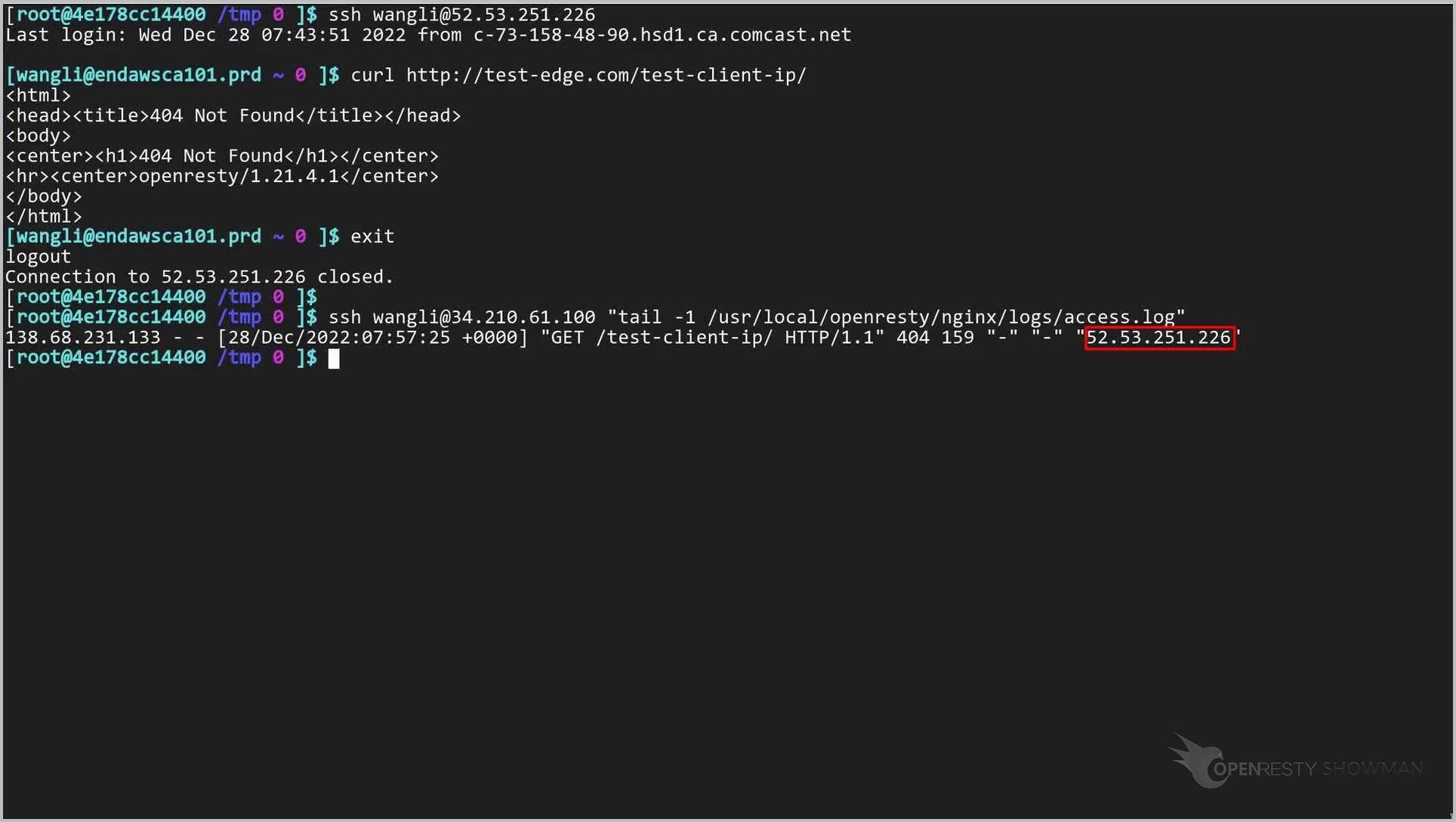
We log onto another server in San Francisco, USA.
Note the IP address of the server ends of .226.
Log onto the server.
Send a test request.
curl http://test-edge.com/test-client-ip/
So the real client IP for this request should end with .226 as well.
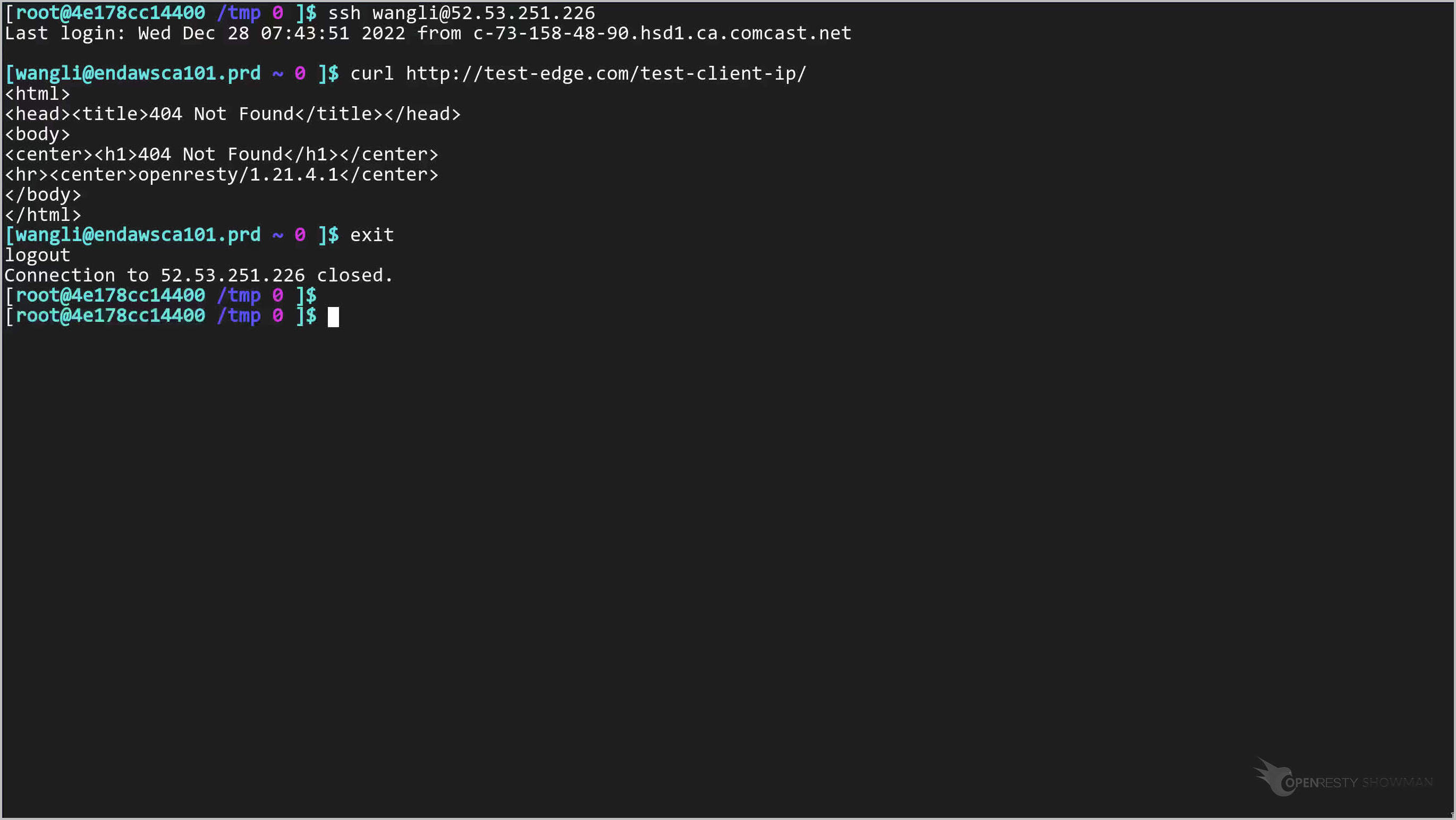
Exit the server.
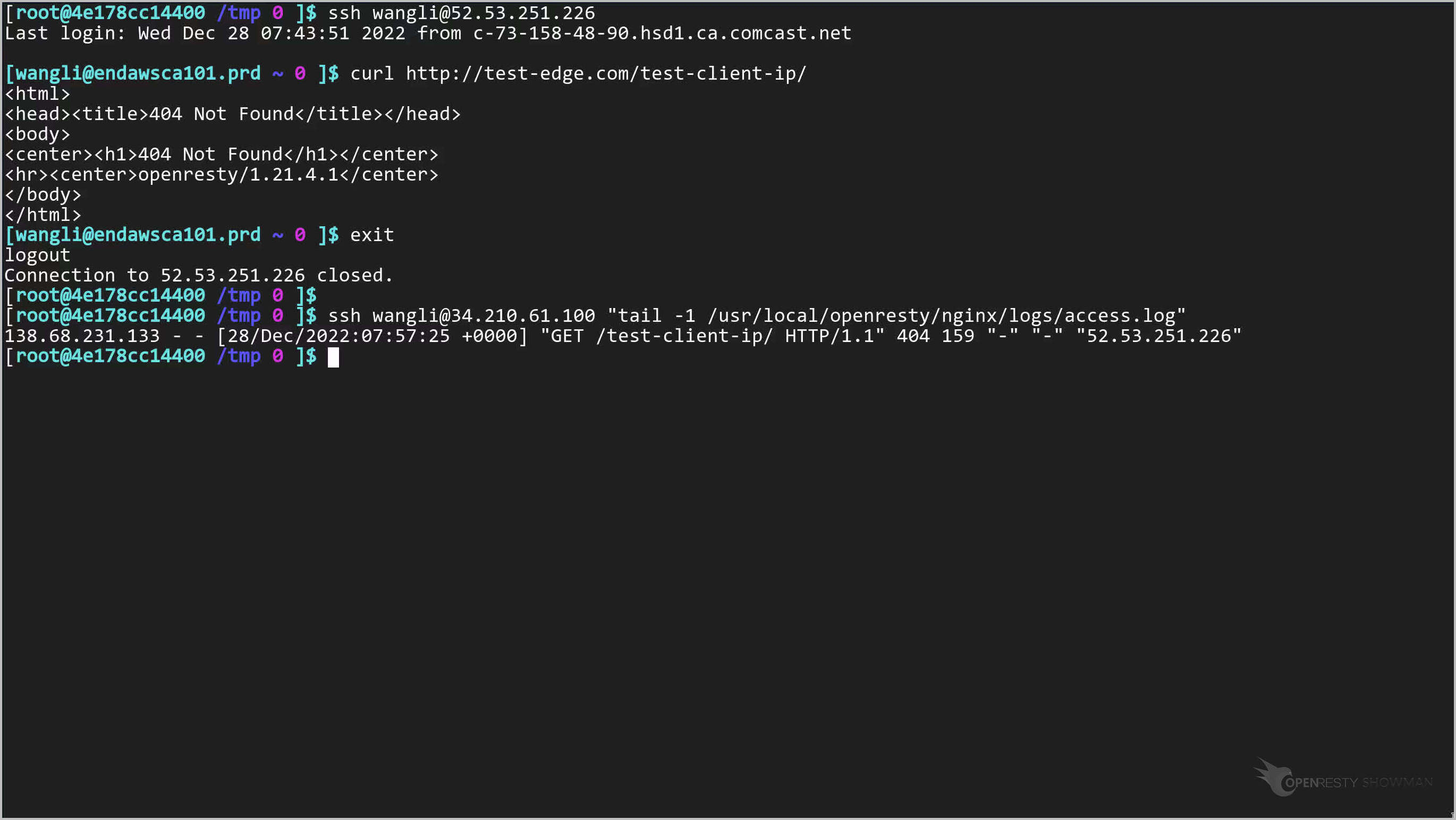
Check the last line in the backend servers access log file.
The X-Forwarded-For header of the forwarded request ends with 226, exactly what we’d expect.
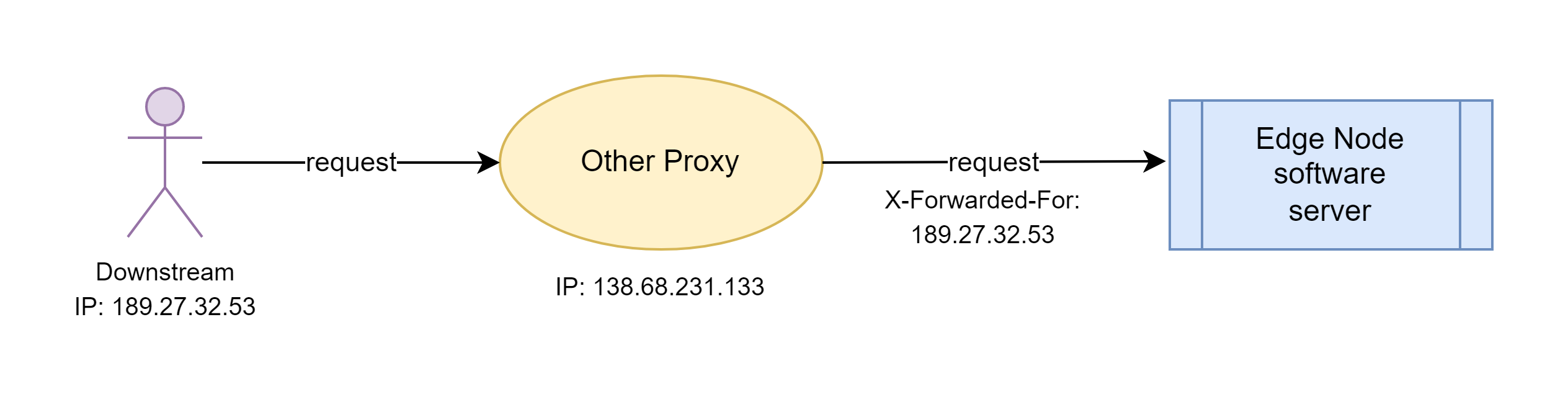
Sometimes, the OpenResty Edge gateway servers themselves may be behind another proxy. In such cases, OpenResty Edge also need to read real client IP addresses from some special request headers. We covers this topic in another tutorial.
What is OpenResty Edge
OpenResty Edge is our all-in-one gateway software for microservices and distributed traffic architectures. It combines traffic management, private CDN construction, API gateway, security, and more to help you easily build, manage, and protect modern applications. OpenResty Edge delivers industry-leading performance and scalability to meet the demanding needs of high concurrency, high load scenarios. It supports scheduling containerized application traffic such as K8s and manages massive domains, making it easy to meet the needs of large websites and complex applications.
If you like this tutorial, please subscribe to this blog site and/or our YouTube channel. Thank you!
About The Author
Yichun Zhang (Github handle: agentzh), is the original creator of the OpenResty® open-source project and the CEO of OpenResty Inc..
Yichun is one of the earliest advocates and leaders of “open-source technology”. He worked at many internationally renowned tech companies, such as Cloudflare, Yahoo!. He is a pioneer of “edge computing”, “dynamic tracing” and “machine coding”, with over 22 years of programming and 16 years of open source experience. Yichun is well-known in the open-source space as the project leader of OpenResty®, adopted by more than 40 million global website domains.
OpenResty Inc., the enterprise software start-up founded by Yichun in 2017, has customers from some of the biggest companies in the world. Its flagship product, OpenResty XRay, is a non-invasive profiling and troubleshooting tool that significantly enhances and utilizes dynamic tracing technology. And its OpenResty Edge product is a powerful distributed traffic management and private CDN software product.
As an avid open-source contributor, Yichun has contributed more than a million lines of code to numerous open-source projects, including Linux kernel, Nginx, LuaJIT, GDB, SystemTap, LLVM, Perl, etc. He has also authored more than 60 open-source software libraries.